Proper study guides for 70-414 Implementing an Advanced Server Infrastructure certified begins with preparation products which designed to deliver the by making you pass the 70-414 test at your first time. Try the free right now.
Check 70-414 free dumps before getting the full version:
NEW QUESTION 1
Your network contains four servers. The servers are configured as shown in the following table.
You manage all of the servers and all of the clusters by using Microsoft System Center 2012 Virtual Machine Manager (VMM).
You plan to implement Dynamic Optimization for the virtual machines. You need to recommend a configuration for the planned implementation.
What should you recommend?
- A. Dynamic Optimization on Cluster3 and Cluster4 only Virtual machines that are balanced across the clusters
- B. Dynamic Optimization on all of the clustersVirtual machines that are balanced across the nodes in the clusters
- C. Dynamic Optimization on all of the clustersVirtual machines that are balanced across the clusters
- D. Dynamic Optimization on Cluster1 and Cluster2 onlyVirtual machines that are balanced across the nodes in the clusters
Answer: B
Explanation: Explanation:
http://technet.microsoft.com/en-us/library/gg675109.aspx
NEW QUESTION 2
You have a System Center 2012 R2 Configuration Manager deployment.
All users have client computers that run Windows 8.1. The users log on to their client computers as standard users.
An application named App1 is deployed to the client computers by using System Center.
You need to recommend a solution to validate a registry key used by App1. If the registry key has an incorrect value, the value must be changed. The registry key must be validated every day. The solution must generate a report on non-compliant computers.
What is the best approach to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
- A. Group Policy preferences
- B. A desired configuration baseline
- C. The Windows PowerShell Desired State Configuration (DSC) feature
- D. The Microsoft Baseline Security Analyzer (MBSA)
Answer: B
NEW QUESTION 3
You need to automatically restart the appropriate web service on DETCRL01 and CHICRL01 if the web service is stopped.
Solution: You create a recovery task in SCOM and configure it to start the World Wide Web publishing service.
Does this meet the goal?
- A. Yes
- B. No
Answer: A
Explanation: The Internet Information Services (IIS) World Wide Web Publishing Service (W3SVC), sometimes referred to as the WWW Service, manages the HTTP protocol and HTTP performance counters.
The following is a list of the managed entities that are included in this managed entity:
* IIS Web Site
An Internet Information Services (IIS) Web site is a unique collection of Web pages and Web applications that is hosted on an IIS Web server. Web sites have bindings that consist of a port number, an IP address, and an optional host name or names.
* Active Server Pages (ASP) Active Server Pages (ASP)
NEW QUESTION 4
You use the entire System Center suite. You integrate Service Manager with Operations Manager, Virtual Machine Manager, Orchestrator, and Active Directory. You perform all remediation by using Orchestrator runbooks. An application experiences performance problems on a periodic basis.
You have the following requirements:
A new incident must be opened when System Center Operations Manager (SCOM) detects a performance problem.
The incident must be closed when the performance problem is resolved.
The incident must be associated with the HR performance problem in Service Manager. You need to configure the environment.
Answer:
Explanation: 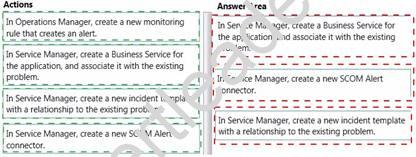
NEW QUESTION 5
Your network contains servers that run Windows Server 2012. The network contains two servers named Server1 and Server2 that are connected to a SAS storage device. The device only supports two connected computers.
Server1 has the iSCSI Target Server role service installed. Ten application servers use their iSCSI Initiator to connect to virtual disks in the SAS storage device via iSCSI targets on Server1.
Currently, Server2 is used only to run backup software. You install the iSCSI Target Server role service on Server2.
You need to ensure that the iSCSI targets are available if Server1 fails. Which five actions should you perform?
To answer, move the five appropriate actions from the list of actions to the answer area and arrange them in the correct order.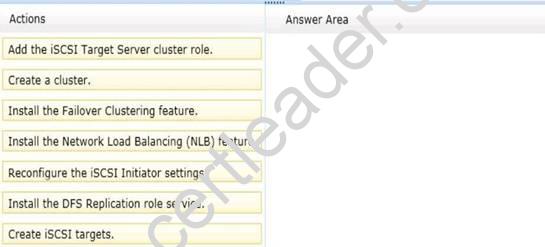
Answer:
Explanation: 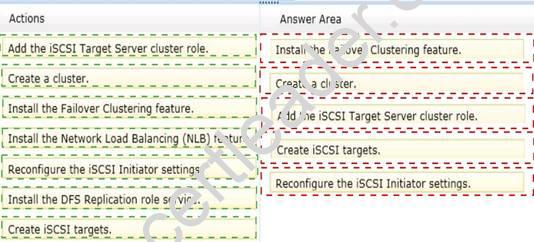
NEW QUESTION 6
Your network contains two Hyper-V hosts named Host1 and Host2. Host1 contains a virtual machine named VM1. Host2 contains a virtual machine named VM2. VM1 and VM2 run Windows Server 2012 R2.
You install the Network Load Balancing feature on VM1 and VM2. You need to ensure that the virtual machines are configured to support Network Load Balancing (NLB).
Which virtual machine settings should you configure on VM1 and VM2?
- A. DHCP guard
- B. MAC address
- C. Router guard
- D. Port mirroring
Answer: B
Explanation: Explanation:
When MAC addresses are not assigned to virtual machines, it could cause network problems.
NEW QUESTION 7
Your network contains an Active Directory domain named contoso.com. The network contains a perimeter network. The perimeter network and the internal network are separated by a firewall.
On the perimeter network, you deploy a server named Server1 that runs Windows Server 2012. You deploy Active Directory Certificate Services (AD CS).
Each user is issued a smart card.
Users report that when they work remotely, they are unable to renew their smart card certificate.
You need to recommend a solution to ensure that the users can renew their smart card certificate from the Internet.
What should you recommend implementing on Server1?
More than one answer choice may achieve the goal. Select the BEST answer.
- A. The Certificate Enrollment Policy Web Service role service and the Certificate Enrollment Web Service role service
- B. The Active Directory Federation Services server role
- C. An additional certification authority (CA) and the Online Responder role service
- D. The Certification Authority Web Enrollment role service and the Online Responder role service
Answer: A
NEW QUESTION 8
You need to delegate permissions for DETCA01.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.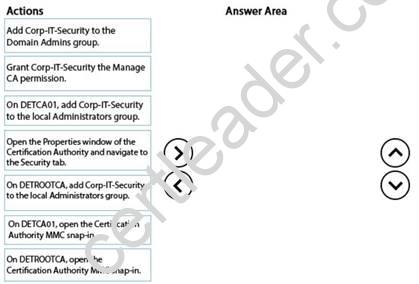
Answer:
Explanation: 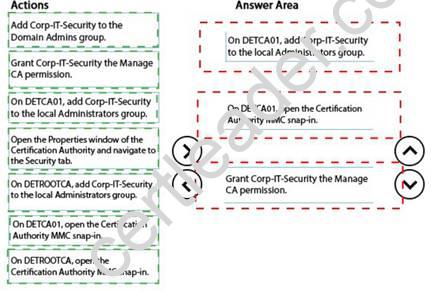
NEW QUESTION 9
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. System Center 2012 R2 Virtual Machine Manager (VMM) is deployed to the domain.
In VMM, you create a host group named HostGroup1. You add a 16-node Hyper-V failover cluster to HostGroup1. From Windows PowerShell, you run the following commands: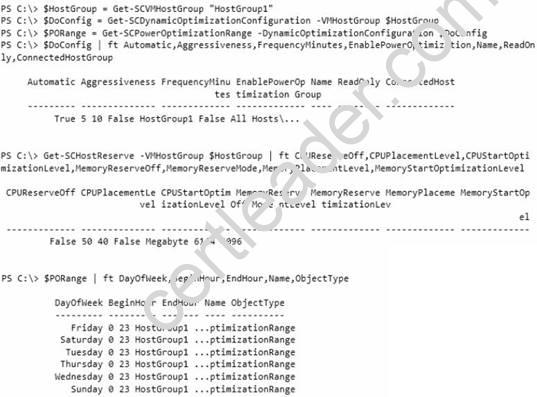
Use the drop-down menus to select the answer choice that completes each statement.
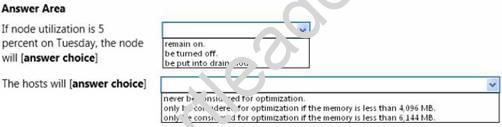
Answer:
Explanation: 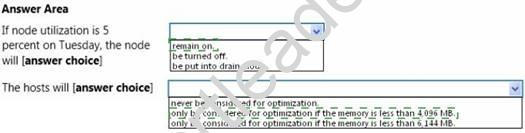
NEW QUESTION 10
You need to recommend which Certificate Services role service must be deployed to the perimeter network. The solution must meet the security requirements.
Which Certificate Services role services should you recommend?
- A. Online Responder and Network Device Enrollment Service
- B. Online Responder and Certificate Enrollment Web Service
- C. Certificate Enrollment Web Service and Certificate Enrollment Policy Web Service
- D. Certificate Enrollment Policy Web Service and Certification Authority Web Enrollment
Answer: C
NEW QUESTION 11
Your network contains an Active Directory domain named contoso.com. The network has an Active Directory Certificate Services (AD CS) infrastructure.
You need to issue a certificate to users to meet the following requirements:
Ensure that the users can encrypt files by using Encrypting File System (EFS).
Ensure that all of the users reenroll for their certificate every six months.
What should you do first?
- A. From the properties of the User certificate template, assign the Allow -Enroll permission to the Authenticated Users group.
- B. From the properties of the Basic EFS template, assign the Allow -Enroll permission to the Authenticated Users group.
- C. Create a copy of the User certificate template, and then modify the extensions of the copy.
- D. Create a copy of the Basic EFS certificate template, and then modify the validity period of the copy.
Answer: D
Explanation: 
NEW QUESTION 12
You need to recommend changes to the existing environment to meet the email requirement. What should you recommend?
- A. Implement a two-way forest trust that has selective authentication.
- B. Implement qualified subordination.
- C. Deploy the FabrikamCA root certificate to all of the client computers.
- D. Deploy a user certificate from FabrikamCA to all of the users.
Answer: B
NEW QUESTION 13
Your network contains two servers named Server1 and Server2 that run Windows Server 2012.
Server1 and Server2 are members of a failover cluster named Cluster1 and are connected to an iSCSI Storage Area Network (SAN).
You need to ensure that you can implement the clustered File Server role of the File Server for scale-out application data type for Cluster1.
What should you install?
- A. The iSCSI Target Server cluster role
- B. The Distributed Transaction Coordinator (DTC) cluster role
- C. The DFS Namespace Server cluster role
- D. A Cluster Shared Volume (CSV)
Answer: D
Explanation: 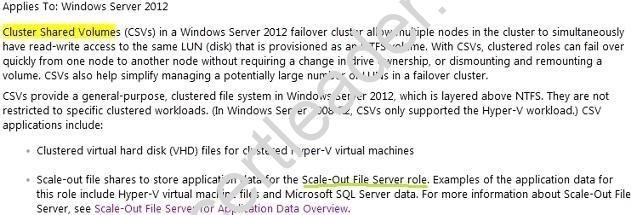
NEW QUESTION 14
An organization uses an Active Directory Rights Management Services (AD RMS) cluster named RMS1 to protect content for a project. You uninstall AD RMS when the project is complete. You need to ensure that the protected content is still available after AD RMS is uninstalled.
Solution: You add the backup service account to the SuperUsers group and back up the protected content. Then, you restore the content to a file server and apply the required NTFS permissions to the files.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 15
You administer an Active Directory Domain Services environment. There are no certification authorities (CAs) in the environment.
You plan to implement a two-tier CA hierarchy with an offline root CA.
You need to ensure that the issuing CA is not used to create additional subordinate CAs. What should you do?
- A. In the CAPolicy.inf file for the issuing CA, enter the following constraint: PathLength=1
- B. In the CAPolicy.inf file for the root CA, enter the following constraint: PathLength=1
- C. In the CAPolicy.inf file for the root CA, enter the following constraint: PathLength=2
- D. In the CAPolicy.inf file for the issuing CA, enter the following constraint:PathLength=2
Answer: B
Explanation: Explanation:
You can use the CAPolicy.inf file to define the PathLength constraint in the Basic Constraints extension of the root CA certificate. Setting the PathLength basic constraint allows you to limit the path length of the CA hierarchy by specifying how many tiers of subordinate CAs can exist beneath the root. A PathLength of 1 means there can be at most one tier of CAs beneath the root. These subordinate CAs will have a PathLength basic constraint of 0, which means that they cannot issue any subordinate CA certificates.
NEW QUESTION 16
Your network contains an Active Directory domain named contoso.com. The domain contains a Microsoft System Center 2012 infrastructure. You deploy a service named Service1 by using a service template. Service1 contains two virtual machines. The virtual machines are configured as shown in the following table.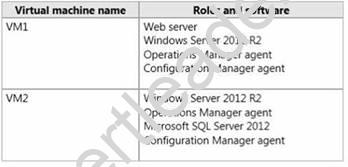
You need to recommend a monitoring solution to ensure that an administrator can review the availability information of Service1.
What should you do?
- A. From Configuration Manager, create a Collection and a Desired Configuration Management baseline.
- B. From Virtual Machine Manager (VMM), modify the properties of the service template.
- C. From Operations Manager, create a Distributed Application and a Monitor Override.
- D. From Operations Manager, create a Distributed Application and a Service Level Tracking object.
Answer: D
Explanation: 
NEW QUESTION 17
Your network contains an Active Directory domain named contoso.com. The domain contains several domain controllers. The domain controllers run either Windows Server 2012 or Windows Server 2008 R2.
The domain functional level is Windows Server 2008 R2. The forest functional level is Windows Server 2008. The corporate compliance policy states that all items deleted from Active Directory must be recoverable from a Recycle Bin.
You need to recommend changes to the current environment to meet the compliance policy.
Which changes should you recommend? (Each correct answer presents part of the solution. Choose all that apply.)
- A. Raise the forest functional level to Windows Server 2008 R2.
- B. Run the Enable-ADOptionalFeature cmdlet.
- C. Run the New-ADObject cmdlet.
- D. Run the Set-Server cmdlet
- E. Raise the domain functional level to Windows Server 2012.
Answer: AB
Explanation: You can enable Active Directory Recycle Bin only if the forest functional level of your environment is set to Windows Server 2008 R2.
B: Enabling Active Directory Recycle Bin
After the forest functional level of your environment is set to Windows Server 2008 R2, you can enable Active Directory Recycle Bin by using the following methods:
/ Enable-ADOptionalFeature Active Directory module cmdlet (This is the recommended method.)
/ Ldp.exe
Note: By default, Active Directory Recycle Bin in Windows Server 2008 R2 is disabled.
P.S. Easily pass 70-414 Exam with 270 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy 70-414 Dumps: https://www.2passeasy.com/dumps/70-414/ (270 New Questions)