Proper study guides for Leading Juniper Security, Specialist (JNCIS-SEC) certified begins with Juniper jn0-333 preparation products which designed to deliver the Exact jn0-333 questions by making you pass the jn0-333 test at your first time. Try the free jn0-333 demo right now.
Also have jn0-333 free dumps questions for you:
NEW QUESTION 1
Click the Exhibit button.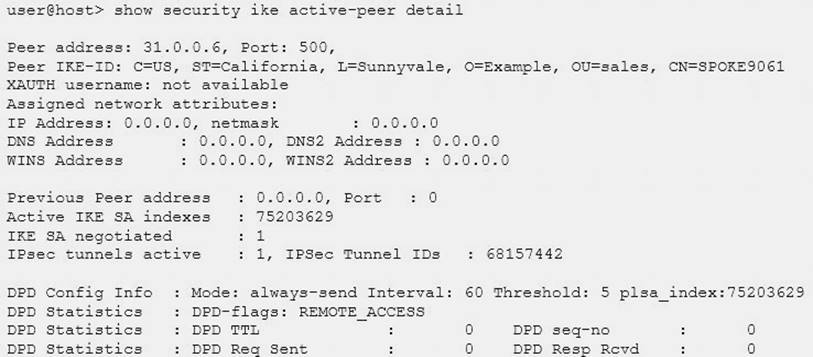
A customer would like to monitor their VPN using dead peer detection.
Referring to the exhibit, for how many minutes was the peer down before the customer was notified?
- A. 5
- B. 3
- C. 4
- D. 2
Answer: A
NEW QUESTION 2
Which two statements about security policy actions are true? (Choose two.)
- A. The log action implies an accept action.
- B. The log action requires an additional terminating action.
- C. The count action implies an accept action.
- D. The count action requires an additional terminating action.
Answer: BD
NEW QUESTION 3
Click the Exhibit button.
Which statement would explain why the IP-monitoring feature is functioning incorrectly?
- A. The global weight value is too large for the configured global threshold.
- B. The secondary IP address should be on a different subnet than the reth IP address.
- C. The secondary IP address is the same as the reth IP address.
- D. The monitored IP address is not on the same subnet as the reth IP address.
Answer: C
NEW QUESTION 4
What are three valid virtual interface types for a vSRX? (Choose three.)
- A. SR-IOV
- B. fxp0
- C. eth0
- D. VMXNET 3
- E. virtio
Answer: ABD
NEW QUESTION 5
Click the Exhibit button.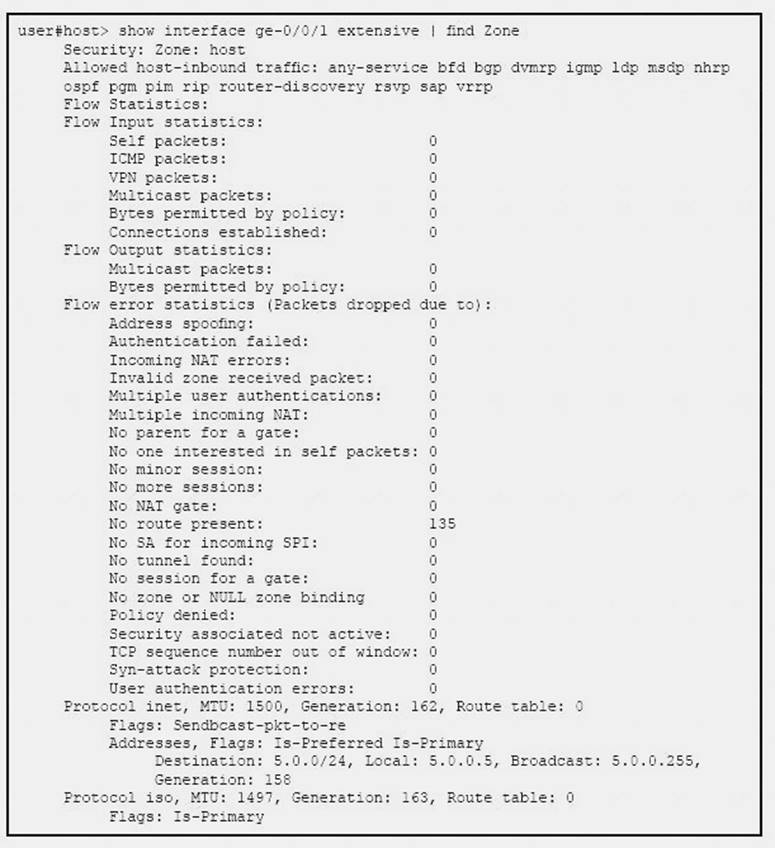
Referring to the exhibit, which statement is true?
- A. TCP packets entering the interface are failing the TCP sequence check.
- B. Packets entering the interface are being dropped due to a stateless filter.
- C. Packets entering the interface are getting dropped because there is no route to the destination.
- D. Packets entering the interface matching an ALG are getting dropped.
Answer: C
NEW QUESTION 6
You want to protect your SRX Series device from the ping-of-death attack coming from the untrust security zone.
How would you accomplish this task?
- A. Configure the host-inbound-traffic system-services ping except parameter in the untrust security zone.
- B. Configure the application tracking parameter in the untrust security zone.
- C. Configure a from-zone untrust to-zone trust security policy that blocks ICMP traffic.
- D. Configure the appropriate screen and apply it to the [edit security zone security-zone untrust] hierarchy.
Answer: D
NEW QUESTION 7
Screens help prevent which three attack types? (Choose three.)
- A. SYN flood
- B. port scan
- C. NTP amplification
- D. ICMP fragmentation
- E. SQL injection
Answer: ABD
NEW QUESTION 8
Which three elements does AH provide in an IPsec implementation? (Choose three.)
- A. confidentiality
- B. authentication
- C. integrity
- D. availability
- E. replay attack protection
Answer: BCE
NEW QUESTION 9
Click to the Exhibit button.
Referring to the exhibit, which two statements are true? (Choose two.)
- A. Interface ge-0/0/0 will not accept SSH connections.
- B. Interfaces ge-0/0/0.0 and ge-0/0/1.0 will allow SSH connections.
- C. Interface ge-0/0/0.0 will respond to pings.
- D. Interface ge-0/0/1.0 will respond to pings.
Answer: BD
NEW QUESTION 10
Click the exhibit button.
Referring to the exhibit, which statement is true?
- A. Packets entering the interface are being dropped because of a stateless filter.
- B. Packets entering the interface matching an ALG are getting dropped.
- C. TCP packets entering the interface are failing the TCP sequence check.
- D. Packets entering the interface are getting dropped because the interface is not bound to a zone.
Answer: D
NEW QUESTION 11
You want to trigger failover of redundancy group 1 currently running on node 0 and make node 1 the primary node the redundancy group 1.
Which command would be used accomplish this task?
- A. user@host# set chassis cluster redundancy-group 1 node 1
- B. user@host> request chassis cluster failover redundancy-group 1 node 1
- C. user@host# set chassis cluster redundancy-group 1 preempt
- D. user@host> request chassis cluster failover reset redundancy-group 1
Answer: B
NEW QUESTION 12
Which interface is used exclusively to forward Ethernet-switching traffic between two chassis cluster nodes?
- A. swfab0
- B. fxp0
- C. fab0
- D. me0
Answer: A
NEW QUESTION 13
What are two fields that an SRX Series device examines to determine if a packet is associated with an existing flow? (Choose two.)
- A. protocol
- B. source IP address
- C. source MAC address
- D. type of service
Answer: AB
NEW QUESTION 14
Which statement is true about high availability (HA) chassis clusters for the SRX Series device?
- A. Cluster nodes require an upgrade to HA compliant Routing Engines.
- B. Cluster nodes must be connected through a Layer 2 switch.
- C. There can be active/passive or active/active clusters.
- D. HA clusters must use NAT to prevent overlapping subnets between the nodes.
Answer: C
NEW QUESTION 15
What is the correct ordering of Junos policy evaluation from first to last?
- A. global policy > zone-based policy > default policy
- B. default policy > zone-based policy > global policy
- C. global policy > default policy > zone-based policy
- D. zone-based policy > global policy > default policy
Answer: D
NEW QUESTION 16
Which host-inbound-traffic security zone parameter would allow access to the REST API configured to listen on custom TCP port 5080?
- A. http
- B. all
- C. xnm-clear-text
- D. any-service
Answer: D
NEW QUESTION 17
What is the function of redundancy group 0 in a chassis cluster?
- A. Redundancy group 0 identifies the node controlling the cluster management interface IP addresses.
- B. The primary node for redundancy group 0 identifies the first member node in a chassis cluster.
- C. The primary node for redundancy group 0 determines the interface naming for all chassis cluster nodes.
- D. The node on which redundancy group 0 is primary determines which Routing Engine is active in the cluster.
Answer: D
NEW QUESTION 18
Which two statements are true about global security policies? (Choose two.)
- A. Global security policies are evaluated before regular security policies.
- B. Global security policies can be configured to match addresses across multiple zones.
- C. Global security policies can match traffic regardless of security zones.
- D. Global security policies do not support IPv6 traffic.
Answer: BC
NEW QUESTION 19
Click the Exhibit button.
Referring to the exhibit, which action will be taken for traffic coming from the untrust zone going to the trust zone?
- A. Source address 2001:db8::8 will be translated to 10.1.1.5.
- B. Source address 2001:db8::8 will be translated to 10.1.1.8.
- C. Source address 10.1.1.8 will be translated to 2001:db8::8.
- D. Source address 10.1.1.5 will be translated to 2001:db8::8.
Answer: B
NEW QUESTION 20
Click the Exhibit button. Referring to the exhibit, what will happen if client 172.16.128.50 tries to connect to destination 192.168.150.3 using HTTP?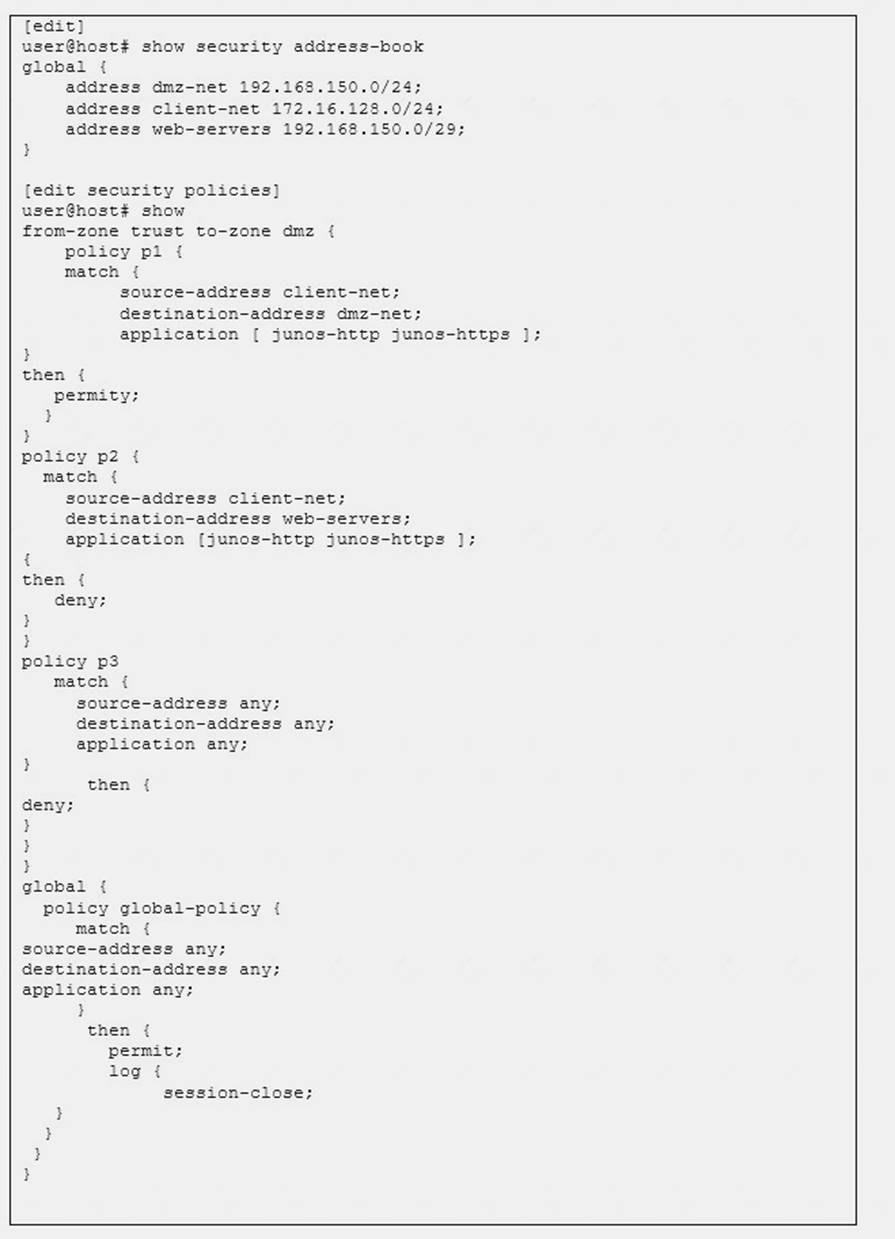
- A. The client will be permitted by policy p1.
- B. The client will be denied by policy p3.
- C. The client will be denied by policy p2.
- D. The client will be permitted by the global policy.
Answer: D
NEW QUESTION 21
......
Recommend!! Get the Full jn0-333 dumps in VCE and PDF From prep-labs.com, Welcome to Download: https://www.prep-labs.com/dumps/jn0-333/ (New 75 Q&As Version)