Certleader offers free demo for SY0-601 exam. "CompTIA Security+ Exam", also known as SY0-601 exam, is a CompTIA Certification. This set of posts, Passing the CompTIA SY0-601 exam, will help you answer those questions. The SY0-601 Questions & Answers covers all the knowledge points of the real exam. 100% real CompTIA SY0-601 exams and revised by experts!
Check SY0-601 free dumps before getting the full version:
NEW QUESTION 1
Which of the following BEST describes a security exploit for which a vendor patch is not readily available?
- A. Integer overflow
- B. Zero-day
- C. End of life
- D. Race condition
Answer: B
NEW QUESTION 2
A security engineer needs to Implement the following requirements:
• All Layer 2 switches should leverage Active Directory tor authentication.
• All Layer 2 switches should use local fallback authentication If Active Directory Is offline.
• All Layer 2 switches are not the same and are manufactured by several vendors.
Which of the following actions should the engineer take to meet these requirements? (Select TWO).
- A. Implement RADIUS.
- B. Configure AAA on the switch with local login as secondary.
- C. Configure port security on the switch with the secondary login method.
- D. Implement TACACS+
- E. Enable the local firewall on the Active Directory server.
- F. Implement a DHCP server.
Answer: AB
NEW QUESTION 3
An organization is developing a plan in the event of a complete loss of critical systems and data. Which of the following plans is the organization MOST likely developing?
- A. Incident response
- B. Communications
- C. Disaster recovery
- D. Data retention
Answer: C
NEW QUESTION 4
A network administrator has been alerted that web pages are experiencing long load times. After determining it is not a routing or DNS issue, the administrator logs in to the router, runs a command, and receives the following output:
Which of the following is the router experiencing?
- A. DDoS attack
- B. Memory leak
- C. Buffer overflow
- D. Resource exhaustion
Answer: D
NEW QUESTION 5
A retail executive recently accepted a job with a major competitor. The following week, a security analyst reviews the security logs and identifies successful logon attempts to access the departed executive's accounts. Which of the following security practices would have addressed the issue?
- A. A non-disclosure agreement
- B. Least privilege
- C. An acceptable use policy
- D. Ofboarding
Answer: D
NEW QUESTION 6
Which of the following incident response steps involves actions to protect critical systems while maintaining business operations?
- A. Investigation
- B. Containment
- C. Recovery
- D. Lessons learned
Answer: B
NEW QUESTION 7
An end user reports a computer has been acting slower than normal for a few weeks. During an investigation, an analyst determines the system is sending the user's email address and a ten-digit number to an IP address once a day. The only recent log entry regarding the user's computer is the following: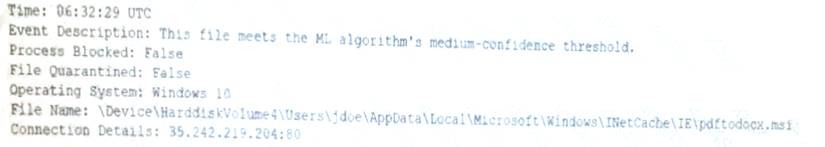
Which of the following is the MOST likely cause of the issue?
- A. The end user purchased and installed a PUP from a web browser
- B. A bot on the computer is brute forcing passwords against a website
- C. A hacker is attempting to exfiltrate sensitive data
- D. Ransomware is communicating with a command-and-control server.
Answer: A
NEW QUESTION 8
A security auditor is reviewing vulnerability scan data provided by an internal security team. Which of the following BEST indicates that valid credentials were used?
- A. The scan results show open ports, protocols, and services exposed on the target host
- B. The scan enumerated software versions of installed programs
- C. The scan produced a list of vulnerabilities on the target host
- D. The scan identified expired SSL certificates
Answer: B
NEW QUESTION 9
Which of the following BEST explains the difference between a data owner and a data custodian?
- A. The data owner is responsible for adhering to the rules for using the data, while the data custodian is responsible for determining the corporate governance regarding the data
- B. The data owner is responsible for determining how the data may be used, while the data custodian is responsible for implementing the protection to the data
- C. The data owner is responsible for controlling the data, while the data custodian is responsible for maintaining the chain of custody when handling the data
- D. The data owner grants the technical permissions for data access, while the data custodian maintains the database access controls to the data
Answer: B
NEW QUESTION 10
A network administrator has been asked to design a solution to improve a company's security posture The administrator is given the following, requirements?
• The solution must be inline in the network
• The solution must be able to block known malicious traffic
• The solution must be able to stop network-based attacks
Which of the following should the network administrator implement to BEST meet these requirements?
- A. HIDS
- B. NIDS
- C. HIPS
- D. NIPS
Answer: D
NEW QUESTION 11
A network administrator would like to configure a site-to-site VPN utilizing iPSec. The administrator wants the tunnel to be established with data integrity encryption, authentication and anti- replay functions Which of the following should the administrator use when configuring the VPN?
- A. AH
- B. EDR
- C. ESP
- D. DNSSEC
Answer: C
NEW QUESTION 12
A database administrator needs to ensure all passwords are stored in a secure manner, so the administrate adds randomly generated data to each password before string. Which of the following techniques BEST explains this action?
- A. Predictability
- B. Key stretching
- C. Salting
- D. Hashing
Answer: C
NEW QUESTION 13
An organization has decided to host its web application and database in the cloud Which of the following BEST describes the security concerns for this decision?
- A. Access to the organization's servers could be exposed to other cloud-provider clients
- B. The cloud vendor is a new attack vector within the supply chain
- C. Outsourcing the code development adds risk to the cloud provider
- D. Vendor support will cease when the hosting platforms reach EOL.
Answer: B
NEW QUESTION 14
Which of the following are requirements that must be configured for PCI DSS compliance? (Select TWO).
- A. Testing security systems and processes regularly
- B. Installing and maintaining a web proxy to protect cardholder data
- C. Assigning a unique ID to each person with computer access
- D. Encrypting transmission of cardholder data across private networks
- E. Benchmarking security awareness training for contractors
- F. Using vendor-supplied default passwords for system passwords
Answer: BD
NEW QUESTION 15
A security modern may have occurred on the desktop PC of an organization's Chief Executive Officer (CEO) A duplicate copy of the CEO's hard drive must be stored securely to ensure appropriate forensic processes and the chain of custody are followed. Which of the following should be performed to accomplish this task?
- A. Install a new hard drive in the CEO's PC, and then remove the old hard drive and place it in a tamper-evident bag
- B. Connect a write blocker to the hard drive Then leveraging a forensic workstation, utilize the dd command m a live Linux environment to create a duplicate copy
- C. Remove the CEO's hard drive from the PC, connect to the forensic workstation, and copy all the contents onto a remote fileshare while the CEO watches
- D. Refrain from completing a forensic analysts of the CEO's hard drive until after the incident is confirmed, duplicating the hard drive at this stage could destroy evidence
Answer: D
NEW QUESTION 16
Under GDPR, which of the following is MOST responsible for the protection of privacy and website user rights?
- A. The data protection officer
- B. The data processor
- C. The data owner
- D. The data controller
Answer: C
NEW QUESTION 17
A researcher has been analyzing large data sets for the last ten months. The researcher works with colleagues from other institutions and typically connects via SSH to retrieve additional data. Historically, this setup has worked without issue, but the researcher recently started getting the following message: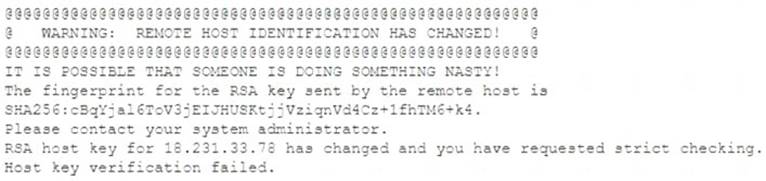
Which of the following network attacks is the researcher MOST likely experiencing?
- A. MAC cloning
- B. Evil twin
- C. Man-in-the-middle
- D. ARP poisoning
Answer: C
NEW QUESTION 18
The Chief Financial Officer (CFO) of an insurance company received an email from Ann, the company’s Chief Executive Officer (CEO), requesting a transfer of $10,000 to an account. The email states Ann is on vacation and has lost her purse, containing cash and credit cards. Which of the following social-engineering techniques is the attacker using?
- A. Phishing
- B. Whaling
- C. Typo squatting
- D. Pharming
Answer: B
NEW QUESTION 19
Local guidelines require that all information systems meet a minimum-security baseline to be compliant. Which of the following can security administrators use to assess their system configurations against the baseline?
- A. SOAR playbook
- B. Security control matrix
- C. Risk management framework
- D. Benchmarks
Answer: D
NEW QUESTION 20
Which of the following will provide the BEST physical security countermeasures to stop intruders? (Select TWO.)
- A. Alarms
- B. Signage
- C. Lighting
- D. Mantraps
- E. Fencing
- F. Sensors
Answer: DE
NEW QUESTION 21
A website developer is working on a new e-commerce website and has asked an information security expert for the most appropriate way to store credit card numbers to create an easy reordering process. Which of the following methods would BEST accomplish this goal?
- A. Salting the magnetic strip information
- B. Encrypting the credit card information in transit.
- C. Hashing the credit card numbers upon entry.
- D. Tokenizing the credit cards in the database
Answer: C
NEW QUESTION 22
......
Thanks for reading the newest SY0-601 exam dumps! We recommend you to try the PREMIUM Thedumpscentre.com SY0-601 dumps in VCE and PDF here: https://www.thedumpscentre.com/SY0-601-dumps/ (218 Q&As Dumps)