Guaranteed of CAS-004 answers materials and exam topics for CompTIA certification for IT examinee, Real Success Guaranteed with Updated CAS-004 pdf dumps vce Materials. 100% PASS CompTIA Advanced Security Practitioner (CASP+) Exam exam Today!
Free demo questions for CompTIA CAS-004 Exam Dumps Below:
NEW QUESTION 1
A company created an external application for its customers. A security researcher now reports that the application has a serious LDAP injection vulnerability that could be leveraged to bypass authentication and authorization.
Which of the following actions would BEST resolve the issue? (Choose two.)
- A. Conduct input sanitization.
- B. Deploy a SIEM.
- C. Use containers.
- D. Patch the OS
- E. Deploy a WAF.
- F. Deploy a reverse proxy
- G. Deploy an IDS.
Answer: BD
NEW QUESTION 2
A university issues badges through a homegrown identity management system to all staff and students. Each week during the summer, temporary summer school students arrive and need to be issued a badge to access minimal campus resources.
The security team received a report from an outside auditor indicating the homegrown system is not consistent with best practices in the security field and leaves the institution vulnerable.
Which of the following should the security team recommend FIRST?
- A. Investigating a potential threat identified in logs related to the identity management system
- B. Updating the identity management system to use discretionary access control
- C. Beginning research on two-factor authentication to later introduce into the identity management system
- D. Working with procurement and creating a requirements document to select a new IAM system/vendor
Answer: A
NEW QUESTION 3
A shipping company that is trying to eliminate entire classes of threats is developing an SELinux policy to ensure its custom Android devices are used exclusively for package tracking.
After compiling and implementing the policy, in which of the following modes must the company ensure the devices are configured to run?
- A. Protecting
- B. Permissive
- C. Enforcing
- D. Mandatory
Answer: B
Explanation:
Reference: https://source.android.com/security/selinux/customize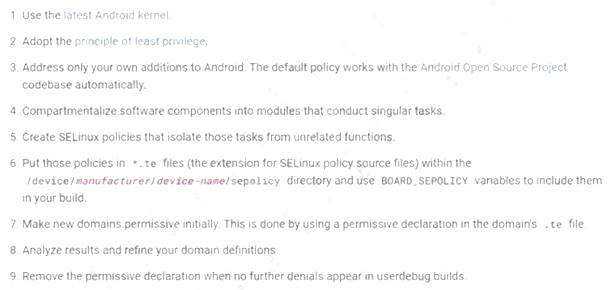
NEW QUESTION 4
A threat hunting team receives a report about possible APT activity in the network. Which of the following threat management frameworks should the team implement?
- A. NIST SP 800-53
- B. MITRE ATT&CK
- C. The Cyber Kill Chain
- D. The Diamond Model of Intrusion Analysis
Answer: A
Explanation:
Reference: https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-30r1.pdf
NEW QUESTION 5
An e-commerce company is running a web server on premises, and the resource utilization is usually less than 30%. During the last two holiday seasons, the server experienced performance issues because of too many connections, and several customers were not able to finalize purchase orders. The company is looking to change the server configuration to avoid this kind of performance issue.
Which of the following is the MOST cost-effective solution?
- A. Move the server to a cloud provider.
- B. Change the operating system.
- C. Buy a new server and create an active-active cluster.
- D. Upgrade the server with a new one.
Answer: A
NEW QUESTION 6
A company has decided to purchase a license for software that is used to operate a mission-critical process. The third-party developer is new to the industry but is delivering what the company needs at this time.
Which of the following BEST describes the reason why utilizing a source code escrow will reduce the operational risk to the company if the third party stops supporting the application?
- A. The company will have access to the latest version to continue development.
- B. The company will be able to force the third-party developer to continue support.
- C. The company will be able to manage the third-party developer’s development process.
- D. The company will be paid by the third-party developer to hire a new development team.
Answer: B
NEW QUESTION 7
An organization recently started processing, transmitting, and storing its customers’ credit card information. Within a week of doing so, the organization suffered a massive breach that resulted in the exposure of the customers’ information.
Which of the following provides the BEST guidance for protecting such information while it is at rest and in transit?
- A. NIST
- B. GDPR
- C. PCI DSS
- D. ISO
Answer: C
Explanation:
Reference: https://en.wikipedia.org/wiki/Payment_Card_Industry_Data_Security_Standard
NEW QUESTION 8
A security analyst is reviewing network connectivity on a Linux workstation and examining the active TCP connections using the command line. Which of the following commands would be the BEST to run to view only active Internet connections?
- A. sudo netstat -antu | grep “LISTEN” | awk ‘{print$5}’
- B. sudo netstat -nlt -p | grep “ESTABLISHED”
- C. sudo netstat -plntu | grep -v “Foreign Address”
- D. sudo netstat -pnut -w | column -t -s $’\w’
- E. sudo netstat -pnut | grep -P ^tcp
Answer: B
Explanation:
Reference: https://www.codegrepper.com/code-examples/shell/netstat+find+port
NEW QUESTION 9
A satellite communications ISP frequently experiences outages and degraded modes of operation over one of its legacy satellite links due to the use of deprecated hardware and software. Three days per week, on average, a contracted company must follow a checklist of 16 different high-latency commands that must be run in serial to restore nominal performance. The ISP wants this process to be automated.
Which of the following techniques would be BEST suited for this requirement?
- A. Deploy SOAR utilities and runbooks.
- B. Replace the associated hardware.
- C. Provide the contractors with direct access to satellite telemetry data.
- D. Reduce link latency on the affected ground and satellite segments.
Answer: A
NEW QUESTION 10
Company A is establishing a contractual with Company B. The terms of the agreement are formalized in a document covering the payment terms, limitation of liability, and intellectual property rights .
Which of the following documents will MOST likely contain these elements?
- A. Company A-B SLA v2.docx
- B. Company A OLA v1b.docx
- C. Company A MSA v3.docx
- D. Company A MOU v1.docx
- E. Company A-B NDA v03.docx
Answer: A
NEW QUESTION 11
A health company has reached the physical and computing capabilities in its datacenter, but the computing demand continues to increase. The infrastructure is fully virtualized and runs custom and commercial healthcare application that process sensitive health and payment information .
Which of the following should the company implement to ensure it can meet the computing demand while complying with healthcare standard for virtualization and cloud computing?
- A. Hybrid IaaS solution in a single-tenancy cloud
- B. Pass solution in a multinency cloud
- C. SaaS solution in a community cloud
- D. Private SaaS solution in a single tenancy cloud.
Answer: D
NEW QUESTION 12
A security analyst discovered that the company’s WAF was not properly configured. The main web server was breached, and the following payload was found in one of the malicious requests: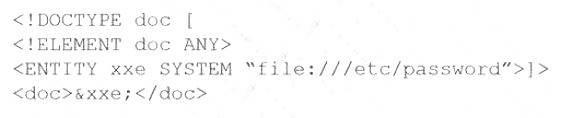
Which of the following would BEST mitigate this vulnerability?
- A. CAPTCHA
- B. Input validation
- C. Data encoding
- D. Network intrusion prevention
Answer: B
Explanation:
Reference: https://hdivsecurity.com/owasp-xml-external-entities-xxe
NEW QUESTION 13
A security analyst is researching containerization concepts for an organization. The analyst is concerned about potential resource exhaustion scenarios on the Docker host due to a single application that is overconsuming available resources.
Which of the following core Linux concepts BEST reflects the ability to limit resource allocation to containers?
- A. Union filesystem overlay
- B. Cgroups
- C. Linux namespaces
- D. Device mapper
Answer: B
Explanation:
Reference: https://www.ibm.com/support/pages/deep-dive-yarn-cgroups-hadoop-dev
NEW QUESTION 14
Which of the following is a benefit of using steganalysis techniques in forensic response?
- A. Breaking a symmetric cipher used in secure voice communications
- B. Determining the frequency of unique attacks against DRM-protected media
- C. Maintaining chain of custody for acquired evidence
- D. Identifying least significant bit encoding of data in a .wav file
Answer: D
Explanation:
Reference: https://www.garykessler.net/library/fsc_stego.html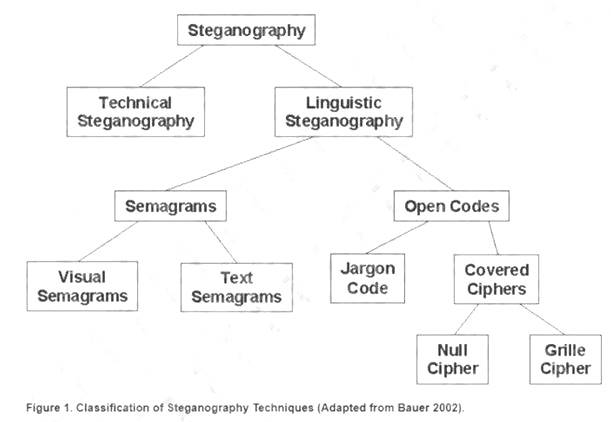
NEW QUESTION 15
A security analyst is performing a vulnerability assessment on behalf of a client. The analyst must define what constitutes a risk to the organization. Which of the following should be the analyst’s FIRST action?
- A. Create a full inventory of information and data assets.
- B. Ascertain the impact of an attack on the availability of crucial resources.
- C. Determine which security compliance standards should be followed.
- D. Perform a full system penetration test to determine the vulnerabilities.
Answer: C
NEW QUESTION 16
During a remodel, a company’s computer equipment was moved to a secure storage room with cameras positioned on both sides of the door. The door is locked using a card reader issued by the security team, and only the security team and department managers have access to the room. The company wants to be able to identify any unauthorized individuals who enter the storage room by following an authorized employee.
Which of the following processes would BEST satisfy this requirement?
- A. Monitor camera footage corresponding to a valid access request.
- B. Require both security and management to open the door.
- C. Require department managers to review denied-access requests.
- D. Issue new entry badges on a weekly basis.
Answer: A
Explanation:
Reference: https://www.getkisi.com/access-control
NEW QUESTION 17
In preparation for the holiday season, a company redesigned the system that manages retail sales and moved it to a cloud service provider. The new infrastructure did not meet the company’s availability requirements. During a postmortem analysis, the following issues were highlighted:
* 1. International users reported latency when images on the web page were initially loading.
* 2. During times of report processing, users reported issues with inventory when attempting to place orders.
* 3. Despite the fact that ten new API servers were added, the load across servers was heavy at peak times.
Which of the following infrastructure design changes would be BEST for the organization to implement to avoid these issues in the future?
- A. Serve static content via distributed CDNs, create a read replica of the central database and pull reports from there, and auto-scale API servers based on performance.
- B. Increase the bandwidth for the server that delivers images, use a CDN, change the database to a non-relational database, and split the ten API servers across two load balancers.
- C. Serve images from an object storage bucket with infrequent read times, replicate the database across different regions, and dynamically create API servers based on load.
- D. Serve static-content object storage across different regions, increase the instance size on the managed relational database, and distribute the ten API servers across multiple regions.
Answer: A
NEW QUESTION 18
A small company needs to reduce its operating costs. vendors have proposed solutions, which all focus on management of the company’s website and services. The Chief information Security Officer (CISO) insist all available resources in the proposal must be dedicated, but managing a private cloud is not an option .
Which of the following is the BEST solution for this company?
- A. Community cloud service model
- B. Multinency SaaS
- C. Single-tenancy SaaS
- D. On-premises cloud service model
Answer: A
NEW QUESTION 19
A security architect is implementing a web application that uses a database back end. Prior to the production, the architect is concerned about the possibility of XSS attacks and wants to identify security controls that could be put in place to prevent these attacks.
Which of the following sources could the architect consult to address this security concern?
- A. SDLC
- B. OVAL
- C. IEEE
- D. OWASP
Answer: B
Explanation:
Reference: https://dzone.com/articles/what-is-oval-a-community-driven-vulnerability-mana
NEW QUESTION 20
DRAG DROP
An organization is planning for disaster recovery and continuity of operations. INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding. Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. Select and Place: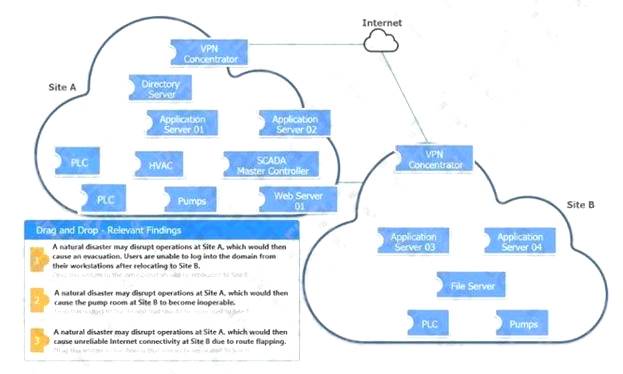
A.
- A.
Answer: A
NEW QUESTION 21
......
Thanks for reading the newest CAS-004 exam dumps! We recommend you to try the PREMIUM 2passeasy CAS-004 dumps in VCE and PDF here: https://www.2passeasy.com/dumps/CAS-004/ (128 Q&As Dumps)