Our pass rate is high to 98.9% and the similarity percentage between our MS-500 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the Microsoft MS-500 exam in just one try? I am currently studying for the Microsoft MS-500 exam. Latest Microsoft MS-500 Test exam practice questions and answers, Try Microsoft MS-500 Brain Dumps First.
Also have MS-500 free dumps questions for you:
NEW QUESTION 1
HOTSPOT
You have a Microsoft 365 subscription.
You create a retention label named Label1 as shown in the following exhibit.
You publish Label1 to SharePoint sites.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.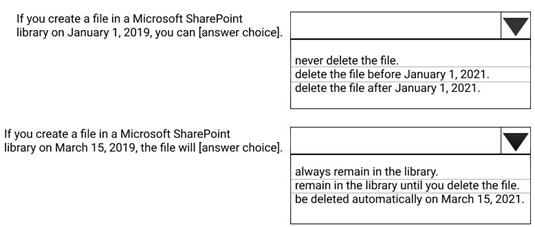
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/labels
NEW QUESTION 2
HOTSPOT
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
You create and enforce an Azure AD Identity Protection sign-in risk policy that has the following settings:
•Assignments: Include Group1, Exclude Group2
•Conditions: Sign in risk of Low and above
•Access: Allow access, Require password multi-factor authentication You need to identify how the policy affects User1 and User2.
What occurs when each user signs in from an anonymous IP address? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.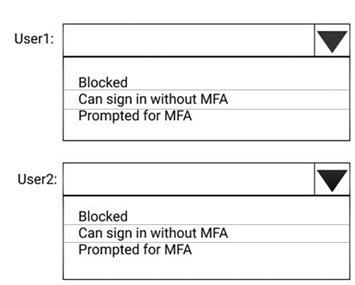
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 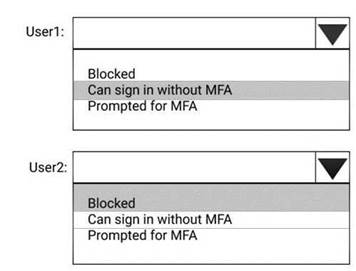
NEW QUESTION 3
HOTSPOT
You have a Microsoft 365 subscription. Auditing is enabled.
A user named User1 is a member of a dynamic security group named Group1. You discover that User1 is no longer a member of Group1.
You need to search the audit log to identify why User1 was removed from Group1.
Which two actions should you use in the search? To answer, select the appropriate activities in the answer area.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/search-the-audit-log-in-security-and-compliance
NEW QUESTION 4
You need to resolve the issue that targets the automated email messages to the IT team. Which tool should you run first?
- A. Synchronization Service Manager
- B. Azure AD Connect wizard
- C. Synchronization Rules Editor
- D. IdFix
Answer: B
Explanation:
References:
https://docs.microsoft.com/en-us/office365/enterprise/fix-problems-with-directory-synchronization
Case Study: 2 Litware, Inc Overview
Litware, Inc. is a financial company that has 1,000 users in its main office in Chicago and 100 users in
a branch office in San Francisco.
Existing Environment
Internal Network Infrastructure
The network contains a single domain forest. The forest functional level is Windows Server 2021. Users are subject to sign-in hour restrictions as defined in Active Directory.
The network has the IP address range shown in the following table.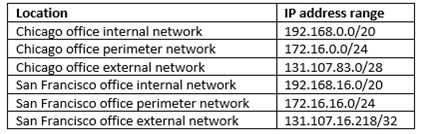
The offices connect by using Multiprotocol Label Switching (MPLS).
The following operating systems are used on the network:
•Windows Server 2021
•Windows 10 Enterprise
•Windows 8.1 Enterprise
The internal network contains the systems shown in the following table.
Litware uses a third-party email system.
Cloud Infrastructure
Litware recently purchased Microsoft 365 subscription licenses for all users.
Microsoft Azure Active Directory (Azure AD) Connect is installed and uses the default authentication settings. User accounts are not yet synced to Azure AD.
You have the Microsoft 365 users and groups shown in the following table.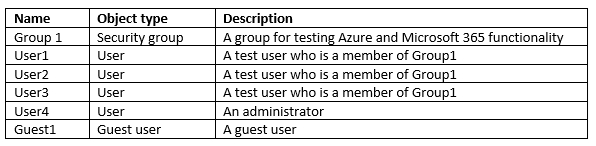
Planned Changes
Litware plans to implement the following changes: Migrate the email system to Microsoft Exchange Online Implement Azure AD Privileged Identity Management Security Requirements
Litware identities the following security requirements:
•Create a group named Group2 that will include all the Azure AD user accounts. Group2 will be used to provide limited access to Windows Analytics
•Create a group named Group3 that will be used to apply Azure Information Protection policies to pilot users. Group3 must only contain user accounts
•Use Azure Advanced Threat Protection (ATP) to detect any security threats that target the forest
•Prevent users locked out of Active Directory from signing in to Azure AD and Active Directory
•Implement a permanent eligible assignment of the Compliance administrator role for User1
•Integrate Windows Defender and Windows Defender ATP on domain-joined servers
•Prevent access to Azure resources for the guest user accounts by default
•Ensure that all domain-joined computers are registered to Azure AD
Multi-factor authentication (MFA) Requirements
Security features of Microsoft Office 365 and Azure will be tested by using pilot Azure user accounts. You identify the following requirements for testing MFA.
Pilot users must use MFA unless they are signing in from the internal network of the Chicago office. MFA must NOT be used on the Chicago office internal network.
If an authentication attempt is suspicious, MFA must be used, regardless of the user location Any disruption of legitimate authentication attempts must be minimized
General Requirements
Litware want to minimize the deployment of additional servers and services in the Active Directory forest.
NEW QUESTION 5
DRAG DROP
You have a Microsoft 365 E5 subscription.
All computers run Windows 10 and are onboarded to Windows Defender Advanced Threat Protection (Windows Defender ATP).
You create a Windows Defender machine group named MachineGroupl.
You need to enable delegation for the security settings of the computers in MachineGroupl.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.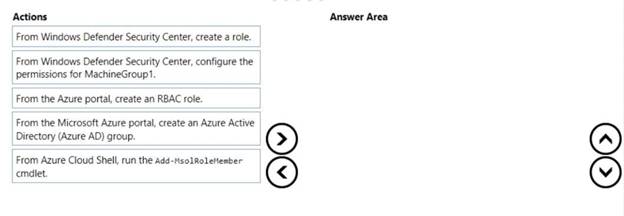
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 6
HOTSPOT
Your company has a Microsoft 365 subscription, a Microsoft Azure subscription, and an Azure Active Directory (Azure AD) tenant named contoso.com.
The company has the offices shown in the following table.
The tenant contains the users shown in the following table.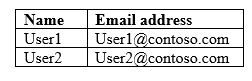
You create the Microsoft Cloud App Security policy shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 7
Note: This question is part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that is associated to a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You use Active Directory Federation Services (AD FS) to federate on-premises Active Directory and the tenant. Azure AD Connect has the following settings:
•Source Anchor: objectGUID
•Password Hash Synchronization: Disabled
•Password writeback: Disabled
•Directory extension attribute sync: Disabled
•Azure AD app and attribute filtering: Disabled
•Exchange hybrid deployment: Disabled
•User writeback: Disabled
You need to ensure that you can use leaked credentials detection in Azure AD Identity Protection. Solution: You modify the Azure AD app and attribute filtering settings.
Does that meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 8
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these
questions will not appear in the review screen.
You have a Microsoft 365 subscription that contains the users shown in the following table.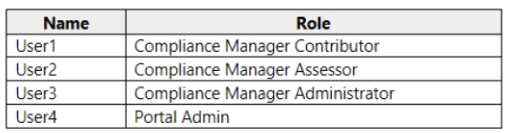
You discover that all the users in the subscription can access Compliance Manager reports. The Compliance Manager Reader role is not assigned to any users.
You need to recommend a solution to prevent a user named User5 from accessing the Compliance Manager reports.
Solution: You recommend assigning the Compliance Manager Reader role to User1. Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 9
You have a Microsoft 365 subscription that includes a user named Admin1.
You need to ensure that Admin1 can preserve all the mailbox content of users, including their deleted items.
The solution must use the principle of least privilege. What should you do?
- A. From the Microsoft 365 admin center, assign the Exchange administrator role to Admin1.
- B. From the Exchange admin center, assign the Discovery Management admin role to Admin1.
- C. From the Azure Active Directory admin center, assign the Service administrator role to Admin1.
- D. From the Exchange admin center, assign the Recipient Management admin role to Admin1.
Answer: B
NEW QUESTION 10
HOTSPOT
You are evaluating which devices are compliant in Intune.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 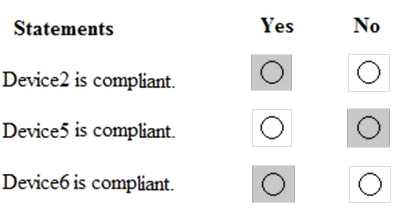
NEW QUESTION 11
You have a Microsoft 365 subscription.
You need to ensure that all users who are assigned the Exchange administrator role have multi-factor authentication (MFA) enabled by default.
What should you use to achieve the goal?
- A. Security & Compliance permissions
- B. Microsoft Azure Active Directory (Azure AD) Privileged Identity Management
- C. Microsoft Azure AD group management
- D. Microsoft Office 365 user management
Answer: B
NEW QUESTION 12
HOTSPOT
You have a Microsoft 365 subscription that uses a default domain name of contoso.com. Microsoft Azure Active Directory (Azure AD) contains the users shown in the following table.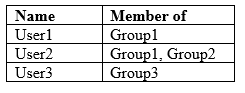
Microsoft Intune has two devices enrolled as shown in the following table:
Both devices have three apps named App1, App2, and App3 installed.
You create an app protection policy named ProtectionPolicy1 that has the following settings:
•Protected apps: App1
•Exempt apps: App2
•Windows Information Protection mode: Block
You apply ProtectionPolicy1 to Group1 and Group3. You exclude Group2 from ProtectionPolicy1. For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.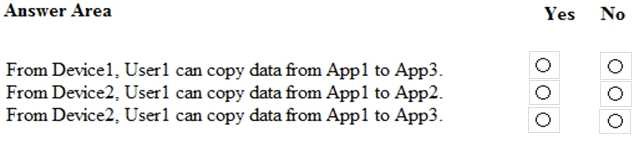
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 13
Your network contains an on-premises Active Directory domain. The domain contains servers that run
Windows Server and have advanced auditing enabled.
The security logs of the servers are collected by using a third-party SIEM solution.
You purchase a Microsoft 365 subscription and plan to deploy Azure Advanced Threat Protection (ATP) by using standalone sensors.
You need to ensure that you can detect when sensitive groups are modified and when malicious services are created.
What should you do?
- A. Configure auditing in the Office 365 Security & Compliance center.
- B. Turn off Delayed updates for the Azure ATP sensors.
- C. Modify the Domain synchronizer candidate’s settings on the Azure ATP sensors.
- D. Integrate SIEM and Azure ATP.
Answer: C
Explanation:
References:
https://docs.microsoft.com/en-us/azure-advanced-threat-protection/install-atp-step5
NEW QUESTION 14
You have a Microsoft 365 subscription.
You create an Advanced Threat Protection (ATP) safe attachments policy.
You need to configure the retention duration for the attachments in quarantine. Which type of threat management policy should you create?
- A. Anti-malware
- B. DKIM
- C. Anti-spam
- D. ATP anti-phishing
Answer: A
NEW QUESTION 15
You have a Microsoft 365 subscription.
A security manager receives an email message every time a data loss prevention (DLP) policy match occurs.
You need to limit alert notifications to actionable DLP events.
What should you do?
- A. From the Security & Compliance admin center, modify the Policy Tips of a DLP policy.
- B. From the Cloud App Security admin center, apply a filter to the alerts.
- C. From the Security & Compliance admin center, modify the User overrides settings of a DLP policy.
- D. From the Security & Compliance admin center, modify the matched activities threshold of an alert policy.
Answer: D
Explanation:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/alert-policies
NEW QUESTION 16
You have a Microsoft 365 subscription. You enable auditing for the subscription.
You plan to provide a user named Auditor with the ability to review audit logs. You add Auditor to the Global administrator role group.
Several days later, you discover that Auditor disabled auditing.
You remove Auditor from the Global administrator role group and enable auditing.
- A. Security operator
- B. Security reader
- C. Security administrator
- D. Compliance administrator
Answer: D
NEW QUESTION 17
You need to recommend a solution that meets the technical and security requirements for sharing data with the partners.
What should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A. Create an access review.
- B. Assign the Global administrator role to User1.
- C. Assign the Guest inviter role to User1.
- D. Modify the External collaboration settings in the Azure Active Directory admin center.
Answer: AC
NEW QUESTION 18
Which role should you assign to User1?
- A. Global administrator
- B. User administrator
- C. Privileged role administrator
- D. Security administrator
Answer: D
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-how-to-give-access-to-pim
NEW QUESTION 19
Your company uses Microsoft Azure Advanced Threat Protection (ATP).
You enable the delayed deployment of updates for an Azure ATP sensor named Sensor1. How long after the Azure ATP cloud service is updated will Sensor1 be updated?
- A. 7 days
- B. 24 hours
- C. 1 hour
- D. 48 hours
- E. 12 hours
Answer: B
Explanation:
Note: The delay period was 24 hours. In ATP release 2.62, the 24 hour delay period has been increased to 72 hours.
NEW QUESTION 20
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription that contains the users shown in the following table.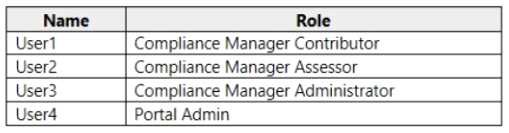
You discover that all the users in the subscription can access Compliance Manager reports. The Compliance Manager Reader role is not assigned to any users.
You need to recommend a solution to prevent a user named User5 from accessing the Compliance Manager reports.
Solution: You recommend assigning the Compliance Manager Reader role to User5. Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 21
DRAG DROP
You have a Microsoft 365 subscription.
You have a site collection named SiteCollection1 that contains a site named Site2. Site2 contains a document library named Customers.
Customers contains a document named Litware.docx. You need to remove Litware.docx permanently.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 22
You have a Microsoft 365 E5 subscription and a hybrid Microsoft Exchange Server organization.
Each member of a group named Executive has an on-premises mailbox. Only the Executive group members have multi-factor authentication (MFA) enabled. Each member of a group named Research has a mailbox in Exchange Online.
You need to use Microsoft Office 365 Attack simulator to model a spear-phishing attack that targets the Research group members.
The email address that you intend to spoof belongs to the Executive group members. What should you do first?
- A. From Azure ATP admin center, configure the primary workspace settings
- B. From the Microsoft Azure portal, configure the user risk settings in Azure AD Identity Protection
- C. Enable MFA for the Research group members
- D. Migrate the Executive group members to Exchange Online
Answer: C
Explanation:
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/attack-simulator
NEW QUESTION 23
......
100% Valid and Newest Version MS-500 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/MS-500-dumps.html (New 114 Q&As)