Master the SY0-701 CompTIA Security+ Exam content and be ready for exam day success quickly with this Passleader SY0-701 free download. We guarantee it!We make it a reality and give you real SY0-701 questions in our CompTIA SY0-701 braindumps.Latest 100% VALID CompTIA SY0-701 Exam Questions Dumps at below page. You can use our CompTIA SY0-701 braindumps and pass your exam.
CompTIA SY0-701 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
During a security assessment, a security finds a file with overly permissive permissions. Which of the following tools will allow the analyst to reduce the permission for the existing users and groups and remove the set-user-ID from the file?
- A. 1s
- B. chflags
- C. chmod
- D. lsof
- E. setuid
Answer: C
Explanation:
The chmod command is used to change the permissions of a file or directory. The analyst can use chmod to reduce the permissions for existing users and groups and remove the set-user-ID bit from the file. References: CompTIA Security+ Study Guide Exam SY0-601, Chapter 6
CompTIA Security+ Study Guide Exam SY0-601, Chapter 6
NEW QUESTION 2
A new security engineer has started hardening systems. One of the hardening techniques the engineer is using involves disabling remote logins to the NAS. Users are now reporting the inability to use SCP to transfer files to the NAS, even through the data is still viewable from the user’s PCs. Which of the following is the most likely cause of this issue?
- A. TFTP was disabled on the local hosts
- B. SSH was turned off instead of modifying the configuration file
- C. Remote login was disabled in the networkd.config instead of using the sshd.conf
- D. Network services are no longer running on the NAS
Answer: B
Explanation:
SSH stands for Secure Shell Protocol, which is a cryptographic network protocol that allows secure remote login and command execution on a network device12. SSH can encrypt both the authentication information and the data being exchanged between the client and the server2. SSH can be used to access and manage a NAS device remotely3.
NEW QUESTION 3
A web architect would like to move a company's website presence to the cloud. One of the management team's key concerns is resiliency in case a cloud provider's data center or network connection goes down. Which of the following should the web architect consider to address this concern?
- A. Containers
- B. Virtual private cloud
- C. Segmentation
- D. Availability zones
Answer: D
Explanation:
Availability zones are the most appropriate cloud feature to address the concern of resiliency in case a cloud provider’s data center or network connection goes down. Availability zones are physically separate locations within an Azure region that have independent power, cooling, and networking. Each availability zone is made up of one or more data centers and houses infrastructure to support highly available, mission-critical applications. Availability zones are connected with high-speed, private fiber-optic networks. Azure services that support availability zones fall into two categories: Zonal services – you pin the resource to a specific zone (for example, virtual machines, managed disks, IP addresses), or Zone-redundant services – platform replicates automatically across zones (for example, zone-redundant storage, SQL Database). To achieve comprehensive business continuity on Azure, build your application architecture using the combination of availability zones with Azure region pairs. You can synchronously replicate your applications and data using availability zones within an Azure region for high-availability and asynchronously replicate across Azure regions for disaster recovery protection.
NEW QUESTION 4
Developers are writing code and merging it into shared repositories several times a day, where it is tested automatically. Which of the following concepts does this BEST represent?
- A. Functional testing
- B. Stored procedures
- C. Elasticity
- D. Continuous integration
Answer: D
Explanation:
Continuous integration is a software development practice where developers merge their code into a shared repository several times a day, and the code is tested automatically. This ensures that code changes are tested and integrated continuously, reducing the risk of errors and conflicts.
NEW QUESTION 5
A retail company that is launching @ new website to showcase the company’s product line and other information for online shoppers registered the following URLs:
* www companysite com
* shop companysite com
* about-us companysite com contact-us. companysite com secure-logon company site com
Which of the following should the company use to secure its website if the company is concerned with convenience and cost?
- A. A self-signed certificate
- B. A root certificate
- C. A code-signing certificate
- D. A wildcard certificate
- E. An extended validation certificate
Answer: D
Explanation:
The company can use a wildcard certificate to secure its website if it is concerned with convenience and cost. A wildcard certificate can secure multiple subdomains, which makes it cost-effective and convenient for securing the various registered domains.
The retail company should use a wildcard certificate if it is concerned with convenience and c1o2s.tA wildcard SSL certificate is a single SSL/TLS certificate that can provide significant time and cost savings, particularly for small businesses. The certificate includes a wildcard character (*) in the domain name field, and can secure multiple subdomains of the primary domain1
NEW QUESTION 6
The Chief Executive Officer announced a new partnership with a strategic vendor and asked the Chief Information Security Officer to federate user digital identities using SAML-based protocols. Which of the following will this enable?
- A. SSO
- B. MFA
- C. PKI
- D. OLP
Answer: A
Explanation:
Federating user digital identities using SAML-based protocols enables Single Sign-On (SSO), which allows users to log in once and access multiple applications without having to enter their credentials for each one. References: CompTIA Security+ Certification Exam Objectives 1.3: Explain authentication and access controls.
CompTIA Security+ Certification Exam Objectives 1.3: Explain authentication and access controls.  CompTIA Security+ Study Guide, Sixth Edition, pages 41-42
CompTIA Security+ Study Guide, Sixth Edition, pages 41-42
NEW QUESTION 7
A network analyst is setting up a wireless access point for a home office in a remote, rural location. The requirement is that users need to connect to the access point securely but do not want to have to remember passwords Which of the following should the network analyst enable to meet the requirement?
- A. MAC address filtering
- B. 802.1X
- C. Captive portal
- D. WPS
Answer: D
Explanation:
The network analyst should enable Wi-Fi Protected Setup (WPS) to allow users to connect to the wireless access point securely without having to remember passwords. WPS allows users to connect to a wireless network by pressing a button or entering a PIN instead of entering a password.
Reference: CompTIA Security+ Study Guide, Exam SY0-601, Chapter 4: Identity and Access Management
NEW QUESTION 8
A network analyst is investigating compromised corporate information. The analyst leads to a theory that network traffic was intercepted before being transmitted to the internet. The following output was captured on an internal host:
Based on the IoCS, which of the following was the MOST likely attack used to compromise the network communication?
- A. Denial of service
- B. ARP poisoning
- C. Command injection
- D. MAC flooding
Answer: B
Explanation:
ARP poisoning (also known as ARP spoofing) is a type of attack where an attacker sends falsified ARP messages over a local area network to link the attacker's MAC address with the IP address of another host on the network. References: CompTIA Security+ Certification Exam Objectives - 2.5 Given a scenario, analyze potential indicators to determine the type of attack. Study Guide: Chapter 6, page 271.
NEW QUESTION 9
After gaining access to a dual-homed (i.e.. wired and wireless) multifunction device by exploiting a vulnerability in the device's firmware, a penetration tester then gains shell access on another networked asset This technique is an example of:
- A. privilege escalation
- B. footprinting
- C. persistence
- D. pivoting.
Answer: D
Explanation:
The technique of gaining access to a dual-homed multifunction device and then gaining shell access on another networked asset is an example of pivoting. References: CompTIA Security+ Study Guide by Emmett Dulaney, Chapter 8: Application, Data, and Host Security, Enumeration and Penetration Testing
NEW QUESTION 10
A security engineer needs to recommend a solution to defend against malicious actors misusing protocols and being allowed through network defenses. Which of the following will the engineer most likely recommended?
- A. A content filter
- B. AWAF
- C. A next-generation firewall
- D. An IDS
Answer: C
Explanation:
A next-generation firewall (NGFW) is a solution that can defend against malicious actors misusing protocols and being allowed through network defenses. A NGFW is a type of firewall that can perform deep packet inspection, application-level filtering, intrusion prevention, malware detection, and identity-based access control. A NGFW can also use threat intelligence and behavioral analysis to identify and block malicious traffic based on protocols, signatures, or anomalies. References:
https://www.comptia.org/blog/what-is-a-next-generation-firewall
https://www.certblaster.com/wp-content/uploads/2020/11/CompTIA-Security-SY0-601-Exam-Objectives-1.0.pd
NEW QUESTION 11
During a forensic investigation, a security analyst discovered that the following command was run on a compromised host:
Which of the following attacks occurred?
- A. Buffer overflow
- B. Pass the hash
- C. SQL injection
- D. Replay attack
Answer: B
Explanation:
Pass the hash is an attack technique that allows an attacker to authenticate to a remote server or service by using the hashed version of a user’s password, rather than requiring the plaintext password
NEW QUESTION 12
Physical access to the organization's servers in the data center requires entry and exit through multiple access points: a lobby, an access control vestibule, three doors leading to the server floor itself and eventually to a caged area solely for the organization's hardware. Which of the following controls is described in this scenario?
- A. Compensating
- B. Deterrent
- C. Preventive
- D. Detective
Answer: C
Explanation:
The scenario describes preventive controls, which are designed to stop malicious actors from gaining access to the organization's servers. This includes using multiple access points, such as a lobby, an access control vestibule, and multiple doors leading to the server floor, as well as caging the organization's hardware. According to the CompTIA Security+ SY0-601 document, preventive controls are "designed to stop malicious actors from performing a malicious activity or gaining access to an asset." These controls can include technical solutions, such as authentication and access control systems, physical security solutions, such as locks and barriers, and administrative solutions such as policy enforcement.
NEW QUESTION 13
A company's public-facing website, https://www.organization.com, has an IP address of 166.18.75.6. However, over the past hour the SOC has received reports of the site's homepage displaying incorrect information. A quick nslookup search shows hitps://;www.organization.com is pointing to 151.191.122.115. Which of the following is occurring?
- A. DoS attack
- B. ARP poisoning
- C. DNS spoofing
- D. NXDOMAIN attack
Answer: C
Explanation:
The issue is DNS spoofing, where the DNS resolution has been compromised and is pointing to a malicious IP address. References: CompTIA Security+ Study Guide: Exam SY0-601, Chapter 7
NEW QUESTION 14
An organization wants to quickly assess how effectively the IT team hardened new laptops Which of the following would be the best solution to perform this assessment?
- A. Install a SIEM tool and properly configure it to read the OS configuration files.
- B. Load current baselines into the existing vulnerability scanner.
- C. Maintain a risk register with each security control marked as compliant or non-compliant.
- D. Manually review the secure configuration guide checklists.
Answer: B
Explanation:
A vulnerability scanner is a tool that can scan devices and systems for known vulnerabilities, misconfigurations, and compliance issues. By loading the current baselines into the scanner, the organization can compare the actual state of the new laptops with the desired state and identify any deviations or weaknesses. This is a quick and automated way to assess the hardening of the new laptops.
NEW QUESTION 15
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.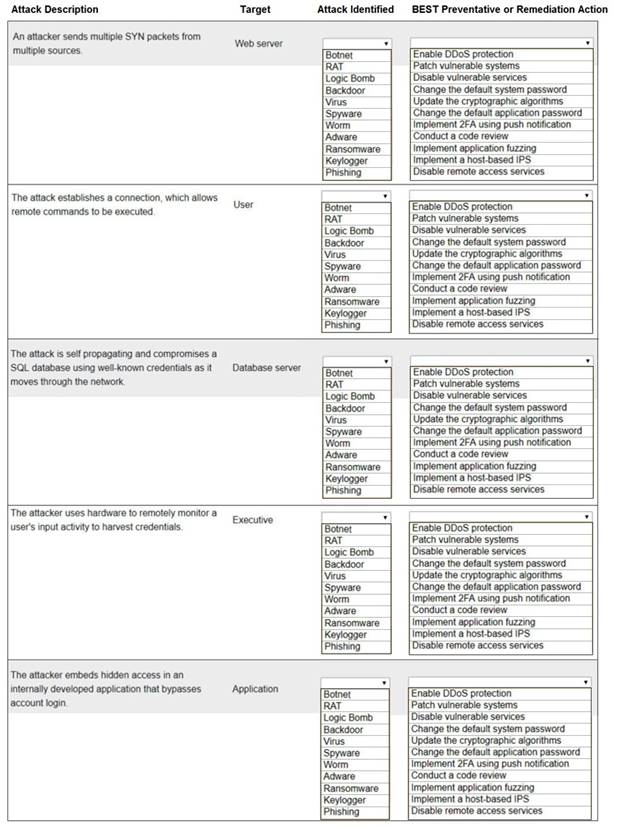
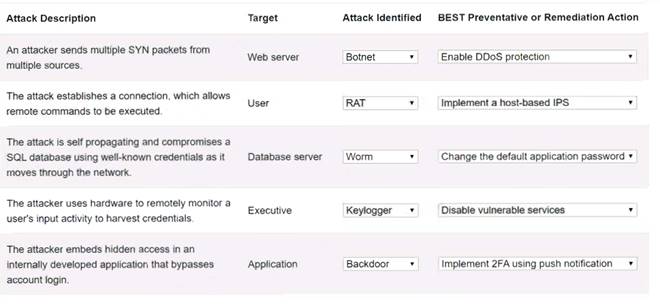
Solution:
Web serverBotnet Enable DDoS protectionUser RAT Implement a host-based IPSDatabase server Worm Change the default application passwordExecutive KeyloggerDisable vulnerable servicesApplication Backdoor Implement 2FA using push notification
A screenshot of a computer program Description automatically generated with low confidence
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
A security team is conducting a security review of a hosted data provider. The management team has asked the hosted data provider to share proof that customer data is being appropriately protected.
Which of the following would provide the best proof that customer data is being protected?
- A. SOC2
- B. CSA
- C. CSF
- D. 1SO 31000
Answer: A
Explanation:
SOC2 is a type of audit report that provides assurance on the security, availability, processing integrity, confidentiality, and privacy of a service organization’s systems. It is based on the Trust Services Criteria developed by the American Institute of Certified Public Accountants (AICPA). A SOC2 report can provide proof that customer data is being appropriately protected by the hosted data provider1
https://www.csagroup.org/store/product/50072454/ 3: https://www.csagroup.org/store/product/50072454os/ 1: https://cloudsecurityalliance.org/blog/2021/08/20/star-testimonial-csa-star-soc2-from-readiness-to-attestation/
NEW QUESTION 17
The most recent vulnerability scan flagged the domain controller with a critical vulnerability. The systems administrator researched the vulnerability and discovered the domain controller does not run the associated application with the vulnerability. Which of the following steps should the administrator take next?
- A. Ensure the scan engine is configured correctly.
- B. Apply a patch to the domain controller.
- C. Research the CVE.
- D. Document this as a false positive.
Answer: D
Explanation:
A false positive is a result that indicates a problem when there is no actual problem. In this case, the vulnerability scan flagged the domain controller with a critical vulnerability, but the domain controller does not run the application that is vulnerable. Therefore, the scan result is inaccurate and should be documented as a false positive.
* A. Ensure the scan engine is configured correctly. This is not the next step, because the scan engine may be configured correctly and still produce false positives due to various factors, such as outdated signatures, network latency, or misconfigured devices.
* B. Apply a patch to the domain controller. This is not the next step, because applying a patch to a system that does not have the vulnerability may cause unnecessary problems or conflicts.
* C. Research the CVE. This is not the next step, because the systems administrator already researched the vulnerability and discovered that it does not affect the domain controller.
* D. Document this as a false positive. This is the correct answer, because documenting false positives helps to improve the accuracy and efficiency of future scans and audits.
Reference: CompTIA Security+ Study Guide (PDF) - Netwrix, page 14.
NEW QUESTION 18
......
100% Valid and Newest Version SY0-701 Questions & Answers shared by 2passeasy, Get Full Dumps HERE: https://www.2passeasy.com/dumps/SY0-701/ (New 0 Q&As)