We provide 1Y0-240 Braindumps which are the best for clearing 1Y0-240 test, and to get certified by Citrix Citrix NetScaler 12 Essentials and Traffic Management. The 1Y0-240 Dumps covers all the knowledge points of the real 1Y0-240 exam. Crack your Citrix 1Y0-240 Exam with latest dumps, guaranteed!
Free demo questions for Citrix 1Y0-240 Exam Dumps Below:
NEW QUESTION 1
After being audited, a Citrix Administrator was notified that additional enhancements should be made of the virtual servers.
Which two options can the administrator take to make the additional enhancements? (Choose two.)
- A. Enable RC4 cipher suite
- B. Create SHA1 key
- C. Enable TLSv1.2
- D. Disable SSLv3
Answer: BC
NEW QUESTION 2
Scenario: A Citrix Administrator has configured the following Access Control List (ACL) to block traffic from the IP address 10.102.29.5.
add simpleacl rule1 DENY –srcIP 10.102.29.5
A week later, the administrator found that the ACL is no longer present on the NetScaler. What could be the reason for this?
- A. The administrator did NOT run the apply ACL command.
- B. The NetScaler has been restarted without saving the configurations.
- C. The Simple ACLs remain active for only 600 seconds.
- D. The Simple ACLs remain active for only 60 seconds.
Answer: A
NEW QUESTION 3
Scenario: A Citrix Administrator is concerned about the amount of health checks the NetScaler is sending to the backend resources. The administrator would like to find a way to remove health checks from specific bound services.
How can the administrator accomplish this?
- A. Use the No-Monitor option.
- B. Use Service Groups to minimize health checks.
- C. Unbind the current monitor.
- D. Use reverse condition monitoring.
Answer: A
NEW QUESTION 4
What is the effect of the set gslb parameter – IdnsprobeOrder DNS PING TCP command in an Active/Active Global Server Load Balancing (GSLB) setup?
- A. The order to calculate the Empty Domain Service (EDS) for Dynamic proximity will be the DNS UDP query followed by the PING and then TCP.
- B. The order to calculate the Round-trip time (RTT) for Dynamic proximity will be the DNS UDP query followed by the PING and then TCP.
- C. The order to calculate the Time to live (TTL) proximity will be the DNS UDP query followed by the PING and then TCP.
- D. The order to calculate the Multiple IP responses (MIR) for Dynamic proximity will be the DNS UDP query followed by the PING and then TCP.
Answer: C
NEW QUESTION 5
Scenario: A Citrix Administrator has configured an Authentication, Authorization, and Auditing (AAA) action policy to allow users access through the NetScaler. The administrator bound the policy to a specific virtual server.
Which policy expression will allow all users access through the virtual server?
- A. ns_disallow
- B. ns_false
- C. ns_allow
- D. ns_true
Answer: C
NEW QUESTION 6
Which NetScaler mode is commonly referred to as ‘inline mode’?
- A. One-Arm Mode
- B. MAC-based Forwarding
- C. Two-Arm Mode
- D. Use Source IP (USIP)
Answer: C
NEW QUESTION 7
POLICY 1:
add rewrite action ACT_1 corrupt_http_header Accept-Encoding add rewrite policy POL_1 HTTP.REQ.IS_VALID ACT_1
POLICY 2:
add rewrite action ACT_2 insert_http_header Accept-Encoding “”identity”” add rewrite policy POL_2 “HTTP.REQ.IS_VALID” ACT_2
How can a Citrix Administrator bind the rewrite policies to the LB vserver lb_vsrv such that POL_2 is evaluated after POL_1 is evaluated successfully?
- A. bind lb vserver lb_vsrv –policyName POL_1 –priority 110 –gotoPriorityExpression NEXT–type REQUESTbind lb vserver lb_vsrv –policyName POL_2 –priority 100–gotoPriorityExpression END –type REQUEST
- B. bind lb vserver lb_vsrv –policyName POL_1 –priority 90 –type REQUESTbind lb vserver lb_vsrv –policyName POL_2 –priority 100 –type REQUEST
- C. bind lb vserver lb_vsrv –policyName POL_1 –priority 90 –gotoPriorityExpression NEXT–type REQUESTbind lb vserver lb_vsrv –policyName POL_2 –priority 100–gotoPriorityExpression END –type REQUEST
- D. bind lb vserver lb_vsrv –policyName POL_1 –priority 90 –gotoPriorityExpression END–type REQUEST bind lb vserver lb_vsrv –policyName POL_2 –priority 80–gotoPriorityExpression NEXT –type REQUEST
Answer: C
NEW QUESTION 8
A Citrix Administrator wants to configure independent and isolated access on a single appliance for three different departments to allow them to manage and isolate their own applications.
How can the administrator isolate department-level administration?
- A. Configure dedicated routes in the admin partitions for each department.
- B. Configure Policy-based Routes for each department in the nsroot partition.
- C. Configure admin partitions that use dedicated VLANs.
- D. Configure a SNIP in each partition and bind a VLAN for the department.
Answer: B
NEW QUESTION 9
Scenario: A NetScaler is configured with the following modes:
A Citrix Administrator configured a new router and now requires some of the incoming and outgoing traffic to take different paths through the new router. However, the administrator notices that this is failing and takes a network trace. After a short monitoring period, the administrator notices that the packets are still NOT getting to the new router from the NetScaler.
Which mode should the administrator disable on the NetScaler to facilitate the addition of the new router and successfully route the packets?
- A. Layer 3 mode
- B. USIP
- C. MAC-based Forwarding
- D. USNIP
Answer: B
NEW QUESTION 10
View the Exhibit.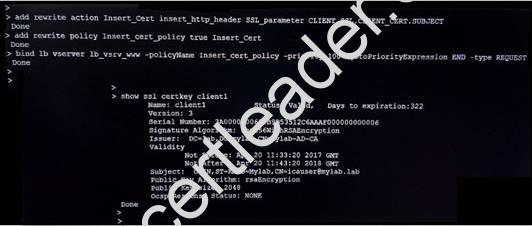
A Citrix Administrator has configured the commands using the command-line interface. Click on the ‘Exhibit’ button to view the screenshots of the command-line interface. What will be the effect of the rewrite policy, based on the exhibit?
- A. HTTP Header “SSL_parameter: icauser@mylab.lab” will be inserted in every RESPONSE.
- B. HTTP Header “SSL_parameter: icauser@mylab.lab” will be inserted in every REQUEST.
- C. HTTP Header “SSL_parameter: C=IN, ST=KA, O=Mylab, CN=icauser@mylab.lab” will be inserted in every RESPONSE.
- D. HTTP Header “SSL_parameter: C=IN, ST=KA, O=Mylab, CN=icauser@mylab.lab” will be inserted in every REQUEST.
Answer: A
NEW QUESTION 11
Before:
<link rel=”stylesheet” type=”text/css” href=”sheet/abc.css”>
<link rel=”stylesheet” type=”text/css” href=”sheet/xyz.css”>
After:
<link rel=”stylesheet” type=”text/css” href=”sheet/abc.css+ xyz.css”>
Which Front-End Optimization (FEO) action can a Citrix Administrator use to achieve the results above?
- A. Minify CSS
- B. Combine CSS
- C. Inline CSS
- D. Convert linked CSS
Answer: A
NEW QUESTION 12
A Citrix Administrator needs to configure a rate limiting policy for the DNS requests to a threshold of 1000 DNS requests per second.
Which set of commands does the administrator need to run to correctly configure the rate limiting policy?
- A. add stream selector DNSSelector1 client.udp.dns.domainadd ns limitIdentifier DNSLimitIdentifier1 –threshold 5 –timeSlice 1000 –selectorName DNSSelector1add dns policy DNSLimitPolicy1 “sys.check_limit(”DNSLimitIdentifier1”)” –preferredLocation “North America.US.TX.Dallas..”bind dns global DNSLimitPolicy1 5
- B. add stream selector DNSSelector1 client.udp.dns.domainadd ns limitIdentifier DNSLimitIdentifier1 –threshold 5 –timeSlice 1000 –selectorName DNSSelector1add dns policy DNSLimitPolicy1 “sys.check_limit(”DNSLimitIdentifier1”)” –preferredLocation “North America.US.TX.Dallas..”
- C. add stream selector DNSSelector1 client.udp.dns.domainadd ns limitIdentifier DNSLimitIdentifier1 –threshold 1000 –timeSlice 1000 –selectorName DNSSelector1add dns policy DNSLimitPolicy1 “sys.check_limit(”DNSLimitIdentifier1”)” –preferredLocation “North America.US.TX.Dallas..”
- D. add stream selector DNSSelector1 client.udp.dns.domainadd ns limitIdentifier DNSLimitIdentifier1 –threshold 1000 –timeSlice 1000 –selectorName DNSSelector1add dns policy DNSLimitPolicy1 “sys.check_limit(”DNSLimitIdentifier1”)” –preferredLocation “North America.US.TX.Dallas..”bind dns global DNSLimitPolicy1 5
Answer: C
NEW QUESTION 13
Scenario: A Citrix Administrator notices user sessions are disconnecting and reconnecting more often this week than last week, signaling a problem.
The administrator troubleshoots this issue and prepares to resolve it using persistence. However, the following consideration apply in the environment:
The administrator can use persistence based on the ___ setting to resolve this issue. (Choose the correct option to complete the sentence.)
- A. Subnet IP
- B. HTTP Cookies
- C. Proximity
- D. SSL Session IDs
Answer: A
NEW QUESTION 14
Scenario: A Citrix Administrator is executing the following commands on the NetScaler:
add policy dataset Admin_group ipv4
bind policy dataset Admin_group 192.168.149.10 –index 11 bind policy dataset Admin_group 192.168.149.39 –index 12 bind policy dataset Admin_group 192.168.149.49 –index 13 add responder policy POL_1
“!(CLIENT.IP.SRC.TYPECAST_TEXT_T.CONTAINS_ANY(”Admin_group”))” RESET
bind lb vserver ln_vsrv_www –policyName POL_1 –priority 100 –gotoPriorityExpression END –type REQUEST
What will be the effect of these commands?
- A. All the traffic from users with a source IP address of 192.168.149.10, 192.168.149.39, or 192.168.149.49 will be blocked through the NetScaler.
- B. Only the users with a source IP address of 192.168.149.10, 192.168.149.39, or 192.168.149.49 will be allowed to connect to vserver lb_vsrv_www.
- C. Only the users with a source IP address of 192.168.149.10, 192.168.149.39, or 192.168.149.49 will be blocked when attempting to connect to vserver lb_vsrv_www.
- D. Only the users with a source IP address of 192.168.149.10 or 192.168.149.39 will be allowed to connect to the virtual server.
Answer: B
NEW QUESTION 15
View the Exhibit.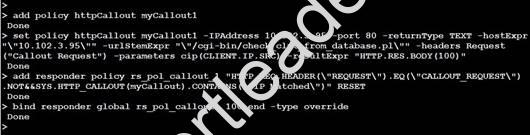
A Citrix Administrator has implemented the HTTP Callout.
Click on the ‘Exhibit’ button to view the screenshot of the command-line interface.
Which part of the configuration is responsible for triggering the call to HTTP Callout server?
- A. –parameters cip(CLIENT.IP.SRC)
- B. sys.http_callout(myCallout1)
- C. –urlStemExpr “”/cgi-bin/check_clnt_from_database.pl”
- D. –headers Request(“Callout Request”)
Answer: D
NEW QUESTION 16
Scenario: A Citrix Administrator would like to grant access to a Junior Administrator on the NetScaler. The administrator would like to grant full access to everything except the following:
Which pre-existing command policy would meet the needs of the scenario?
- A. Superuser
- B. Network
- C. Operator
- D. Sysadmin
Answer: A
100% Valid and Newest Version 1Y0-240 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/1Y0-240-exam-dumps.html (New 122 Q&As)