Your success in Juniper JN0-1332 is our sole target and we develop all our JN0-1332 braindumps in a way that facilitates the attainment of this target. Not only is our JN0-1332 study material the best you can find, it is also the most detailed and the most updated. JN0-1332 Practice Exams for Juniper JN0-1332 are written to the highest standards of technical accuracy.
Juniper JN0-1332 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
When designing the security for a service provider core router, you are asked to add a firewall fitter on the to0 interface in this scenario, which two protocols would you want to allow through the filter? (Choose two.)
- A. LLDP
- B. SSH
- C. BGP
- D. STP
Answer: AC
NEW QUESTION 2
According to Juniper Networks, what are two focus points when designing a secure network? (Choose two.)
- A. performance
- B. automation
- C. distributed control
- D. classification
Answer: AD
NEW QUESTION 3
You are asked to enable denial of service protection for a webserver behind an SRX Series device In this scenario, which feature would you enable?
- A. screens
- B. App Secure
- C. Web filtering
- D. Juniper ATP
Answer: D
NEW QUESTION 4
You are designing a security solution for an existing data center. All traffic most be secured using SRX Series devices, however, you are unable to change the existing IP addressing scheme. Which firewall deployment method satisfies this requirement?
- A. transparent deployment
- B. two-arm deployment
- C. one-arm deployment
- D. inline deployment
Answer: A
NEW QUESTION 5
Multiple customers use the shared infrastructure of your data center. These customers require isolation for compliance and security reasons.
What would you do to satisfy this requirement?
- A. Isolate each customer by using different physical hard//are
- B. Deploy multiple physical security control points
- C. Deploy a single logical security control point.
- D. Place each customers VLANs separate virtual router
Answer: C
NEW QUESTION 6
You are asked to segment the networks connected to an SRX Series device into distinct logical groups with different security requirements.
How would you accomplish this task?
- A. Define different NAT policies for each network segment.
- B. Define different security policies for each network segment.
- C. Define different intrusion prevention policies for each network segment.
- D. Define different security zones for each network segment
Answer: B
NEW QUESTION 7
What are two factors you must consider when designing a network for security intelligence? (Choose two.)
- A. the number and model of JSA Series devices
- B. the third-party management application
- C. the number and model of SRX Series devices
- D. the Junos OS version
Answer: B
NEW QUESTION 8
As part of your design to secure a service provider WAN. you are asked to design a destination-based remote triggered black hole (RTBH) solution What arc two reasons for using this design? (Choose two)
- A. The attack is focused on a single IP address
- B. You do not know the source address of DDoS packets
- C. The attack comes from a limited number of source IP addresses
- D. You want to ensure that the destination IP remains reachable
Answer: D
NEW QUESTION 9
Which two features would provide protection from known malware? (Choose two.)
- A. ALGs
- B. screens
- C. Junker ATP Cloud
- D. IPS
Answer: BC
NEW QUESTION 10
You are asked to design an automated vulnerability scanner that can actively check to see which ports are open and report on the findings. Which Junker Networks product would you use in this scenario7
- A. Security Director
- B. Log Director
- C. Policy Enforcer
- D. JSA
Answer: C
NEW QUESTION 11
Refer to the exhibit.
The SRX Series devices are decoyed in an off-path active/passive Cluster configuration
What are two advantages of this deployment model over an active-'active duster configuration' (Choose two)
- A. load-balancing of east/west traffic
- B. load-balancing of north/south traffic
- C. reduced latency
- D. reduced fabric link traffic
Answer: CD
NEW QUESTION 12
Refer the Exhibit.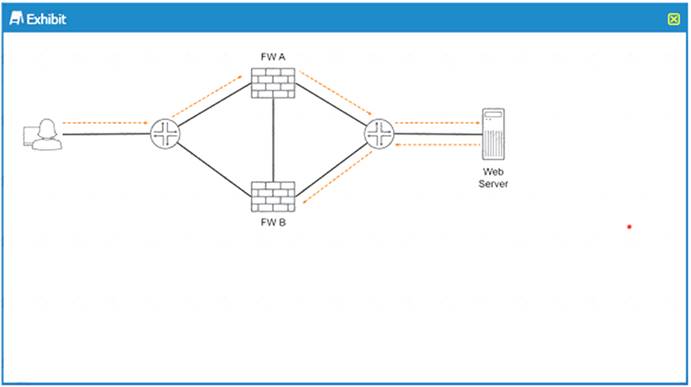
You must ensure that return Web traffic is not dropped by the firewall devices What must be implemented on the link between FW A and FW B?
- A. VRRP
- B. session sync
- C. asymmetric routing
- D. BFO
Answer: A
NEW QUESTION 13
You arc asked to proud a design proposal to secure a service provider's network against IP spoofing As part of your design, you must ensure that only traffic sourced from the same subnet is followed on the
customer-facing interfaces. Which solution will satisfy this requirement?
- A. BGP with source of origin community
- B. unicast RPF with strict mode
- C. unicast RPF with loose mode
- D. BGP labeled-unicast using the resolve-vpn option
Answer: B
NEW QUESTION 14
You want to reduce the possibility of your data center's server becoming an unwilling participant in a DDoS attack When tvA3 features should you use on your SRX Series devices to satisfy this requirement? (Choose two.)
- A. dynamic IPsec tunnels
- B. Juniper ATP Cloud GeolP
- C. UTMWebtaering
- D. Juniper ATP Cloud CC feeds
Answer: AD
NEW QUESTION 15
In yew network design, you must include a method to block IP addresses from certain countries that will automatically update within the SRX Series devices' security policies.
Which technology would accomplish this goal?
- A. UTM
- B. GeolP
- C. dynamic DNS
- D. IPS
Answer: C
NEW QUESTION 16
When designing security for the service provider WAN. you are asked to implement unicast reverse path forwarding (uRPF) in this scenario. on which interfaces would you choose to implement loose mode uRPF?
- A. On interfaces where the best forwarding path fee routes is through the receiving interface
- B. On interfaces that are user access interfaces
- C. On interfaces where all data originates on the same network as that of the router interface
- D. On interfaces that participate in multihomes environments
Answer: B
NEW QUESTION 17
......
100% Valid and Newest Version JN0-1332 Questions & Answers shared by Dumpscollection.com, Get Full Dumps HERE: https://www.dumpscollection.net/dumps/JN0-1332/ (New 65 Q&As)