It is more faster and easier to pass the Fortinet NSE4_FGT-6.4 exam by using Highest Quality Fortinet Fortinet NSE 4 - FortiOS 6.4 questuins and answers. Immediate access to the Most recent NSE4_FGT-6.4 Exam and find the same core area NSE4_FGT-6.4 questions with professionally verified answers, then PASS your exam with a high score now.
Online NSE4_FGT-6.4 free questions and answers of New Version:
NEW QUESTION 1
Examine this PAC file configuration.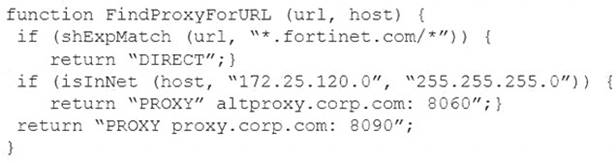
Which of the following statements are true? (Choose two.)
- A. Browsers can be configured to retrieve this PAC file from the FortiGate.
- B. Any web request to the 172.25.120.0/24 subnet is allowed to bypass the proxy.
- C. All requests not made to Fortinet.com or the 172.25.120.0/24 subnet, have to go through altproxy.corp.com: 8060.
- D. Any web request fortinet.com is allowed to bypass the proxy.
Answer: AD
NEW QUESTION 2
Refer to the exhibit.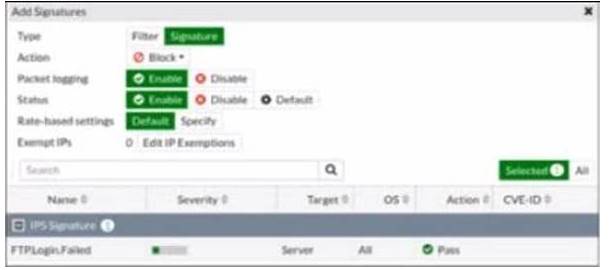
Review the Intrusion Prevention System (IPS) profile signature settings. Which statement is correct in adding the FTP.Login.Failed signature to the IPS sensor profile?
- A. The signature setting uses a custom rating threshold.
- B. The signature setting includes a group of other signatures.
- C. Traffic matching the signature will be allowed and logged.
- D. Traffic matching the signature will be silently dropped and logged.
Answer: B
NEW QUESTION 3
Refer to the exhibit.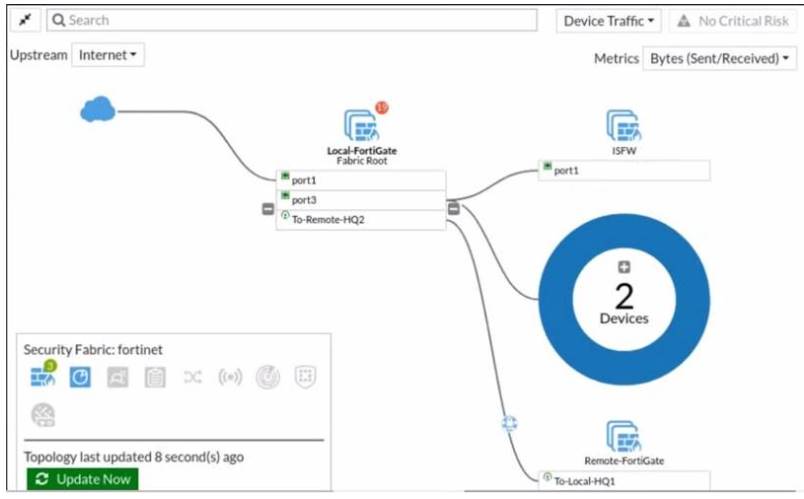
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)
- A. This security fabric topology is a logical topology view.
- B. There are 19 security recommendations for the security fabric.
- C. There are five devices that are part of the security fabric.
- D. Device detection is disabled on all FortiGate devices.
Answer: AD
NEW QUESTION 4
Which three authentication timeout types are availability for selection on FortiGate? (Choose three.)
- A. hard-timeout
- B. auth-on-demand
- C. soft-timeout
- D. new-session
- E. Idle-timeout
Answer: ADE
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD37221
NEW QUESTION 5
By default, FortiGate is configured to use HTTPS when performing live web filtering with FortiGuard servers. Which two CLI commands will cause FortiGate to use an unreliable protocol to communicate with FortiGuard servers for live web filtering? (Choose two.)
- A. set fortiguard anycast disable
- B. set protocol udp
- C. set webfilter-force-off disable
- D. set webfilter-cache disable
Answer: AC
NEW QUESTION 6
Which two actions can you perform only from the root FortiGate in a Security Fabric? (Choose two.)
- A. Shut down/reboot a downstream FortiGate device.
- B. Disable FortiAnalyzer logging for a downstream FortiGate device.
- C. Log in to a downstream FortiSwitch device.
- D. Ban or unban compromised hosts.
Answer: A
NEW QUESTION 7
A network administrator is configuring a new IPsec VPN tunnel on FortiGate. The remote peer IP address is dynamic, in addition, the remote peer does not support a dynamic DNS update service. What type of remote gateway should tie administrator configure on FortiGate for the new IPsec VPN tunnel to work?
- A. Static IP Address
- B. Dialup User
- C. Dynamic DNS
- D. Pre-shared Key
Answer: C
NEW QUESTION 8
If theServicesfield is configured in a Virtual IP (VIP), which statement is true when central NAT is used?
- A. TheServicesfield prevents SNAT and DNAT from being combined in the same policy.
- B. TheServicesfield is used when you need to bundle several VIPs into VIP groups.
- C. TheServicesfield removes the requirement to create multiple VIPs for different services.
- D. TheServicesfield prevents multiple sources of traffic from using multiple services to connect to a singlecomputer.
Answer: C
NEW QUESTION 9
Refer to the exhibit.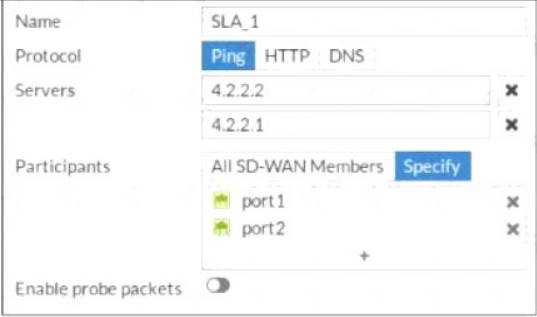
Which contains a PerformanceSLA configuration.
An administrator has configured a performance SLA on FortiGate. Which failed to generate any traffic. Why is FortiGate not generating any traffic for the performance SLA?
- A. Participants configured are not SD-WAN members.
- B. There may not be a static route to route the performance SLA traffic.
- C. The Ping protocol is not supported for the public servers that are configured.
- D. You need to turn on the Enable probe packets switch.
Answer: D
NEW QUESTION 10
Which of the following are purposes of NAT traversal in IPsec? (Choose two.)
- A. To delete intermediary NAT devices in the tunnel path.
- B. To dynamically change phase 1 negotiation mode aggressive mode.
- C. To encapsulation ESP packets in UDP packets using port 4500.
- D. To force a new DH exchange with each phase 2 rekey.
Answer: AC
NEW QUESTION 11
Which of statement is true about SSL VPN web mode?
- A. The tunnel is up while the client is connected.
- B. It supports a limited number of protocols.
- C. The external network application sends data through the VPN.
- D. It assigns a virtual IP address to the client.
Answer: C
NEW QUESTION 12
Refer to the exhibit.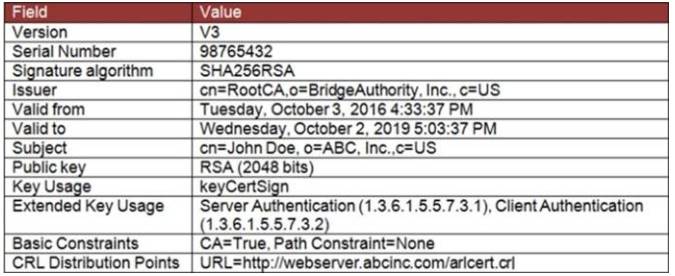
According to the certificate values shown in the exhibit, which type of entity was the certificate issued to?
- A. A user
- B. A root CA
- C. A bridge CA
- D. A subordinate
Answer: A
NEW QUESTION 13
Which two statements are true about the FGCP protocol? (Choose two.)
- A. Not used when FortiGate is in Transparent mode
- B. Elects the primary FortiGate device
- C. Runs only over the heartbeat links
- D. Is used to discover FortiGate devices in different HA groups
Answer: CD
NEW QUESTION 14
What types of traffic and attacks can be blocked by a web application firewall (WAF) profile? (Choose three.)
- A. Traffic to botnetservers
- B. Traffic to inappropriate web sites
- C. Server information disclosure attacks
- D. Credit card data leaks
- E. SQL injection attacks
Answer: ACE
NEW QUESTION 15
A FortiGate is operating in NAT mode and configured with two virtual LAN (VLAN) sub interfaces added to the physical interface.
Which statements about the VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in different subnets.
- A. The two VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in different subnets.
- B. The two VLAN sub interfaces must have different VLAN IDs.
- C. The two VLAN sub interfaces can have the same VLAN ID, only if they belong to different VDOMs.
- D. The two VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in the same subnet.
Answer: B
Explanation:
FortiGate_Infrastructure_6.0_Study_Guide_v2-Online.pdf –> page 147
“Multiple VLANs can coexist in the same physical interface, provide they have different VLAN ID”
NEW QUESTION 16
Which three statements about a flow-based antivirus profile are correct? (Choose three.)
- A. IPS engine handles the process as a standalone.
- B. FortiGate buffers the whole file but transmits to the client simultaneously.
- C. If the virus is detected, the last packet is delivered to the client.
- D. Optimized performance compared to proxy-based inspection.
- E. Flow-based inspection uses a hybrid of scanning modes available in proxy-based inspection.
Answer: CDE
NEW QUESTION 17
To complete the final step of a Security Fabric configuration, an administrator must authorize all the devices on which device?
- A. FortiManager
- B. Root FortiGate
- C. FortiAnalyzer
- D. Downstream FortiGate
Answer: B
NEW QUESTION 18
Examine the network diagram shown in the exhibit, then answer the following question: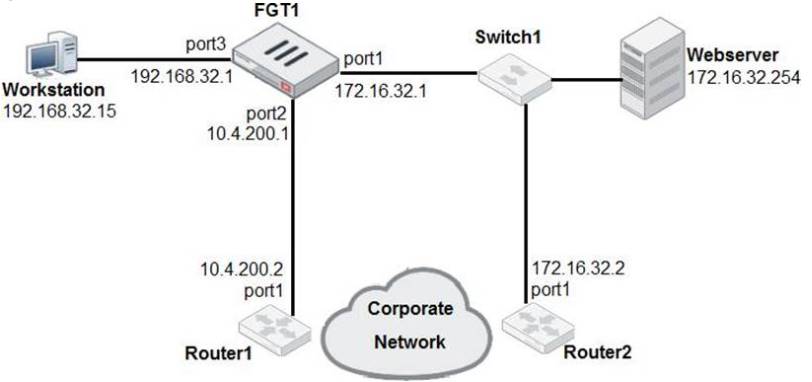
Which one of the following routes is the best candidate route for FGT1 to route traffic from the Workstation to the Web server?
- A. 172.16.0.0/16 [50/0] via 10.4.200.2, port2 [5/0]
- B. 0.0.0.0/0 [20/0] via 10.4.200.2, port2
- C. 10.4.200.0/30 is directly connected, port2
- D. 172.16.32.0/24 is directly connected, port1
Answer: D
NEW QUESTION 19
View the exhibit: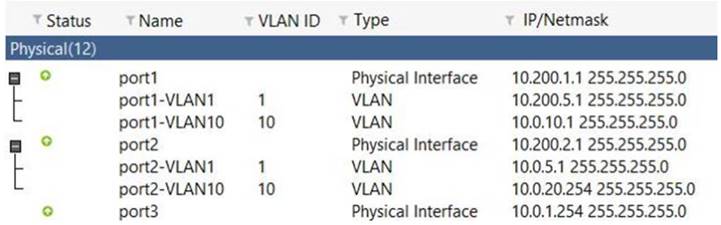
Which the FortiGate handle web proxy traffic rue? (Choose two.)
- A. Broadcast traffic received in port1-VLAN10 will not be forwarded to port2-VLAN10.
- B. port-VLAN1 is the native VLAN for the port1 physical interface.
- C. port1-VLAN10 and port2-VLAN10 can be assigned to different VDOMs.
- D. Traffic between port1-VLAN1 and port2-VLAN1 is allowed by default.
Answer: AC
NEW QUESTION 20
Refer to the exhibit.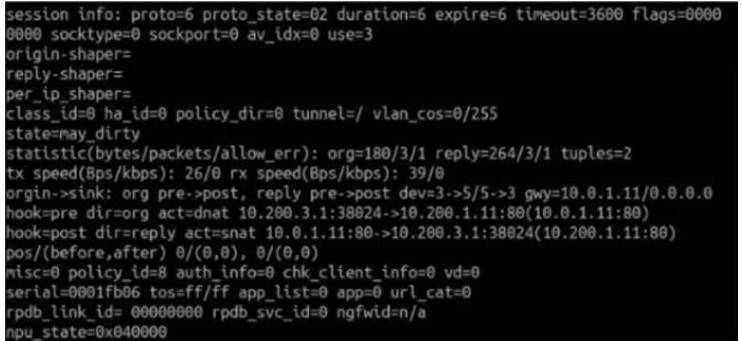
Which contains a session diagnostic output. Which statement is true about the session diagnostic output?
- A. The session is in SYN_SEXT state.
- B. The session is in FIN_ACK state.
- C. The session is in FTN_WAIT state.
- D. The session is in ESTABLISHED state.
Answer: D
NEW QUESTION 21
Which statement about the IP authentication header (AH) used by IPsec is true?
- A. AH does not provide any data integrity or encryption.
- B. AH does not support perfect forward secrecy.
- C. AH provides data integrity bur no encryption.
- D. AH provides strong data integrity but weak encryption.
Answer: C
NEW QUESTION 22
Refer to the exhibit.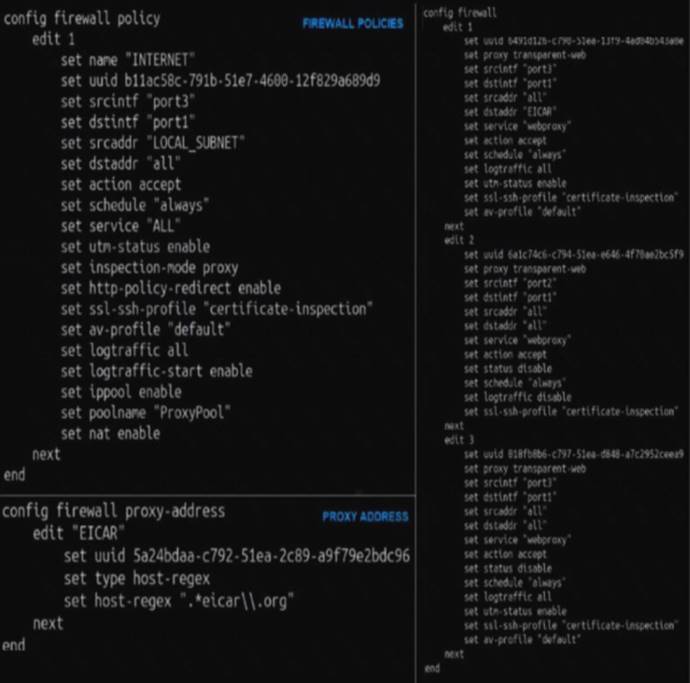
The exhibit shows a CLI output of firewall policies, proxy policies, and proxy addresses.
How does FortiGate process the traffic sent to http://www.fortinet.com?
- A. Traffic will be redirected to the transparent proxy and it will be allowed by proxy policy ID 3.
- B. Traffic will not be redirected to the transparent proxy and it will be allowed by firewall policy ID 1.
- C. Traffic will be redirected to the transparent proxy and It will be allowed by proxy policy ID 1.
- D. Traffic will be redirected to the transparent proxy and it will be denied by the proxy implicit deny policy.
Answer: D
NEW QUESTION 23
......
Recommend!! Get the Full NSE4_FGT-6.4 dumps in VCE and PDF From Certleader, Welcome to Download: https://www.certleader.com/NSE4_FGT-6.4-dumps.html (New 94 Q&As Version)