Your success in Oracle 1z0-888 is our sole target and we develop all our 1z0-888 braindumps in a way that facilitates the attainment of this target. Not only is our 1z0-888 study material the best you can find, it is also the most detailed and the most updated. 1z0-888 Practice Exams for Oracle Oracle Other Exam 1z0-888 are written to the highest standards of technical accuracy.
Free demo questions for Oracle 1z0-888 Exam Dumps Below:
NEW QUESTION 1
Force Majeure is a catastrophic failure on a major level of the database operation. Regular backups are key to helping avoid data loss in such situations.
Which two other steps can help avoid data loss in a major catastrophe?
- A. Implement a failover strategy to another geographic location.
- B. Create a master-master pair for each service.
- C. Have a second data centre in a different region or country.
- D. Keep software updated to the latest version.
- E. Use RAID 10 storage for datA.
- F. Use on-site network-attached storage to separate service from dat
Answer: AC
NEW QUESTION 2
You have the following in your my.cnf configuration file: [mysqld] default_authentication_plugin=sha256_password
You want to create a new user who will be connecting from the IP address 192.0.2.10, and you want to use the authentication plug-in that implements SHA-256 hashing for user account passwords.
Which two statements would create a user named webdesign for this IP address with the password of imbatman using a SHA_256 password hash?
- A. CREATE USER ‘webdesign’@’192.0.2.10’ IDENTIFIED AS sha256_user WITH sha256_password ‘imbatman’;
- B. CREATE USER ‘webdesign’@’192.0.2.10’ IDENTIFIED BY ‘iambatman’;
- C. CREATE USER ‘webdesign’@’192.0.2.10’ IDENTIFIED WITH sha256_password BY ‘imbatman’;
- D. CREATE USER WITH sha256_password ‘sha256_user’@’192.0.2.10’ IDENTIFIED AS ‘webdesign’ USING ‘imbatman’;
- E. CREATE USER ‘webdesign’@’192.0.2.10’ WITH mysql_native_password USING SHA265 BY ‘imbatman’;
- F. CREATE USER ‘webdesign’@’192.0.2.10’ IDENTIFIED BY SHA265 AS ‘imbatman’;
Answer: BF
NEW QUESTION 3
On a master server that is using statement-based replication, a table of log data has become very large. You decide to delete 100.000 rows.
Which two methods can be independently invoked to ensure that the delete is properly propagated to the slave? (Choose two.)
- A. Change the replication mode to mixed before issuing any delete statements when the limit clause is used.
- B. If the data modification is non-deterministic, the query optimizer will resolve any potential issues.
- C. Use the limit clause to limit the deletion to 100.000 rows.
- D. Use the limit clause in conjunction with the order 3Y claus
Answer: AD
NEW QUESTION 4
You back up by using mysqldump.
Which configuration is required on the MySQL Server to allow point-in-time recovery?
- A. binlog_format=STATEMENT
- B. log-bin
- C. apply-log
- D. bonlog_format=ROW
- E. gtid_enable
Answer: B
NEW QUESTION 5
Which three are key advantages of standard MySQL replication?
- A. supports native automatic failover
- B. enables automatic resync of databases when discrepancies are detected
- C. provides arbitrary geographic redundancy with minimal overhead to master
- D. synchronously guarantees identical slave copy
- E. is easy to configure and has low performance overhead
- F. can easily add slaves for read scaling
Answer: BEF
NEW QUESTION 6
Consider these global status variables:
Which two conclusions can be made from the output?
- A. There are 140 Performance Schema threads at the time of the output.
- B. There are 510 connections to MySQL at the time of the output.
- C. The thread cache has been configured with thread_cache_size set to at least 6.
- D. There are more connections being idle than executing queries.
- E. All max_connections were in use at 2021-03-22 14:54:06
Answer: BD
NEW QUESTION 7
One of your colleagues is trying to make a change using the mysql command-line client for his or her application session.
The colleague instant messages you this command: mysql> SET SESSION max_connections = 200; Why does the command fail?
- A. max_connections requires the GLOBAL scope.
- B. Its current user does not have the SUPER privilege.
- C. max_connections is not a dynamic variabl
- D. You need to change the config file and restart the database.
- E. Users can control only the max_user_connections variabl
Answer: A
NEW QUESTION 8
You created a backup of the world database with this command: shell> mysqldump --opt world > dump.sql Which two will import the data from dump.sql?
- A. shell> mysqladmin recover test dump.sql
- B. shell> mysql test < dump.sql
- C. shell> mysqlimport test dump.sql
- D. mysql> USE test; mysql> LOAD DATA INFILE ‘dump.sql’;
- E. mysql>USE test; mysql>SOURCE dump.sql;
Answer: CD
NEW QUESTION 9
Which two statements are true about InnoDB auto-increment locking?
- A. InnoDB never uses table_level locks.
- B. InnoDB always protects auto-increment updates with a table-level lock
- C. InnoDB does not use locks to enforce auto-increment uniqueness.
- D. The auto-increment lock can be a table-level lock.
- E. Some settings for innodb_autoinc_lock_mode can help reduce lockin
Answer: DE
NEW QUESTION 10
To satisfy a security requirement, you have created or altered some user accounts to include REQUIRE X509.
Which additional task needs to be performed for those user accounts to fulfill the requirement to use X509?
- A. Install the X509 plug-in on the server.
- B. Set the X509 option in the [client] section of the MySQL server’s configuration file.
- C. Restart the server with the --require-x509 option.
- D. Distribute client digital certificates to the client computers being used to log in by the user accounts.
- E. Provide users access to the server’s private ke
Answer: B
NEW QUESTION 11
MySQL is installed on a Linux server and has this configuration:
[mysqld] user=mysql
datadir=/data/mysql/
As the ‘root’ user, you change the datadir location by executing:
shell> cp –R /var/lib/mysql /data/mysql/ shell> chown –R mysql /data/mysql
What is the purpose of changing ownership of datadir to the ‘mysql’ user?
- A. MySQL needs to be run as the root user, but files cannot be owned by it.
- B. The mysqld process requires all permissions within datadir to be the same.
- C. MySQL cannot be run as the root user.
- D. MySQL requires correct file ownership while remaining secur
Answer: A
NEW QUESTION 12
You are contacted by a user who does not have permission to access a database table. You determine after investigation that this user should be permitted to have access and so you execute a GRANT statement to enable the user to access the table.
Which statement describes the activation of that access for the user?
- A. The access does not take effect until the user logs out and back in.
- B. The access does not take effect until the next time the server is started.
- C. The access is available immediately.
- D. The access does not take effect until you issue the FLUSH PRIVILEGES statemen
Answer: C
NEW QUESTION 13
A MySQL Server has been running an existing application successfully for six months. The my.cnf is adjusted to contain this additional configuration: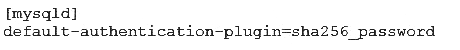
The MySQL Server is restarted without error.
What effect will the new configuration have on existing account?
- A. They are not affected by this configuration change.
- B. They all connect via the secure sha256_password algorithm without any configuration change.
- C. They will have their passwords updated on start-up to sha256_password format.
- D. They will have to change their password the next time they login to the serve
Answer: A
NEW QUESTION 14
The /myfolder/my.cnf file has option set: [mysqld] skip-log-bin
/myfolder2/my.cnf has this option set: [mysqld] log-bin = /valid/path/to/mysqlbinlog
All mentioned paths are accessible to the account that you are currently using. Assume that any other options mentioned in either file are valid and legal option definitions.
You start an instance by using this command line:
mysqld --defaults-file=/myfolder/my.cnf --defaults-extra-file=/myfolder2/my.cnf What is the outcome?
- A. MySQL starts and Binary Logging is enabled.
- B. MySQL fails to start due to the conflicting options in the configuration files.
- C. MySQL fails to start due to conflicting options on the command line.
- D. MySQL starts but Binary Logging is disable
Answer: C
NEW QUESTION 15
What two statements are true regarding FLUSH TABLES FOR EXPORT?
- A. It can be used to export TEMPORARY tables.
- B. Table only exports when the table has its own tablespace.
- C. The InnoDB Storage engine must be used for the table being exported.
- D. It is the safest way to extract tables from the shared tablespace.
- E. Partitioned tables are not supporte
Answer: AB
NEW QUESTION 16
You are no longer able to log in to an existing MySQL Server because the root password credentials not
working. You need to reset the root password to complete various administrative tasks. What are the two major methods that will achieve this?
- A. Start the MySQL Server in --safe-mode, which only loads the privilege system for changes as data is inaccessible.
- B. Start the MySQL Server with reset-root-password in my.cnf, which will prompt you to enter a new root user password.
- C. Start the MySQL Server with --init-file pointing to SQL that executes an ALTER USER statement to change the root user password.
- D. Start the MySQL Server with --skip-grant-tables and execute SQL, which will update the root password.
- E. Start the MySQL Server with –initialize-insecure to force a password reset procedure on the command lin
Answer: CD
NEW QUESTION 17
An admin attempts to enforce stronger security by using these commands: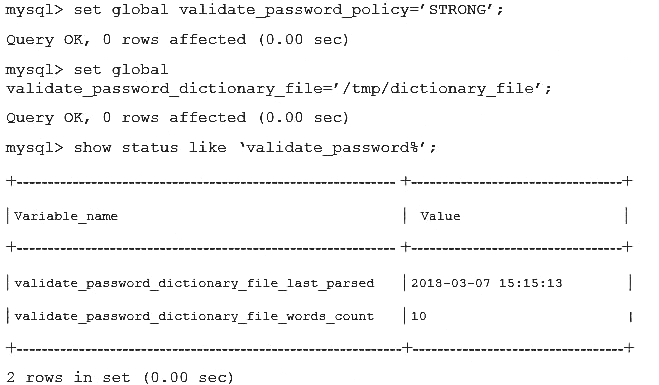
The admin then leaves the system running with the specified changes. What are two remaining security concerns?
- A. validate_password_policy cannot be set without restarting the MySQL instance.
- B. The name of the dictionary file is too obvious.
- C. The dictionary file word list is too short.
- D. validate_password_dictionary_file cannot be set without restarting the MySQL instance.
- E. The validate_password plug-in has not been loaded.
- F. The dictionary file is an insecure locatio
Answer: BF
NEW QUESTION 18
Consider that local disk files are accessible via MySQL with commands such as: mysql> LOAD DATA LOCAL INFILE ‘/etc/passwd’ INTO TABLE mypasswords; What change could be made to stop any breach via this insecurity?
- A. executing REVOKE LOADFROM *.*
- B. setting the --local-service=0 option when starting mysqld
- C. executing REVOKEFILEFROM *_*
- D. executing REVOKEFILE ON *_* FROM ‘ ‘@’%’
- E. setting the --local-infile=0 option when starting mysqld
- F. setting the --open-files-limit=0 option when starting mysqld
Answer: F
NEW QUESTION 19
Which two statements describe how InnoDB recovery works?
- A. InnoDB handles most crash recoveries automatically.
- B. InnoDB blocks some operations when innodb_force_recovery is set to greater than 0.
- C. There will in general be lost committed transactions after a crash using the default settings.
- D. It is required to enable binlog_gtid_simple_recovery to perform a crash recovery.
- E. It is recommended to set innodb_force_recovery = 1 as part of normal operations.
- F. It is always required to enable innodb_force_recovery to perform a crash recover
Answer: BF
NEW QUESTION 20
Consider the two partial outputs of the SHOW GLOBAL VARIABLES command from a master and slave server: Master:
Slave: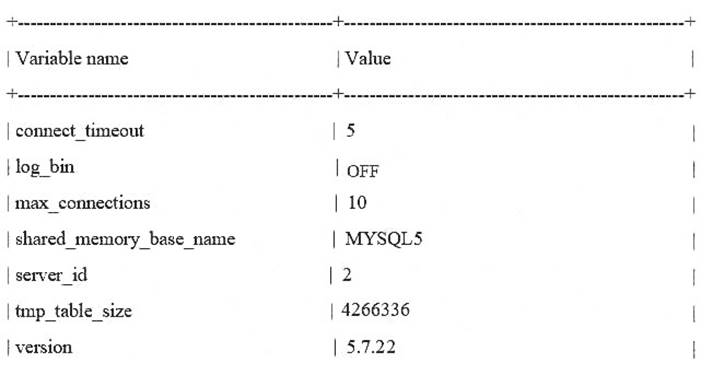
There is a problem with the slave replicating from the master. Which statement describes the cause of the problem?
- A. The log_bin variable is set to OFF on the slave.
- B. server_id is not unique.
- C. The max_connections variable on the slave needs to be increased.
- D. The shared_memory_base_name variable must match the master.
- E. The version of the slave is newer that the version of the maste
Answer: A
NEW QUESTION 21
You have a MySQL replication setup and you intentionally stop the SQL thread on the slave.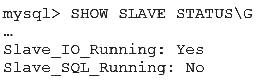
What are two reasons that you may stop the SQL thread on the slave while keeping the I/O thread running?
- A. to allow the remaining events to be processed on the slave while not receiving new events from the master
- B. to allow a backup to be created under reduced load
- C. to allow for point-in-time recovery on the slave
- D. to prevent schema changes from propagating to the slave before they are validated
- E. to prevent any transaction experiencing a deadlock
Answer: BC
NEW QUESTION 22
......
P.S. Easily pass 1z0-888 Exam with 84 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam 1z0-888 Dumps: https://www.surepassexam.com/1z0-888-exam-dumps.html (84 New Questions)