Testking offers free demo for NSE4_FGT-6.0 exam. "Fortinet NSE 4 – FortiOS 6.0", also known as NSE4_FGT-6.0 exam, is a Fortinet Certification. This set of posts, Passing the Fortinet NSE4_FGT-6.0 exam, will help you answer those questions. The NSE4_FGT-6.0 Questions & Answers covers all the knowledge points of the real exam. 100% real Fortinet NSE4_FGT-6.0 exams and revised by experts!
NEW QUESTION 1
An administrator has configured central DNAT and virtual IPs. Which of the following can be selected in the firewall policy Destination field?
- A. A VIP group
- B. The mapped IP address object of the VIP object
- C. A VIP object
- D. An IP pool
Answer: C
NEW QUESTION 2
Examine the two static routes shown in the exhibit, then answer title following question.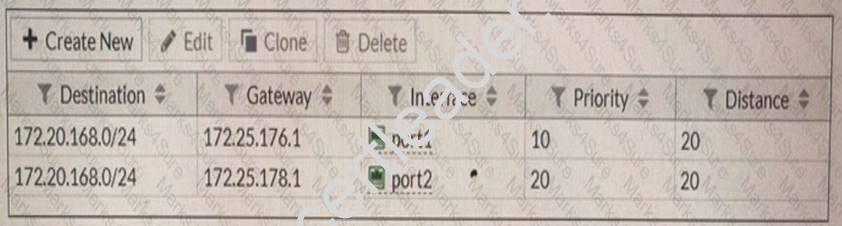
Which of the following is the expected FortiGate behavior regarding these two routes to the same destination?
- A. FortiGate will load balance all traffic across both routes.
- B. FortiGate will use the port1 route as the primary candidate.
- C. FortiGate will route twice as much traffic to the port2 route
- D. FortiGate will only actuate the portl route m tlie routing table
Answer: C
NEW QUESTION 3
Examine the exhibit, which contains a session diagnostic output.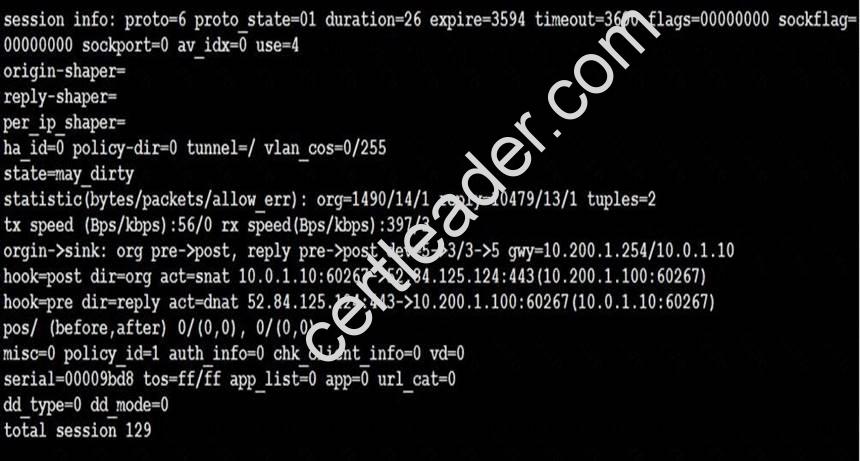
Which of the following statements about the session diagnostic output is true?
- A. The session is in ESTABLISHED state.
- B. The session is in LISTEN state.
- C. The session is in TIME_WAIT state.
- D. The session is in CLOSE_WAIT state.
Answer: A
NEW QUESTION 4
Which is a requirement for creating an inter-VDOM link between two VDOMs?
- A. The inspection mode of at least one VDOM must be proxy-based.
- B. At least one of the VDOMs must operate in NAT mode.
- C. The inspection mode of both VDOMs must match.
- D. Both VDOMs must operate in NAT mode.
Answer: A
NEW QUESTION 5
What is the limitation of using a URL list and application control on the same firewall policy, in NCFW policy-based mode?
- A. It limits the scope of application control to the browser-based technology category only.
- B. It limits the scope of application control to scan application traffic based on application category only.
- C. It limits the scope of application control to scan application traffic using parent signatures only
- D. It limits the scope of application control to scan application traffic on DNS protocol only.
Answer: D
NEW QUESTION 6
If the Issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
- A. A CRL
- B. A person
- C. A subordinate CA
- D. A root CA
Answer: D
NEW QUESTION 7
An administrator has configured a dialup IPsec VPN with XAuth. Which statement best describes what occurs during this scenario?
- A. Phase 1 negotiations will skip preshared key exchange.
- B. Only digital certificates will be accepted as an authentication method in phase 1.C
- C. Dialup clients must provide a username and password for authentication.
- D. Dialup clients must provide their local ID during phase 2 negotiations.
Answer: C
NEW QUESTION 8
Which of the following statements about virtual domains (VDOMs) are true? (Choose two.)
- A. The root VDOM is the management VDOM by default.
- B. A FortiGate device has 64 VDOMs, created by default.
- C. Each VDOM maintains its own system time.
- D. Each VDOM maintains its own routing table.
Answer: AD
NEW QUESTION 9
Examine this PAC file configuration.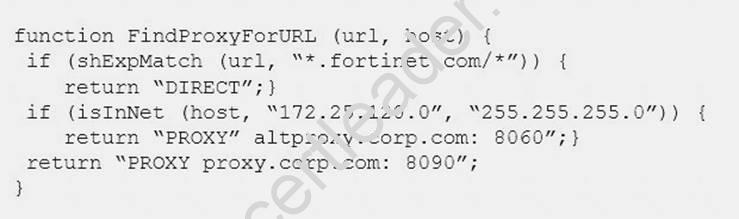
Which of the following statements are true? (Choose two.)
- A. Browsers can be configured to retrieve this PAC file from the FortiGate.
- B. Any web request to the 172.25.120.0/24 subnet is allowed to bypass the proxy.
- C. All requests not made to Fortinet.com or the 172.25.120.0/24 subnet, have to go through altproxy.corp.com: 8060.
- D. Any web request fortinet.com is allowed to bypass the proxy.
Answer: AD
NEW QUESTION 10
When using SD-WAN, how do you configure the next-hop gateway address for a member interface so that FortiGate can forward Internet traffic?
- A. It must be configured in a static route using the sdwan virtual interface.
- B. It must be provided in the SD-WAN member interface configuration.
- C. It must be configured in a policy-route using the sdwan virtual interface.
- D. It must be learned automatically through a dynamic routing protocol.
Answer: A
NEW QUESTION 11
View the following exhibit, which shows the firewall policies and the object uses in the firewall policies.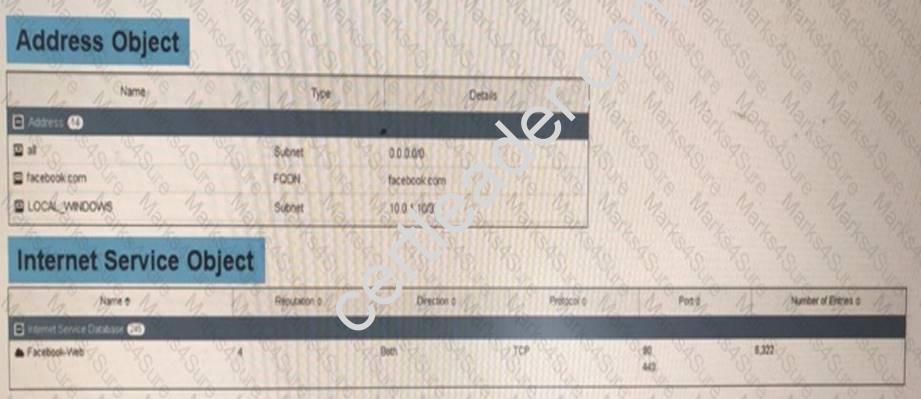
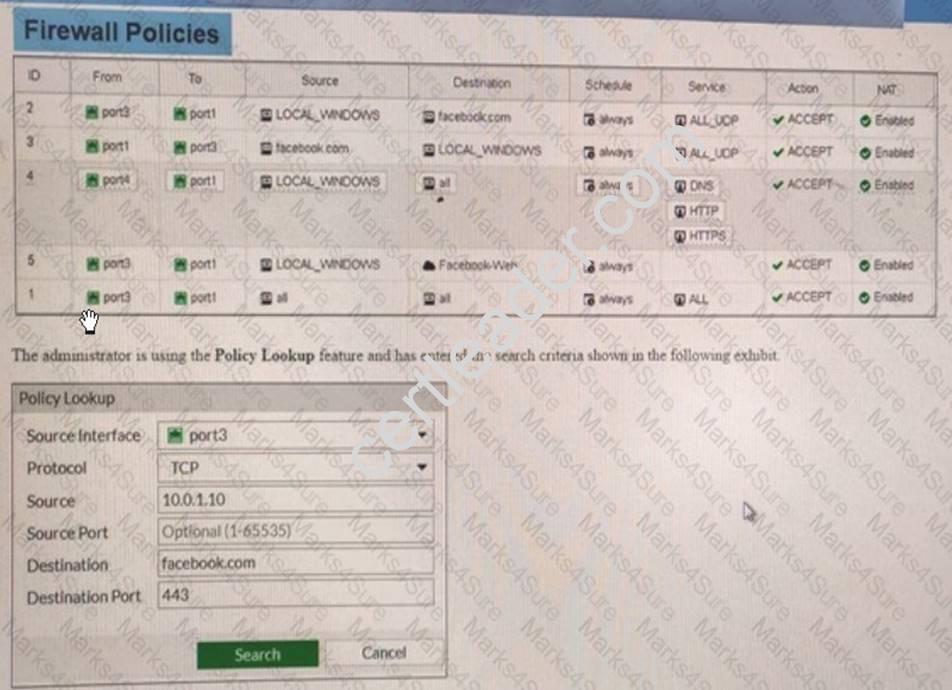
The administrator is using the Policy Lookup feature and has entered the search create shown in the following exhibit.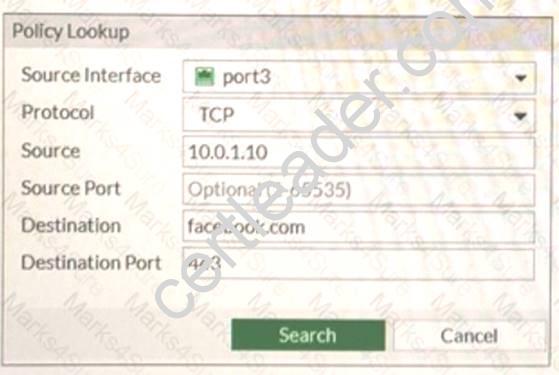
Which of the following will be highlighted based oil the input criteria?
- A. Policy with ID 1.
- B. Policies with ID 2 and 3.
- C. Policy with ID 5.
- D. Policy with ID 4
Answer: B
NEW QUESTION 12
Which of the following SD-WAN load –balancing method use interface weight value to distribute traffic? (Choose two.)
- A. Source IP
- B. Spillover
- C. Volume
- D. Session
Answer: CD
NEW QUESTION 13
On a FortiGate with a hard disk, how can you upload logs to FortiAnalyzer or FortiManager? (Choose two.)
- A. hourly
- B. real tune
- C. on-demand
- D. store-and-upload
Answer: BD
NEW QUESTION 14
NGFW mode allows policy-based configuration for most inspection rules. Which security profile’s configuration does not change when you enable policy-based inspection?
- A. Web filtering
- B. Antivirus
- C. Web proxy
- D. Application control
Answer: C
NEW QUESTION 15
How does FortiGate verify the login credentials of a remote LDAP user?
- A. FortiGate regenerates the algorithm based on the login credentials and compares it to the algorithm stored on the LDAP server.
- B. FortiGate sends the user-entered credentials to the LDAP server for authentication.
- C. FortiGate queries the LDAP server for credentials.
- D. FortiGate queries its own database for credentials.
Answer: B
NEW QUESTION 16
What FortiGate components are tested during the hardware test? (Choose three.)
- A. Administrative access
- B. HA heartbeat
- C. CPU
- D. Hard disk
- E. Network interfaces
Answer: CDE
NEW QUESTION 17
View the certificate shown to the exhibit, and then answer the following question: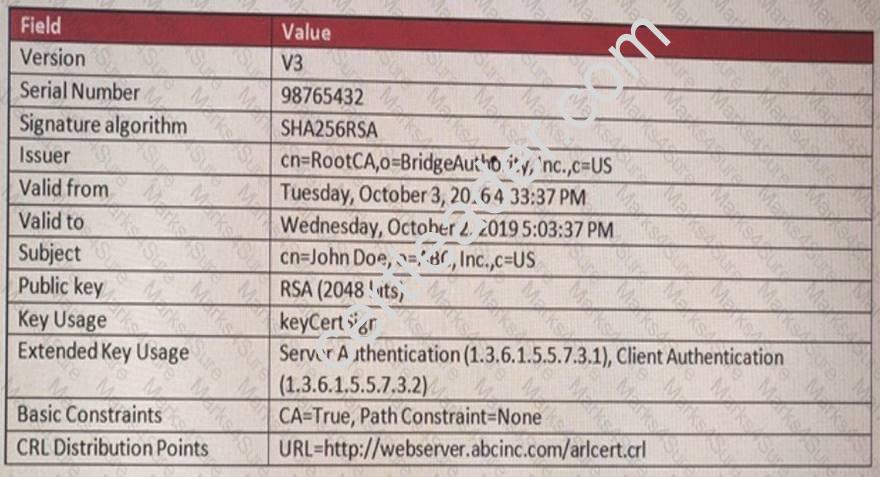
The CA issued this certificate to which entity?
- A. A root CA
- B. A person
- C. A bridge CA
- D. A subordinate CA
Answer: A
NEW QUESTION 18
Examine the routing database shown in the exhibit, and then answer the following question: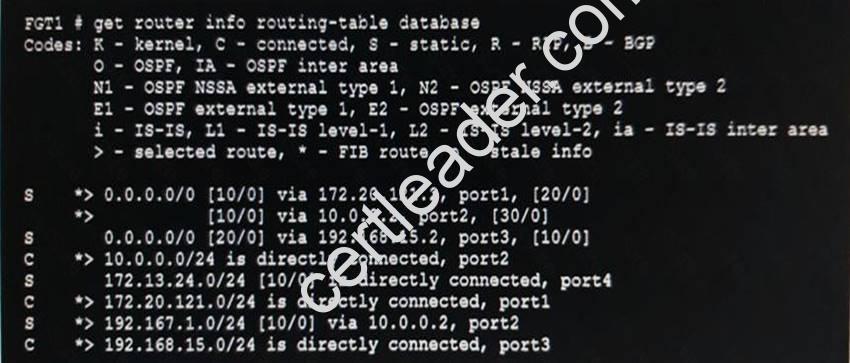
Which of the following statements are correct? (Choose two.)
- A. The port3 default route has the highest distance.
- B. The port3 default route has the lowest metric.
- C. There will be eight routes active in the routing table.
- D. The port1 and port2 default routes are active in the routing table.
Answer: AD
NEW QUESTION 19
Which configuration objects can be selected for the Source field of a firewall policy? (Choose two.)
- A. Firewall service
- B. User or user group
- C. IP Pool
- D. FQDN address
Answer: BC
NEW QUESTION 20
Which of the following route attributes must be equal for static routes to be eligible for equal cost multipath (ECMP) routing? (Choose two.)
- A. Priority
- B. Metric
- C. Distance
- D. Cost
Answer: AC
NEW QUESTION 21
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
- A. The firmware image must be manually uploaded to each FortiGate.
- B. Only secondary FortiGate devices are rebooted.
- C. Uninterruptable upgrade is enabled by default.
- D. Traffic load balancing is temporally disabled while upgrading the firmware.
Answer: BD
NEW QUESTION 22
View the exhibit.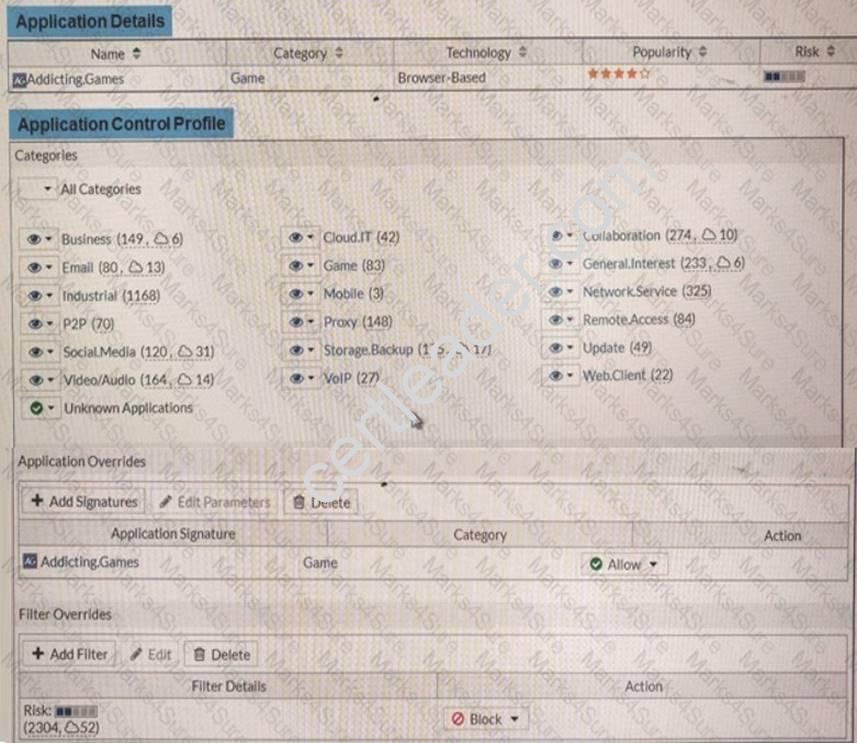
A user behind the FortiGate is trying to go to http://www.addictinggames.com (Addicting.Games). Based on this configuration, which statement is true?
- A. Addicting.Games is allowed based on the Application Overrides configuration.
- B. Addicting.Games is blocked based on the Filter Overrides configuration.
- C. Addicting.Games can be allowed only if the Filter Overrides actions is set to Exempt.
- D. Addicting.Games is allowed based on the Categories configuration.
Answer: A
NEW QUESTION 23
Examine this output from a debug flow: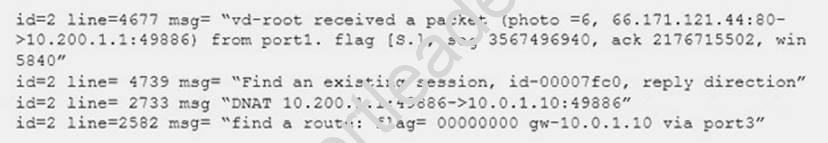
Which statements about the output are correct? (Choose two.)
- A. FortiGate received a TCP SYN/ACK packet.
- B. The source IP address of the packet was translated to 10.0.1.10.
- C. FortiGate routed the packet through port 3.
- D. The packet was allowed by the firewall policy with the ID 00007fc0.
Answer: AC
NEW QUESTION 24
......
100% Valid and Newest Version NSE4_FGT-6.0 Questions & Answers shared by Certstest, Get Full Dumps HERE: https://www.certstest.com/dumps/NSE4_FGT-6.0/ (New 126 Q&As)