Precise of NSE4_FGT-7.0 actual exam materials and test preparation for Fortinet certification for customers, Real Success Guaranteed with Updated NSE4_FGT-7.0 pdf dumps vce Materials. 100% PASS Fortinet NSE 4 - FortiOS 7.0 exam Today!
Free NSE4_FGT-7.0 Demo Online For Fortinet Certifitcation:
NEW QUESTION 1
Which statements best describe auto discovery VPN (ADVPN). (Choose two.)
- A. It requires the use of dynamic routing protocols so that spokes can learn the routes to other spokes.
- B. ADVPN is only supported with IKEv2.
- C. Tunnels are negotiated dynamically between spokes.
- D. Every spoke requires a static tunnel to be configured to other spokes so that phase 1 and phase 2 proposals are defined in advance.
Answer: AC
NEW QUESTION 2
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for example.com home page, the override must be configured using a specific syntax.
Which two syntaxes are correct to configure web rating for the home page? (Choose two.)
- A. www.example.com:443
- B. www.example.com
- C. example.com
- D. www.example.com/index.html
Answer: BC
Explanation:
FortiGate_Security_6.4 page 384
When using FortiGuard category filtering to allow or block access to a website, one option is to make a web rating override and define the website in a different category. Web ratings are only for host names— "no URLs or wildcard characters are allowed".
NEW QUESTION 3
Which Security rating scorecard helps identify configuration weakness and best practice violations in your network?
- A. Fabric Coverage
- B. Automated Response
- C. Security Posture
- D. Optimization
Answer: C
Explanation:
Reference:
https://www.fortinet.com/content/dam/fortinet/assets/support/fortinet-recommended-security-bestpractices.pdf
NEW QUESTION 4
Which two statements are true about collector agent advanced mode? (Choose two.)
- A. Advanced mode uses Windows convention—NetBios: Domain\Username.
- B. FortiGate can be configured as an LDAP client and group filters can be configured on FortiGate
- C. Advanced mode supports nested or inherited groups
- D. Security profiles can be applied only to user groups, not individual users.
Answer: BC
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.0.0/handbook/482937/agent-based-fsso
NEW QUESTION 5
Which two statements about SSL VPN between two FortiGate devices are true? (Choose two.)
- A. The client FortiGate requires a client certificate signed by the CA on the server FortiGate.
- B. The client FortiGate requires a manually added route to remote subnets.
- C. The client FortiGate uses the SSL VPN tunnel interface type to connect SSL VPN.
- D. Server FortiGate requires a CA certificate to verify the client FortiGate certificate.
Answer: CD
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.9/cookbook/266506/ssl-vpn-with-certificate-authentication
NEW QUESTION 6
An administrator has configured two-factor authentication to strengthen SSL VPN access. Which additional best practice can an administrator implement?
- A. Configure Source IP Pools.
- B. Configure split tunneling in tunnel mode.
- C. Configure different SSL VPN realms.
- D. Configure host check.
Answer: D
NEW QUESTION 7
Refer to the exhibit.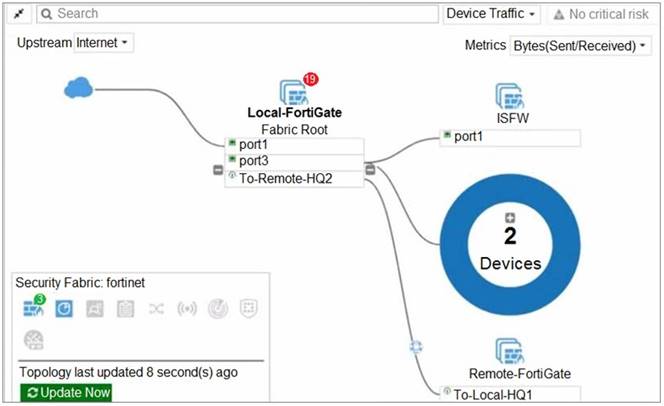
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)
- A. There are five devices that are part of the security fabric.
- B. Device detection is disabled on all FortiGate devices.
- C. This security fabric topology is a logical topology view.
- D. There are 19 security recommendations for the security fabric.
Answer: CD
Explanation:
References: https://docs.fortinet.com/document/fortigate/5.6.0/cookbook/761085/results
https://docs.fortinet.com/document/fortimanager/6.2.0/new-features/736125/security-fabric-topology
NEW QUESTION 8
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
- A. diagnose wad session list
- B. diagnose wad session list | grep hook-pre&&hook-out
- C. diagnose wad session list | grep hook=pre&&hook=out
- D. diagnose wad session list | grep "hook=pre"&"hook=out"
Answer: A
NEW QUESTION 9
Refer to the exhibit.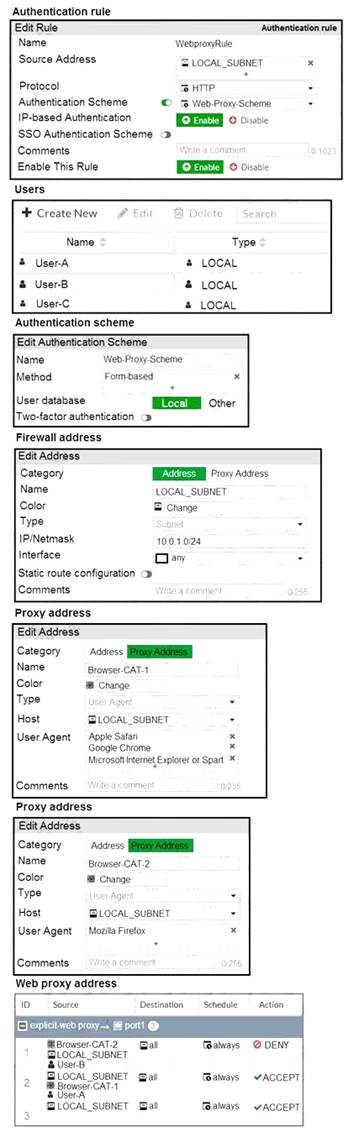
The exhibit shows proxy policies and proxy addresses, the authentication rule and authentication scheme, users, and firewall address.
An explicit web proxy is configured for subnet range 10.0.1.0/24 with three explicit web proxy policies. The authentication rule is configured to authenticate HTTP requests for subnet range 10.0.1.0/24 with a
form-based authentication scheme for the FortiGate local user database. Users will be prompted for
authentication.
How will FortiGate process the traffic when the HTTP request comes from a machine with the source IP 10.1.1.10 to the destination http://www.fortinet.com? (Choose two.)
- A. If a Mozilla Firefox browser is used with User-B credentials, the HTTP request will be allowed.
- B. If a Google Chrome browser is used with User-B credentials, the HTTP request will be allowed.
- C. If a Mozilla Firefox browser is used with User-A credentials, the HTTP request will be allowed.
- D. If a Microsoft Internet Explorer browser is used with User-B credentials, the HTTP request will be allowed.
Answer: BD
NEW QUESTION 10
Refer to the exhibit.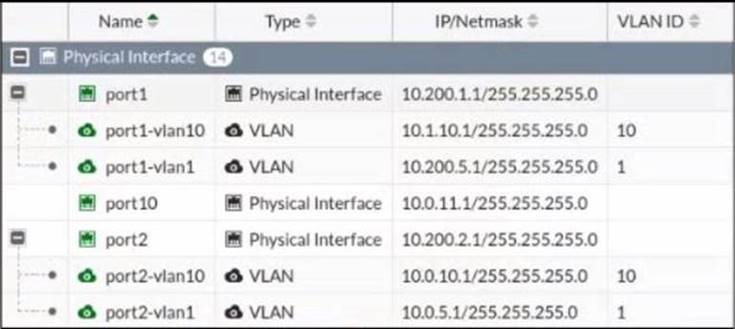
Given the interfaces shown in the exhibit. which two statements are true? (Choose two.)
- A. Traffic between port2 and port2-vlan1 is allowed by default.
- B. port1-vlan10 and port2-vlan10 are part of the same broadcast domain.
- C. port1 is a native VLAN.
- D. port1-vlan and port2-vlan1 can be assigned in the same VDOM or to different VDOMs.
Answer: CD
Explanation:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-rules-about-VLAN-configuration-and-VDOM-interf https://kb.fortinet.com/kb/viewContent.do?externalId=FD30883
NEW QUESTION 11
If Internet Service is already selected as Destination in a firewall policy, which other configuration objects can be selected to the Destination field of a firewall policy?
A User or User Group
- A. IP address
- B. No other object can be added
- C. FQDN address
Answer: B
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.5/cookbook/179236/using-internet-service-in-policy
NEW QUESTION 12
In which two ways can RPF checking be disabled? (Choose two )
- A. Enable anti-replay in firewall policy.
- B. Disable the RPF check at the FortiGate interface level for the source check
- C. Enable asymmetric routing.
- D. Disable strict-arc-check under system settings.
Answer: CD
Explanation:
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD33955
NEW QUESTION 13
Which two attributes are required on a certificate so it can be used as a CA certificate on SSL Inspection? (Choose two.)
- A. The keyUsage extension must be set to keyCertSign.
- B. The common name on the subject field must use a wildcard name.
- C. The issuer must be a public CA.
- D. The CA extension must be set to TRUE.
Answer: AD
Explanation:
Reference: https://www.reddit.com/r/fortinet/comments/c7j6jg/recommended_ssl_cert/
NEW QUESTION 14
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
- A. The subject field in the server certificate
- B. The serial number in the server certificate
- C. The server name indication (SNI) extension in the client hello message
- D. The subject alternative name (SAN) field in the server certificate
- E. The host field in the HTTP header
Answer: ACD
Explanation:
Reference: https://checkthefirewall.com/blogs/fortinet/ssl-inspection
NEW QUESTION 15
Refer to the exhibit.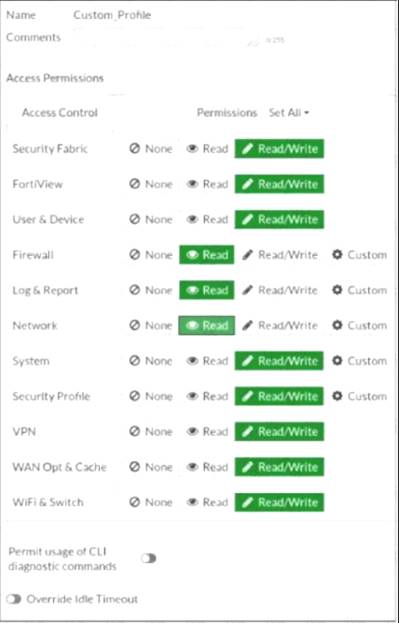
Based on the administrator profile settings, what permissions must the administrator set to run the diagnose firewall auth list CLI command on FortiGate?
- A. Custom permission for Network
- B. Read/Write permission for Log & Report
- C. CLI diagnostics commands permission
- D. Read/Write permission for Firewall
Answer: C
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD50220
NEW QUESTION 16
Which statement about video filtering on FortiGate is true?
- A. Full SSL Inspection is not required.
- B. It is available only on a proxy-based firewall policy.
- C. It inspects video files hosted on file sharing services.
- D. Video filtering FortiGuard categories are based on web filter FortiGuard categories.
Answer: B
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/7.0.0/new-features/190873/video-filtering
NEW QUESTION 17
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)
- A. SSH
- B. HTTPS
- C. FTM
- D. FortiTelemetry
Answer: AB
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.4.0/hardening-your-fortigate/995103/buildingsecurity-into-fortios
NEW QUESTION 18
An administrator has configured a route-based IPsec VPN between two FortiGate devices. Which statement about this IPsec VPN configuration is true?
- A. A phase 2 configuration is not required.
- B. This VPN cannot be used as part of a hub-and-spoke topology.
- C. A virtual IPsec interface is automatically created after the phase 1 configuration is completed.
- D. The IPsec firewall policies must be placed at the top of the list.
Answer: C
Explanation:
In a route-based configuration, FortiGate automatically adds a virtual interface eith the VPN name (Infrastructure Study Guide, 206)
NEW QUESTION 19
If the Issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
- A. A CRL
- B. A person
- C. A subordinate CA
- D. A root CA
Answer: D
NEW QUESTION 20
......
Recommend!! Get the Full NSE4_FGT-7.0 dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/NSE4_FGT-7.0-pdf-download.html (New 172 Q&As Version)