Proper study guides for Replace EC-Council Certified Ethical Hacker Exam (CEHv12) certified begins with EC-Council 312-50v12 preparation products which designed to deliver the Free 312-50v12 questions by making you pass the 312-50v12 test at your first time. Try the free 312-50v12 demo right now.
EC-Council 312-50v12 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Clark is a professional hacker. He created and configured multiple domains pointing to the same host to switch quickly between the domains and avoid detection. Identify the behavior of the adversary In the above scenario.
- A. use of command-line interface
- B. Data staging
- C. Unspecified proxy activities
- D. Use of DNS tunneling
Answer: C
Explanation:
A proxy server acts as a gateway between you and therefore the internet. It’s an intermediary server separating end users from the websites they browse. Proxy servers provide varying levels of functionality, security, and privacy counting on your use case, needs, or company policy.
If you’re employing a proxy server, internet traffic flows through the proxy server on its thanks to the address you requested. A proxy server is essentially a computer on the web with its own IP address that your computer knows. once you send an internet request, your request goes to the proxy server first. The proxy server then makes your web request on your behalf, collects the response from the online server, and forwards you the online page data so you’ll see the page in your browser.
NEW QUESTION 2
which type of virus can change its own code and then cipher itself multiple times as it replicates?
- A. Stealth virus
- B. Tunneling virus
- C. Cavity virus
- D. Encryption virus
Answer: A
Explanation:
A stealth virus may be a sort of virus malware that contains sophisticated means of avoiding detection by antivirus software. After it manages to urge into the now-infected machine a stealth viruses hides itself by continually renaming and moving itself round the disc.
Like other viruses, a stealth virus can take hold of the many parts of one’s PC. When taking control of the PC and performing tasks, antivirus programs can detect it, but a stealth virus sees that coming and can rename then copy itself to a special drive or area on the disc, before the antivirus software.
Once moved and renamed a stealth virus will usually replace the detected ‘infected’ file with a clean file that doesn’t trigger anti-virus detection. It’s a never-ending game of cat and mouse.
The intelligent architecture of this sort of virus about guarantees it’s impossible to completely rid oneself of it once infected. One would need to completely wipe the pc and rebuild it from scratch to completely eradicate the presence of a stealth virus. Using regularly-updated antivirus software can reduce risk, but, as we all know, antivirus software is additionally caught in an endless cycle of finding new threats and protecting against them. https://www.techslang.com/definition/what-is-a-stealth-virus/
NEW QUESTION 3
if you send a TCP ACK segment to a known closed port on a firewall but it does not respond with an RST. what do you know about the firewall you are scanning?
- A. There is no firewall in place.
- B. This event does not tell you encrypting about the firewall.
- C. It is a stateful firewall
- D. It Is a non-stateful firewall.
Answer: B
NEW QUESTION 4
Bella, a security professional working at an it firm, finds that a security breach has occurred while transferring important files. Sensitive data, employee usernames. and passwords are shared In plaintext, paving the way for hackers 10 perform successful session hijacking. To address this situation. Bella Implemented a protocol that sends data using encryption and digital certificates.
Which of the following protocols Is used by Bella?
- A. FTP
- B. HTTPS
- C. FTPS
- D. IP
Answer: C
Explanation:
The File Transfer Protocol (FTP) is a standard organization convention utilized for the exchange of PC records from a worker to a customer on a PC organization. FTP is based on a customer worker model engineering utilizing separate control and information associations between the customer and the server.[1] FTP clients may validate themselves with an unmistakable book sign-in convention, ordinarily as a username and secret key, however can interface namelessly if the worker is designed to permit it. For secure transmission that ensures the username and secret phrase, and scrambles the substance, FTP is frequently made sure about with SSL/TLS (FTPS) or supplanted with SSH File Transfer Protocol (SFTP).
The primary FTP customer applications were order line programs created prior to working frameworks had graphical UIs, are as yet dispatched with most Windows, Unix, and Linux working systems.[2][3] Many FTP customers and mechanization utilities have since been created for working areas, workers, cell phones, and equipment, and FTP has been fused into profitability applications, for example, HTML editors.
NEW QUESTION 5
By performing a penetration test, you gained access under a user account. During the test, you established a connection with your own machine via the SMB service and occasionally entered your login and password in plaintext. Which file do you have to clean to clear the password?
- A. .X session-log
- B. .bashrc
- C. .profile
- D. .bash_history
Answer: D
Explanation:
File created by Bash, a Unix-based shell program commonly used on Mac OS X and Linux operating systems; stores a history of user commands entered at the command prompt; used for viewing old commands that are executed. BASH_HISTORY files are hidden files with no filename prefix. They always use the filename .bash_history.
NOTE: Bash is that the shell program employed by Apple Terminal.
Our goal is to assist you understand what a file with a *.bash_history suffix is and the way to open it.
The Bash History file type, file format description, and Mac and Linux programs listed on this page are individually researched and verified by the FileInfo team. we attempt for 100% accuracy and only publish information about file formats that we’ve tested and validated.
NEW QUESTION 6
Abel, a cloud architect, uses container technology to deploy applications/software including all its dependencies, such as libraries and configuration files, binaries, and other resources that run independently from other processes in the cloud environment. For the containerization of applications, he follows the five-tier container technology architecture. Currently. Abel is verifying and validating image contents, signing images, and sending them to the registries. Which of the following tiers of the container technology architecture Is Abel currently working in?
- A. Tier-1: Developer machines
- B. Tier-4: Orchestrators
- C. Tier-3: Registries
- D. Tier-2: Testing and accreditation systems
Answer: D
Explanation:
The official management decision given by a senior agency official to authorize operation of an information system and to explicitly accept the risk to agency operations (including mission, functions, image, or reputation), agency assets, or individuals, based on the implementation of an agreed-upon set of security controls. formal declaration by a designated accrediting authority (DAA) or principal accrediting authority (PAA) that an information system is approved to operate at an acceptable level of risk, based on the implementation of an approved set of technical, managerial, and procedural safeguards. See authorization to operate (ATO). Rationale: The Risk Management Framework uses a new term to refer to this concept, and it is called authorization.
Identifies the information resources covered by an accreditation decision, as distinguished from separately accredited information resources that are interconnected or with which information is exchanged via messaging. Synonymous with Security Perimeter.
For the purposes of identifying the Protection Level for confidentiality of a system to be accredited, the system has a conceptual boundary that extends to all intended users of the system, both directly and indirectly connected, who receive output from the system. See authorization boundary.
Rationale: The Risk Management Framework uses a new term to refer to the concept of accreditation, and it is called authorization. Extrapolating, the accreditation boundary would then be referred to as the authorization boundary.
NEW QUESTION 7
Boney, a professional hacker, targets an organization for financial benefits. He performs an attack by sending his session ID using an MITM attack technique. Boney first obtains a valid session ID by logging into a service and later feeds the same session 10 to the target employee. The session ID links the target employee to Boneys account page without disclosing any information to the victim. When the target employee clicks on the link, all the sensitive payment details entered in a form are linked to Boneys account. What is the attack performed by Boney in the above scenario?
- A. Session donation attack
- B. Session fixation attack
- C. Forbidden attack
- D. CRIME attack
Answer: A
Explanation:
In a session donation attack, the attacker donates their own session ID to the target user. In this
attack, the attacker first obtains a valid session ID by logging into a service and later feeds the same session ID to the target user. This session ID links a target user to the attacker's account page without disclosing any information to the victim. When the target user clicks on the link and enters the details (username, password, payment details, etc.) in a form, the entered
details are linked to the attacker's account. To initiate this attack, the attacker can send their session ID using techniques such as cross-site cooking, an MITM attack, and session fixation. A session donation attack involves the following steps.
NEW QUESTION 8
John wants to send Marie an email that includes sensitive information, and he does not trust the network that he is connected to. Marie gives him the idea of using PGP. What should John do to communicate correctly using this type of encryption?
- A. Use his own public key to encrypt the message.
- B. Use Marie's public key to encrypt the message.
- C. Use his own private key to encrypt the message.
- D. Use Marie's private key to encrypt the message.
Answer: B
Explanation:
When a user encrypts plaintext with PGP, PGP first compresses the plaintext. The session key works with a very secure, fast conventional encryption algorithm to encrypt the plaintext; the result is ciphertext. Once the data is encrypted, the session key is then encrypted to the recipient's public key https://en.wikipedia.org/wiki/Pretty_Good_Privacy Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, emails, files, directories, and whole disk partitions and to increase the security of e-mail communications.
PGP encryption uses a serial combination of hashing, data compression, symmetric-key cryptography, and finally public-key cryptography; each step uses one of several supported algorithms. Each public key is bound to a username or an e-mail address.
https://en.wikipedia.org/wiki/Public-key_cryptography
Public key encryption uses two different keys. One key is used to encrypt the information and the other is used to decrypt the information. Sometimes this is referred to as asymmetric encryption because two keys are required to make the system and/or process work securely. One key is known as the public key and should be shared by the owner with anyone who will be securely communicating with the key owner. However, the owner’s secret key is not to be shared and considered a private key. If the private key is shared with unauthorized recipients, the encryption mechanisms protecting the information must be considered compromised.
NEW QUESTION 9
A new wireless client is configured to join a 802.11 network. This client uses the same hardware and
software as many of the other clients on the network. The client can see the network, but cannot
connect. A wireless packet sniffer shows that the Wireless Access Point (WAP) is not responding to
the association requests being sent by the wireless client. What is a possible source of this problem?
- A. The WAP does not recognize the client’s MAC address
- B. The client cannot see the SSID of the wireless network
- C. Client is configured for the wrong channel
- D. The wireless client is not configured to use DHCP
Answer: A
Explanation:
https://en.wikipedia.org/wiki/MAC_filtering
MAC filtering is a security method based on access control. Each address is assigned a 48-bit address,
which is used to determine whether we can access a network or not. It helps in listing a set of
allowed devices that you need on your Wi-Fi and the list of denied devices that you don’t want on
your Wi-Fi. It helps in preventing unwanted access to the network. In a way, we can blacklist or white
list certain computers based on their MAC address. We can configure the filter to allow connection
only to those devices included in the white list. White lists provide greater security than blacklists
because the router grants access only to selected devices.
It is used on enterprise wireless networks having multiple access points to prevent clients from
communicating with each other. The access point can be configured only to allow clients to talk to
the default gateway, but not other wireless clients. It increases the efficiency of access to a network.
The router allows configuring a list of allowed MAC addresses in its web interface, allowing you to
choose which devices can connect to your network. The router has several functions designed to
improve the network's security, but not all are useful. Media access control may seem advantageous,
but there are certain flaws.
On a wireless network, the device with the proper credentials such as SSID and password can
authenticate with the router and join the network, which gets an IP address and access to the
internet and any shared resources.
MAC address filtering adds an extra layer of security that checks the device’s MAC address against a
list of agreed addresses. If the client’s address matches one on the router’s list, access is granted;
otherwise, it doesn’t join the network.
NEW QUESTION 10
What is one of the advantages of using both symmetric and asymmetric cryptography in SSL/TLS?
- A. Supporting both types of algorithms allows less-powerful devices such as mobile phones to use symmetric encryption instead.
- B. Symmetric algorithms such as AES provide a failsafe when asymmetric methods fail.
- C. Symmetric encryption allows the server to security transmit the session keys out-of-band.
- D. Asymmetric cryptography is computationally expensive in compariso
- E. However, it is well-suited to securely negotiate keys for use with symmetric cryptography.
Answer: A
NEW QUESTION 11
What is the proper response for a NULL scan if the port is open?
- A. SYN
- B. ACK
- C. FIN
- D. PSH
- E. RST
- F. No response
Answer: F
NEW QUESTION 12
An unauthorized individual enters a building following an employee through the employee entrance after the lunch rush. What type of breach has the individual just performed?
- A. Reverse Social Engineering
- B. Tailgating
- C. Piggybacking
- D. Announced
Answer: B
Explanation:
Explanation
· Identifying operating systems, services, protocols and devices,
· Collecting unencrypted information about usernames and passwords,
· Capturing network traffic for further analysis
are passive network sniffing methods since with the help of them we only receive information and do not make any changes to the target network. When modifying and replaying the captured network traffic, we are already starting to make changes and actively interact with it.
NEW QUESTION 13
= 1/3 (every three years, meaning the probability of occurring during 1
= SLE * ARO = 0.33 * $440 = $145.2
Why should the security analyst disable/remove unnecessary ISAPI filters?
- A. To defend against social engineering attacks
- B. To defend against webserver attacks
- C. To defend against jailbreaking
- D. To defend against wireless attacks
Answer: B
NEW QUESTION 14
Annie, a cloud security engineer, uses the Docker architecture to employ a client/server model in the application she is working on. She utilizes a component that can process API requests and handle various Docker objects, such as containers, volumes. Images, and networks. What is the component of the Docker architecture used by Annie in the above scenario?
- A. Docker client
- B. Docker objects
- C. Docker daemon
- D. Docker registries
Answer: C
Explanation:
Docker uses a client-server design. The docker client talks to the docker daemon, that will the work of building, running, and distributing your docker containers. The docker client and daemon will run on the same system, otherwise you will connect a docker consumer to a remote docker daemon. The docker consumer and daemon communicate using a REST API, over OS sockets or a network interface.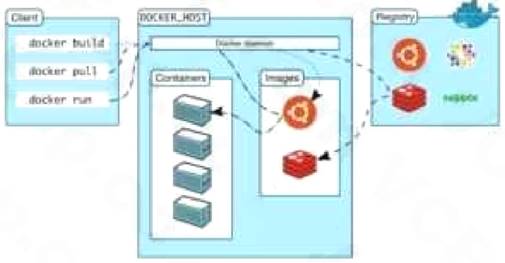
The docker daemon (dockerd) listens for docker API requests and manages docker objects like pictures, containers, networks, and volumes. A daemon may communicate with other daemons to manage docker services.
NEW QUESTION 15
Dorian Is sending a digitally signed email to Polly, with which key is Dorian signing this message and how is Poly validating It?
- A. Dorian is signing the message with his public ke
- B. and Poly will verify that the message came from Dorian by using Dorian's private key.
- C. Dorian Is signing the message with Polys public ke
- D. and Poly will verify that the message came from Dorian by using Dorian's public key.
- E. Dorian is signing the message with his private ke
- F. and Poly will verify that the message came from Dorian by using Dorian's public key.
- G. Dorian is signing the message with Polys private ke
- H. and Poly will verify mat the message came from Dorian by using Dorian's public key.
Answer: C
Explanation:
https://blog.mailfence.com/how-do-digital-signatures-work/ https://en.wikipedia.org/wiki/Digital_signature
A digital signature is a mathematical technique used to validate the authenticity and integrity of a message, software, or digital document. It's the digital equivalent of a handwritten signature or stamped seal, but it offers far more inherent security. A digital signature is intended to solve the problem of tampering and impersonation in digital communications.
Digital signatures can provide evidence of origin, identity, and status of electronic documents, transactions, or digital messages. Signers can also use them to acknowledge informed consent. Digital signatures are based on public-key cryptography, also known as asymmetric cryptography.
Two keys are generated using a public key algorithm, such as RSA (Rivest-Shamir-Adleman), creating a mathematically linked pair of keys, one private and one public.
Digital signatures work through public-key cryptography's two mutually authenticating cryptographic keys. The individual who creates the digital signature uses a private key to encrypt signature-related data, while the only way to decrypt that data is with the signer's public key.
NEW QUESTION 16
Bob was recently hired by a medical company after it experienced a major cyber security breach.
Many patients are complaining that their personal medical records are fully exposed on the Internet and someone can find them with a simple Google search. Bob's boss is very worried because of regulations that protect those dat a. Which of the following regulations is mostly violated?
- A. HIPPA/PHl
- B. Pll
- C. PCIDSS
- D. ISO 2002
Answer: A
Explanation:
PHI stands for Protected Health info. The HIPAA Privacy Rule provides federal protections for private health info held by lined entities and provides patients an array of rights with regard to that info. under HIPAA phi is considered to be any identifiable health info that’s used, maintained, stored, or transmitted by a HIPAA-covered entity – a healthcare provider, health plan or health insurer, or a aid clearinghouse – or a business associate of a HIPAA-covered entity, in relation to the availability of aid or payment for aid services.
It is not only past and current medical info that’s considered letter under HIPAA Rules, however also future info concerning medical conditions or physical and mental health related to the provision of care or payment for care. phi is health info in any kind, together with physical records, electronic records, or spoken info.
Therefore, letter includes health records, medical histories, lab check results, and medical bills. basically, all health info is considered letter once it includes individual identifiers. Demographic info is additionally thought of phi underneath HIPAA Rules, as square measure several common identifiers like patient names, Social Security numbers, Driver’s license numbers, insurance details, and birth dates, once they square measure connected with health info.
The eighteen identifiers that create health info letter are: Names
Dates, except year phonephone numbers Geographic information FAX numbers
Social Security numbers Email addresses
case history numbers Account numbers
Health arrange beneficiary numbers Certificate/license numbers
Vehicle identifiers and serial numbers together with license plates Web URLs
Device identifiers and serial numbers net protocol addresses
Full face photos and comparable pictures Biometric identifiers (i.e. retinal scan, fingerprints) Any distinctive identifying variety or code
One or a lot of of those identifiers turns health info into letter, and phi HIPAA Privacy Rule restrictions can then apply that limit uses and disclosures of the data. HIPAA lined entities and their business associates will ought to guarantee applicable technical, physical, and body safeguards are enforced to make sure the confidentiality, integrity, and availability of phi as stipulated within the HIPAA
Security Rule.
NEW QUESTION 17
Louis, a professional hacker, had used specialized tools or search engines to encrypt all his browsing activity and navigate anonymously to obtain sensitive/hidden information about official government or federal databases. After gathering the Information, he successfully performed an attack on the target government organization without being traced. Which of the following techniques is described in the above scenario?
- A. Dark web footprinting
- B. VoIP footpnnting
- C. VPN footprinting
- D. website footprinting
Answer: A
Explanation:
The deep web is the layer of the online cyberspace that consists of web pages and content that are hidden and unindexed.
NEW QUESTION 18
Which of the following tools can be used to perform a zone transfer?
- A. NSLookup
- B. Finger
- C. Dig
- D. Sam Spade
- E. Host
- F. Netcat
- G. Neotrace
Answer: ACDE
NEW QUESTION 19
In the context of Windows Security, what is a 'null' user?
- A. A user that has no skills
- B. An account that has been suspended by the admin
- C. A pseudo account that has no username and password
- D. A pseudo account that was created for security administration purpose
Answer: C
NEW QUESTION 20
Attacker Rony installed a rogue access point within an organization's perimeter and attempted to intrude into its internal network. Johnson, a security auditor, identified some unusual traffic in the internal network that is aimed at cracking the authentication mechanism. He immediately turned off the targeted network and tested for any weak and outdated security mechanisms that are open to attack. What is the type of vulnerability assessment performed by johnson in the above scenario?
- A. Host-based assessment
- B. Wireless network assessment
- C. Application assessment
- D. Distributed assessment
Answer: B
Explanation:
Wireless network assessment determines the vulnerabilities in an organization’s wireless networks. In the past, wireless networks used weak and defective data encryption mechanisms. Now, wireless network standards have evolved, but many networks still use weak and outdated security mechanisms and are open to attack. Wireless network assessments try to attack wireless authentication mechanisms and gain unauthorized access. This type of assessment tests wireless networks and identifies rogue networks that may exist within an organization’s perimeter. These assessments audit client-specified sites with a wireless network. They sniff wireless network traffic and try to crack encryption keys. Auditors test other network access if they gain access to the wireless network.
NEW QUESTION 21
......
100% Valid and Newest Version 312-50v12 Questions & Answers shared by Dumpscollection.com, Get Full Dumps HERE: https://www.dumpscollection.net/dumps/312-50v12/ (New 503 Q&As)