Master the 312-50v11 Certified Ethical Hacker Exam (CEH v11) content and be ready for exam day success quickly with this Ucertify 312-50v11 test preparation. We guarantee it!We make it a reality and give you real 312-50v11 questions in our EC-Council 312-50v11 braindumps.Latest 100% VALID EC-Council 312-50v11 Exam Questions Dumps at below page. You can use our EC-Council 312-50v11 braindumps and pass your exam.
Online 312-50v11 free questions and answers of New Version:
NEW QUESTION 1
What does the following command in netcat do? nc -l -u -p55555 < /etc/passwd
- A. logs the incoming connections to /etc/passwd file
- B. loads the /etc/passwd file to the UDP port 55555
- C. grabs the /etc/passwd file when connected to UDP port 55555
- D. deletes the /etc/passwd file when connected to the UDP port 55555
Answer: C
NEW QUESTION 2
You are the Network Admin, and you get a complaint that some of the websites are no longer accessible. You try to ping the servers and find them to be reachable. Then you type the IP address and then you try on the browser, and find it to be accessible. But they are not accessible when you try using the URL.
What may be the problem?
- A. Traffic is Blocked on UDP Port 53
- B. Traffic is Blocked on TCP Port 80
- C. Traffic is Blocked on TCP Port 54
- D. Traffic is Blocked on UDP Port 80
Answer: A
NEW QUESTION 3
Study the following log extract and identify the attack.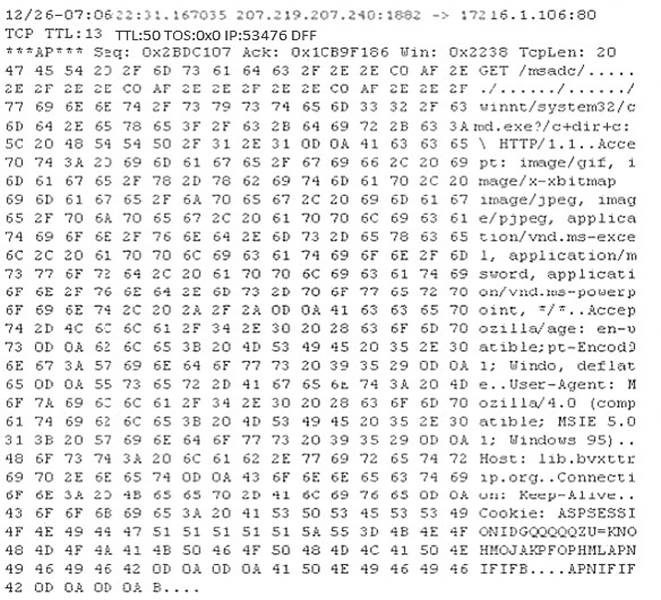
- A. Hexcode Attack
- B. Cross Site Scripting
- C. Multiple Domain Traversal Attack
- D. Unicode Directory Traversal Attack
Answer: D
NEW QUESTION 4
Study the snort rule given below and interpret the rule. alert tcp any any --> 192.168.1.0/24 111 (content:"|00 01 86 a5|"; msG. "mountd access";)
- A. An alert is generated when a TCP packet is generated from any IP on the 192.168.1.0 subnet and destined to any IP on port 111
- B. An alert is generated when any packet other than a TCP packet is seen on the network and destined for the 192.168.1.0 subnet
- C. An alert is generated when a TCP packet is originated from port 111 of any IP address to the 192.168.1.0 subnet
- D. An alert is generated when a TCP packet originating from any IP address is seen on the network and destined for any IP address on the 192.168.1.0 subnet on port 111
Answer: D
NEW QUESTION 5
Joseph was the Web site administrator for the Mason Insurance in New York, who's main Web site was located at www.masonins.com. Joseph uses his laptop computer regularly to administer the Web site. One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance web site had been vandalized! All of its normal content was removed and replaced with an attacker's message ''Hacker Message: You are dead! Freaks!” From his office, which was directly connected to Mason Insurance's internal network, Joseph surfed to the Web site using his laptop. In his browser, the Web site looked completely intact.
No changes were apparent. Joseph called a friend of his at his home to help troubleshoot the problem. The Web site appeared defaced when his friend visited using his DSL connection. So, while Smith and his friend could see the defaced page, Joseph saw the intact Mason Insurance web site. To help make sense of this problem, Joseph decided to access the Web site using hisdial-up ISP. He disconnected his laptop from the corporate internal network and used his modem to dial up the same ISP used by Smith. After his modem connected, he quickly typed www.masonins.com in his browser to reveal the following web page:
After seeing the defaced Web site, he disconnected his dial-up line, reconnected to the internal network, and used Secure Shell (SSH) to log in directly to the Web server. He ran Tripwire against the entire Web site, and determined that every system file and all the Web content on the server were intact. How did the attacker accomplish this hack?
- A. ARP spoofing
- B. SQL injection
- C. DNS poisoning
- D. Routing table injection
Answer: C
NEW QUESTION 6
Which of the following statements about a zone transfer is correct? (Choose three.)
- A. A zone transfer is accomplished with the DNS
- B. A zone transfer is accomplished with the nslookup service
- C. A zone transfer passes all zone information that a DNS server maintains
- D. A zone transfer passes all zone information that a nslookup server maintains
- E. A zone transfer can be prevented by blocking all inbound TCP port 53 connections
- F. Zone transfers cannot occur on the Internet
Answer: ACE
NEW QUESTION 7
The network team has well-established procedures to follow for creating new rules on the firewall. This includes having approval from a manager prior to implementing any new rules. While reviewing the firewall configuration, you notice a recently implemented rule but cannot locate manager approval for it. What would be a good step to have in the procedures for a situation like this?
- A. Have the network team document the reason why the rule was implemented without prior manager approval.
- B. Monitor all traffic using the firewall rule until a manager can approve it.
- C. Do not roll back the firewall rule as the business may be relying upon it, but try to get manager approval as soon as possible.
- D. Immediately roll back the firewall rule until a manager can approve it
Answer: D
NEW QUESTION 8
Which service in a PKI will vouch for the identity of an individual or company?
- A. KDC
- B. CR
- C. CBC
- D. CA
Answer: D
NEW QUESTION 9
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
- A. USER, NICK
- B. LOGIN, NICK
- C. USER, PASS
- D. LOGIN, USER
Answer: A
NEW QUESTION 10
Within the context of Computer Security, which of the following statements describes Social Engineering best?
- A. Social Engineering is the act of publicly disclosing information
- B. Social Engineering is the means put in place by human resource to perform time accounting
- C. Social Engineering is the act of getting needed information from a person rather than breaking into a system
- D. Social Engineering is a training program within sociology studies
Answer: C
NEW QUESTION 11
Which of the following is the best countermeasure to encrypting ransomwares?
- A. Use multiple antivirus softwares
- B. Pay a ransom
- C. Keep some generation of off-line backup
- D. Analyze the ransomware to get decryption key of encrypted data
Answer: C
NEW QUESTION 12
An attacker runs netcat tool to transfer a secret file between two hosts.
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?
- A. Machine A: netcat -l -p -s password 1234 < testfileMachine B: netcat <machine A IP> 1234
- B. Machine A: netcat -l -e magickey -p 1234 < testfileMachine B: netcat <machine A IP> 1234
- C. Machine A: netcat -l -p 1234 < testfile -pw passwordMachine B: netcat <machine A IP> 1234 -pw password
- D. Use cryptcat instead of netcat
Answer: D
NEW QUESTION 13
Log monitoring tools performing behavioral analysis have alerted several suspicious logins on a Linux server occurring during non-business hours. After further examination of all login activities, it is noticed that none of the logins have occurred during typical work hours. A Linux administrator who is investigating this problem realizes the system time on the Linux server is wrong by more than twelve hours. What protocol used on Linux servers to synchronize the time has stopped working?
- A. Time Keeper
- B. NTP
- C. PPP
- D. OSPP
Answer: B
NEW QUESTION 14
One of your team members has asked you to analyze the following SOA record.
What is the TTL? Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.)
- A. 200303028
- B. 3600
- C. 604800
- D. 2400
- E. 60
- F. 4800
Answer: D
NEW QUESTION 15
These hackers have limited or no training and know how to use only basic techniques or tools. What kind of hackers are we talking about?
- A. Black-Hat Hackers A
- B. Script Kiddies
- C. White-Hat Hackers
- D. Gray-Hat Hacker
Answer: C
NEW QUESTION 16
What is the known plaintext attack used against DES which gives the result that encrypting plaintext with one DES key followed by encrypting it with a second DES key is no more secure than using a single key?
- A. Man-in-the-middle attack
- B. Meet-in-the-middle attack
- C. Replay attack
- D. Traffic analysis attack
Answer: B
NEW QUESTION 17
What is the role of test automation in security testing?
- A. It is an option but it tends to be very expensive.
- B. It should be used exclusivel
- C. Manual testing is outdated because of low speed and possible test setup inconsistencies.
- D. Test automation is not usable in security due to the complexity of the tests.
- E. It can accelerate benchmark tests and repeat them with a consistent test setu
- F. But it cannot replace manual testing completely.
Answer: D
NEW QUESTION 18
What ports should be blocked on the firewall to prevent NetBIOS traffic from not coming through the firewall if your network is comprised of Windows NT, 2000, and XP?
- A. 110
- B. 135
- C. 139
- D. 161
- E. 445
- F. 1024
Answer: BCE
NEW QUESTION 19
What is the way to decide how a packet will move from an untrusted outside host to a protected inside that is behind a firewall, which permits the hacker to determine which ports are open and if the packets can pass through the packet-filtering of the firewall?
- A. Session hijacking
- B. Firewalking
- C. Man-in-the middle attack
- D. Network sniffing
Answer: B
NEW QUESTION 20
Which type of security feature stops vehicles from crashing through the doors of a building?
- A. Bollards
- B. Receptionist
- C. Mantrap
- D. Turnstile
Answer: A
NEW QUESTION 21
Which of the following is not a Bluetooth attack?
- A. Bluedriving
- B. Bluesmacking
- C. Bluejacking
- D. Bluesnarfing
Answer: A
NEW QUESTION 22
Vlady works in a fishing company where the majority of the employees have very little understanding of IT let alone IT Security. Several information security issues that Vlady often found includes, employees sharing password, writing his/her password on a post it note and stick it to his/her desk, leaving the computer unlocked, didn’t log out from emails or other social media accounts, and etc.
After discussing with his boss, Vlady decided to make some changes to improve the security environment in his company. The first thing that Vlady wanted to do is to make the employees understand the importance of keeping confidential information, such as password, a secret and they should not share it with other persons.
Which of the following steps should be the first thing that Vlady should do to make the employees in his company understand to importance of keeping confidential information a secret?
- A. Warning to those who write password on a post it note and put it on his/her desk
- B. Developing a strict information security policy
- C. Information security awareness training
- D. Conducting a one to one discussion with the other employees about the importance of information security
Answer: A
NEW QUESTION 23
......
P.S. Surepassexam now are offering 100% pass ensure 312-50v11 dumps! All 312-50v11 exam questions have been updated with correct answers: https://www.surepassexam.com/312-50v11-exam-dumps.html (254 New Questions)