we provide Breathing CompTIA CS0-002 training which are the best for clearing CS0-002 test, and to get certified by CompTIA CompTIA Cybersecurity Analyst (CySA+) Certification Exam. The CS0-002 Questions & Answers covers all the knowledge points of the real CS0-002 exam. Crack your CompTIA CS0-002 Exam with latest dumps, guaranteed!
Also have CS0-002 free dumps questions for you:
NEW QUESTION 1
A security analyst is investigating a system compromise. The analyst verities the system was up to date on OS patches at the time of the compromise. Which of the following describes the type of vulnerability that was MOST likely expiated?
- A. Insider threat
- B. Buffer overflow
- C. Advanced persistent threat
- D. Zero day
Answer: D
NEW QUESTION 2
A Chief Information Security Officer (CISO) wants to upgrade an organization's security posture by improving proactive activities associated with attacks from internal and external threats.
Which of the following is the MOST proactive tool or technique that feeds incident response capabilities?
- A. Development of a hypothesis as part of threat hunting
- B. Log correlation, monitoring, and automated reporting through a SIEM platform
- C. Continuous compliance monitoring using SCAP dashboards
- D. Quarterly vulnerability scanning using credentialed scans
Answer: A
NEW QUESTION 3
Which of the following technologies can be used to house the entropy keys for disk encryption on desktops and laptops?
- A. Self-encrypting drive
- B. Bus encryption
- C. TPM
- D. HSM
Answer: A
NEW QUESTION 4
Which of me following BEST articulates the benefit of leveraging SCAP in an organization's cybersecurity analysis toolset?
- A. It automatically performs remedial configuration changes lo enterprise security services
- B. It enables standard checklist and vulnerability analysis expressions for automaton
- C. It establishes a continuous integration environment for software development operations
- D. It provides validation of suspected system vulnerabilities through workflow orchestration
Answer: B
NEW QUESTION 5
Which of the following BEST describes the process by which code is developed, tested, and deployed in small batches?
- A. Agile
- B. Waterfall
- C. SDLC
- D. Dynamic code analysis
Answer: A
NEW QUESTION 6
A monthly job to install approved vendor software updates and hot fixes recently stopped working. The security team performed a vulnerability scan, which identified several hosts as having some critical OS vulnerabilities, as referenced in the common vulnerabilities and exposures (CVE) database.
Which of the following should the security team do NEXT to resolve the critical findings in the most effective manner? (Choose two.)
- A. Patch the required hosts with the correct updates and hot fixes, and rescan them for vulnerabilities.
- B. Remove the servers reported to have high and medium vulnerabilities.
- C. Tag the computers with critical findings as a business risk acceptance.
- D. Manually patch the computers on the network, as recommended on the CVE website.
- E. Harden the hosts on the network, as recommended by the NIST framework.
- F. Resolve the monthly job issues and test them before applying them to the production network.
Answer: CE
NEW QUESTION 7
A system’s authority to operate (ATO) is set to expire in four days. Because of other activities and limited staffing, the organization has neglected to start reauthentication activities until now. The cybersecurity group just performed a vulnerability scan with the partial set of results shown below: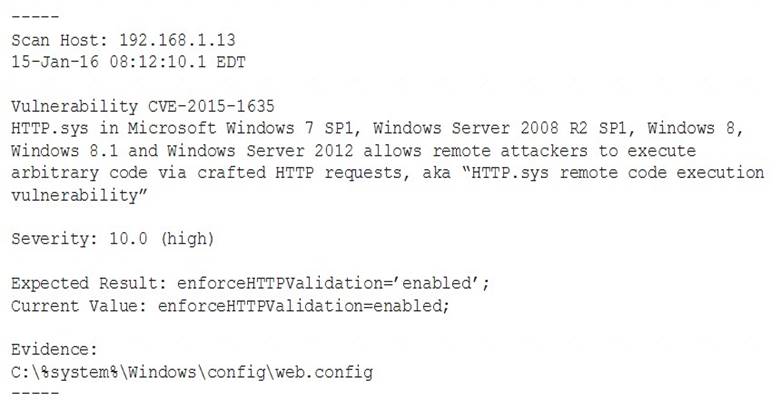
Based on the scenario and the output from the vulnerability scan, which of the following should the security team do with this finding?
- A. Remediate by going to the web config file, searching for the enforce HTTP validation setting, and manually updating to the correct setting.
- B. Accept this risk for now because this is a “high” severity, but testing will require more than the four days available, and the system ATO needs to be competed.
- C. Ignore i
- D. This is false positive, and the organization needs to focus its efforts on other findings.
- E. Ensure HTTP validation is enabled by rebooting the server.
Answer: A
NEW QUESTION 8
A network attack that is exploiting a vulnerability in the SNMP is detected. Which of the following should the cybersecurity analyst do FIRST?
- A. Apply the required patches to remediate the vulnerability.
- B. Escalate the incident to senior management for guidance.
- C. Disable all privileged user accounts on the network.
- D. Temporarily block the attacking IP address.
Answer: A
NEW QUESTION 9
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the desk ticket queue. INSTRUCTIONS
Click on me ticket to see the ticket details Additional content is available on tabs within the ticket
First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button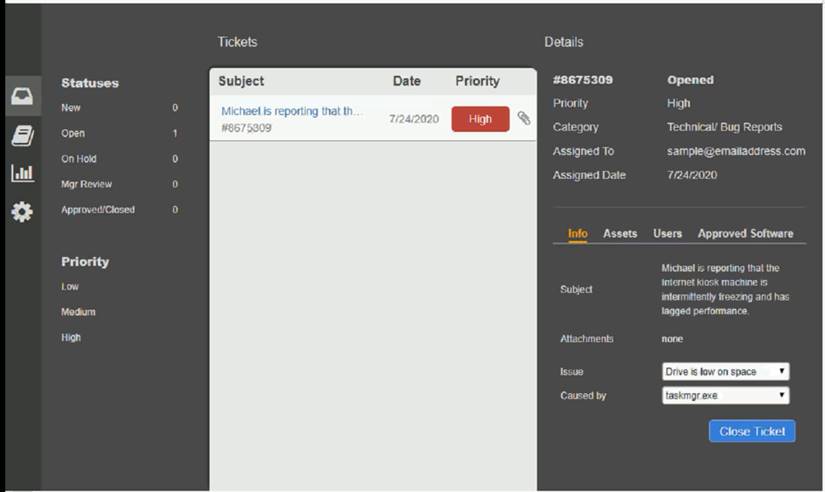

- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 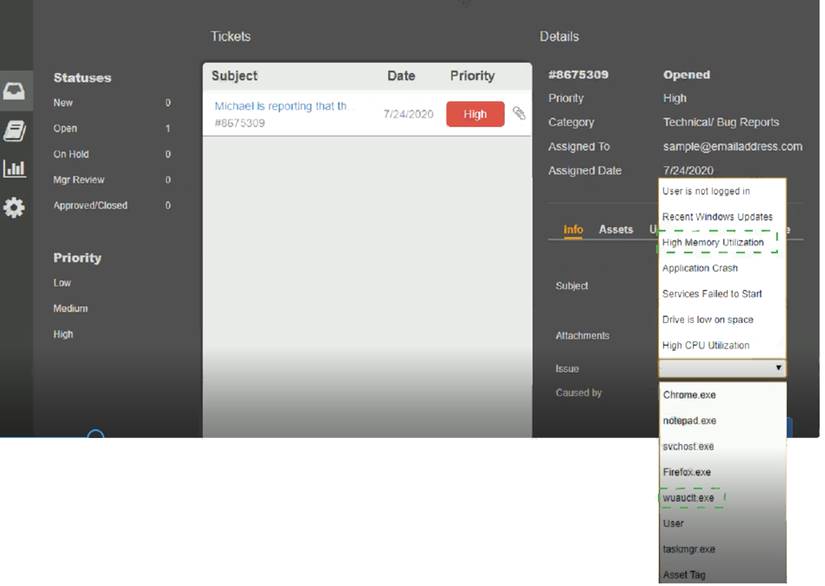
NEW QUESTION 10
A security analyst was alerted to a tile integrity monitoring event based on a change to the vhost-paymonts .c onf file The output of the diff command against the known-good backup reads as follows
Which of the following MOST likely occurred?
- A. The file was altered to accept payments without charging the cards
- B. The file was altered to avoid logging credit card information
- C. The file was altered to verify the card numbers are valid.
- D. The file was altered to harvest credit card numbers
Answer: A
NEW QUESTION 11
The security team at a large corporation is helping the payment-processing team to prepare for a regulatory compliance audit and meet the following objectives: Reduce the number of potential findings by the auditors.
Reduce the number of potential findings by the auditors. Limit the scope of the audit to only devices used by the payment-processing team for activities directly impacted by the regulations.
Limit the scope of the audit to only devices used by the payment-processing team for activities directly impacted by the regulations. Prevent the external-facing web infrastructure used by other teams from coming into scope.
Prevent the external-facing web infrastructure used by other teams from coming into scope. Limit the amount of exposure the company will face if the systems used by the payment-processing
Limit the amount of exposure the company will face if the systems used by the payment-processing
team are compromised.
Which of the following would be the MOST effective way for the security team to meet these objectives?
- A. Limit the permissions to prevent other employees from accessing data owned by the business unit.
- B. Segment the servers and systems used by the business unit from the rest of the network.
- C. Deploy patches to all servers and workstations across the entire organization.
- D. Implement full-disk encryption on the laptops used by employees of the payment-processing team.
Answer: B
NEW QUESTION 12
Which of the following is the MOST important objective of a post-incident review?
- A. Capture lessons learned and improve incident response processes
- B. Develop a process for containment and continue improvement efforts
- C. Identify new technologies and strategies to remediate
- D. Identify a new management strategy
Answer: A
NEW QUESTION 13
A cybersecurity analyst is currently checking a newly deployed server that has an access control list applied. When conducting the scan, the analyst received the following code snippet of results: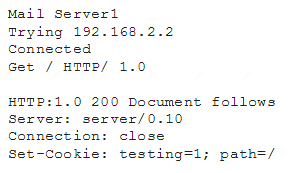
Which of the following describes the output of this scan?
- A. The analyst has discovered a False Positive, and the status code is incorrect providing an OK message.
- B. The analyst has discovered a True Positive, and the status code is correct providing a file not found error message.
- C. The analyst has discovered a True Positive, and the status code is incorrect providing a forbidden message.
- D. The analyst has discovered a False Positive, and the status code is incorrect providing a server error message.
Answer: B
NEW QUESTION 14
Which of the following BEST articulates the benefit of leveraging SCAP in an organization’s cybersecurity analysis toolset?
- A. It automatically performs remedial configuration changes to enterprise security services
- B. It enables standard checklist and vulnerability analysis expressions for automation
- C. It establishes a continuous integration environment for software development operations
- D. It provides validation of suspected system vulnerabilities through workflow orchestration
Answer: B
NEW QUESTION 15
The help desk provided a security analyst with a screenshot of a user's desktop: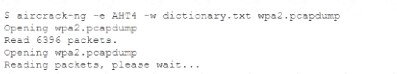
For which of the following is aircrack-ng being used?
- A. Wireless access point discovery
- B. Rainbow attack
- C. Brute-force attack
- D. PCAP data collection
Answer: B
NEW QUESTION 16
A security administrator needs to create an IDS rule to alert on FTP login attempts by root. Which of the following rules is the BEST solution?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: B
NEW QUESTION 17
A security analyst is reviewing the following web server log: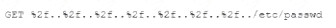
Which of the following BEST describes the issue?
- A. Directory traversal exploit
- B. Cross-site scripting
- C. SQL injection
- D. Cross-site request forgery
Answer: A
NEW QUESTION 18
......
Recommend!! Get the Full CS0-002 dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/CS0-002-dumps.html (New 186 Q&As Version)