It is more faster and easier to pass the Cisco 350-701 exam by using Approved Cisco Implementing and Operating Cisco Security Core Technologies questuins and answers. Immediate access to the Updated 350-701 Exam and find the same core area 350-701 questions with professionally verified answers, then PASS your exam with a high score now.
Check 350-701 free dumps before getting the full version:
NEW QUESTION 1
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic?
- A. File Analysis
- B. SafeSearch
- C. SSL Decryption
- D. Destination Lists
Answer: C
NEW QUESTION 2
On which part of the IT environment does DevSecOps focus?
- A. application development
- B. wireless network
- C. data center
- D. perimeter network
Answer: A
NEW QUESTION 3
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol?
- A. STIX
- B. XMPP
- C. pxGrid
- D. SMTP
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/web_security/scancenter/administrator/guide/b_ScanCenter_Administrator_Guide/b_ScanCenter_Administrator_Guide_chapter_0100011.pdf
NEW QUESTION 4
Which statement about the configuration of Cisco ASA NetFlow v9 Secure Event Logging is true?
- A. To view bandwidth usage for NetFlow records, the QoS feature must be enabled.
- B. A sysopt command can be used to enable NSEL on a specific interface.
- C. NSEL can be used without a collector configured.
- D. A flow-export event type must be defined under a policy.
Answer: D
NEW QUESTION 5
Which two request of REST API are valid on the Cisco ASA Platform? (Choose two.)
- A. put
- B. options
- C. get
- D. push
- E. connect
Answer: AC
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/api/qsg-asa-api.html
NEW QUESTION 6
Which benefit does endpoint security provide the overall security posture of an organization?
- A. It streamlines the incident response process to automatically perform digital forensics on the endpoint.
- B. It allows the organization to mitigate web-based attacks as long as the user is active in the domain.
- C. It allows the organization to detect and respond to threats at the edge of the network.
- D. It allows the organization to detect and mitigate threats that the perimeter security devices do not detect.
Answer: D
NEW QUESTION 7
In which cloud services model is the tenant responsible for virtual machine OS patching?
- A. IaaS
- B. UCaaS
- C. PaaS
- D. SaaS
Answer: A
Explanation:
Reference: https://www.cmswire.com/cms/information-management/cloud-service-models-iaas-saas-paas-how-microsoft-office-365-azure-fit-in-021672.php
NEW QUESTION 8
DRAG DROP
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.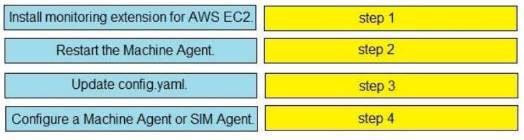
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 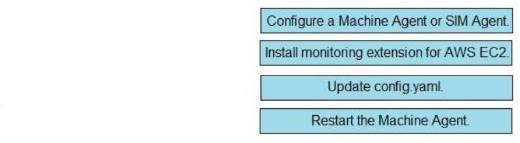
NEW QUESTION 9
How is ICMP used an exfiltration technique?
- A. by flooding the destination host with unreachable packets
- B. by sending large numbers of ICMP packets with a targeted hosts source IP address using an IP broadcast address
- C. by encrypting the payload in an ICMP packet to carry out command and control tasks on a compromised host
- D. by overwhelming a targeted host with ICMP echo-request packets
Answer: C
NEW QUESTION 10
Why would a user choose an on-premises ESA versus the CES solution?
- A. Sensitive data must remain onsite.
- B. Demand is unpredictable.
- C. The server team wants to outsource this service.
- D. ESA is deployed inline.
Answer: A
NEW QUESTION 11
What is the primary difference between an Endpoint Protection Platform and an Endpoint Detection and Response?
- A. EPP focuses on prevention, and EDR focuses on advanced threats that evade perimeter defenses.
- B. EDR focuses on prevention, and EPP focuses on advanced threats that evade perimeter defenses.
- C. EPP focuses on network security, and EDR focuses on device security.
- D. EDR focuses on network security, and EPP focuses on device security.
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/products/security/endpoint-security/what-is-endpoint-detection-response-edr.html
NEW QUESTION 12
Which feature is configured for managed devices in the device platform settings of the Firepower Management Center?
- A. quality of service
- B. time synchronization
- C. network address translations
- D. intrusion policy
Answer: B
NEW QUESTION 13
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
- A. authenticates the IKEv2 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX
- B. authenticates the IP address of the 172.16.0.0/32 peer by using the key ciscXXXXXXXX
- C. authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX
- D. secures all the certificates in the IKE exchange by using the key ciscXXXXXXXX
Answer: B
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/security/a1/sec-a1-cr-book/sec-cr-c4.html#wp6039879000
NEW QUESTION 14
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
- A. transparent
- B. redirection
- C. forward
- D. proxy gateway
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117940-qa-wsa-00.html
NEW QUESTION 15
In a PaaS model, which layer is the tenant responsible for maintaining and patching?
- A. hypervisor
- B. virtual machine
- C. network
- D. application
Answer: D
Explanation:
Reference: https://www.bmc.com/blogs/saas-vs-paas-vs-iaas-whats-the-difference-and-how-to-choose/
NEW QUESTION 16
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two.)
- A. Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
- B. Cisco FTDv with one management interface and two traffic interfaces configured
- C. Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
- D. Cisco FTDv with two management interfaces and one traffic interface configured
- E. Cisco FTDv configured in routed mode and IPv6 configured
Answer: AC
Explanation:
Reference: https://www.cisco.com/c/en/us/products/collateral/security/adaptive-security-virtual-appliance-asav/white-paper-c11-740505.html
NEW QUESTION 17
What is the difference between deceptive phishing and spear phishing?
- A. Deceptive phishing is an attacked aimed at a specific user in the organization who holds a C-level role.
- B. A spear phishing campaign is aimed at a specific person versus a group of people.
- C. Spear phishing is when the attack is aimed at the C-level executives of an organization.
- D. Deceptive phishing hijacks and manipulates the DNS server of the victim and redirects the user to a false webpage.
Answer: B
NEW QUESTION 18
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware? (Choose two.)
- A. Sophos engine
- B. white list
- C. RAT
- D. outbreak filters
- E. DLP
Answer: AD
NEW QUESTION 19
Which two conditions are prerequisites for stateful failover for IPsec? (Choose two.)
- A. Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically.
- B. The active and standby devices can run different versions of the Cisco IOS software but must be the same type of device.
- C. The IPsec configuration that is set up on the active device must be duplicated on the standby device.
- D. Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically.
- E. The active and standby devices must run the same version of the Cisco IOS software and must be the same type of device.
Answer: BC
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_vpnav/configuration/15-mt/sec-vpn-availability-15-mt-book/sec-state-fail-ipsec.html
NEW QUESTION 20
Which VPN technology can support a multivendor environment and secure traffic between sites?
- A. SSL VPN
- B. GET VPN
- C. FlexVPN
- D. DMVPN
Answer: C
Explanation:
Reference: https://www.cisco.com/c/en/us/products/collateral/routers/asr-1000-series-aggregation-services-routers/data_sheet_c78-704277.html
NEW QUESTION 21
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two.)
- A. DDoS
- B. antispam
- C. antivirus
- D. encryption
- E. DLP
Answer: DE
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/td/docs/security/ces/overview_guide/Cisco_Cloud_Hybrid_Email_Security_Overview_Guide.pdf
NEW QUESTION 22
Which command enables 802.1X globally on a Cisco switch?
- A. dot1x system-auth-control
- B. dot1x pae authenticator
- C. authentication port-control auto
- D. aaa new-model
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/routers/nfvis/switch_command/b-nfvis-switch-command-reference/802_1x_commands.html
NEW QUESTION 23
An engineer is configuring AMP for endpoints and wants to block certain files from executing. Which outbreak control method is used to accomplish this task?
- A. device flow correlation
- B. simple detections
- C. application blocking list
- D. advanced custom detections
Answer: C
NEW QUESTION 24
Which network monitoring solution uses streams and pushes operational data to provide a near real-time view of activity?
- A. SNMP
- B. SMTP
- C. syslog
- D. model-driven telemetry
Answer: D
Explanation:
Reference: https://developer.cisco.com/docs/ios-xe/#!streaming-telemetry-quick-start-guide
NEW QUESTION 25
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?
- A. Nexus
- B. Stealthwatch
- C. Firepower
- D. Tetration
Answer: D
Explanation:
Reference: https://www.cisco.com/c/en/us/solutions/security/secure-data-center-solution/index.html#~products
NEW QUESTION 26
......
P.S. Surepassexam now are offering 100% pass ensure 350-701 dumps! All 350-701 exam questions have been updated with correct answers: https://www.surepassexam.com/350-701-exam-dumps.html (102 New Questions)