Cause all that matters here is passing exam with CS0-001 Study Guides. Cause all that you need is a high score of CS0-001 Dumps. The only one thing you need to do is downloading CS0-001 Dumps Questions free now. We will not let you down with our money-back guarantee.
CompTIA CS0-001 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
A new policy requires the security team to perform web application and OS vulnerability scans. All of the company’s web applications use federated authentication and are accessible via a central portal. Which of the following should be implemented to ensure a more thorough scan of the company’s web application, while at the same time reducing false positives?
- A. The vulnerability scanner should be configured to perform authenticated scans.
- B. The vulnerability scanner should be installed on the web server.
- C. The vulnerability scanner should implement OS and network service detection.
- D. The vulnerability scanner should scan for known and unknown vulnerabilities.
Answer: A
NEW QUESTION 2
The development team cur.en.ly consists of lh.ee developers who each specialize in a specific programming language:
Developer 1 – C++/C#
Developer 2 – Python Developer 3 – Assembly
Which of the following SDLC best practices would be challenging lo implement with the current available staff?
- A. Fuzzing
- B. Peer review
- C. Regression testing
- D. Stress testing
Answer: B
NEW QUESTION 3
Which of the following could be directly impacted by an unpatched vulnerability m vSphre ESXi?
- A. The organization's physical routers
- B. The organization's mobile devices
- C. The organization's virtual infrastructure
- D. The organization's VPN
Answer: C
NEW QUESTION 4
When reviewing network traffic, a security analyst detects suspicious activity:
Based on the log above, which of the following vulnerability attacks is occurring?
- A. ShellShock
- B. DROWN
- C. Zeus
- D. Heartbleed
- E. POODLE
Answer: E
NEW QUESTION 5
The software development team pushed a new web application into production for the accounting department. Shortly after the application was published, the head of the accounting department informed IT operations that the application was not performing as intended. Which of the following SDLC best practices was missed?
- A. Peer code reviews
- B. Regression testing
- C. User acceptance testing
- D. Fuzzing
- E. Static code analysis
Answer: C
NEW QUESTION 6
A system administrator recently deployed and verified the installation of a critical patch issued by the company’s primary OS vendor. This patch was supposed to remedy a vulnerability that would allow an adversary to remotely execute code from over the network. However, the administrator just ran a vulnerability assessment of networked systems, and each of them still reported having the same vulnerability. Which of the following is the MOST likely explanation for this?
- A. The administrator entered the wrong IP range for the assessment.
- B. The administrator did not wait long enough after applying the patch to run the assessment.
- C. The patch did not remediate the vulnerability.
- D. The vulnerability assessment returned false positives.
Answer: C
NEW QUESTION 7
A cybersecurity professional typed in a URL and discovered the admin panel for the e-commerce application is accessible over the open web with the default password. Which of the following is the MOST secure solution to remediate this vulnerability?
- A. Rename the URL to a more obscure name, whitelist all corporate IP blocks, and require two-factor authentication.
- B. Change the default password, whitelist specific source IP addresses, and require two-factor authentication.
- C. Whitelist all corporate IP blocks, require an alphanumeric passphrase for the default password, and require two-factor authentication.
- D. Change the username and default password, whitelist specific source IP addresses, and require two-factor authentication.
Answer: D
NEW QUESTION 8
A cybersecurity analyst is reviewing log data and sees the output below: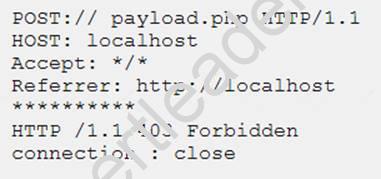
Which of the following technologies MOST likely generated this log?
- A. Stateful inspection firewall
- B. Network-based intrusion detection system
- C. Web application firewall
- D. Host-based intrusion detection system
Answer: C
NEW QUESTION 9
An alert has been distributed throughout the information security community regarding a critical Apache vulnerability. Which of the following courses of action would ONLY identify the known vulnerability?
- A. Perform an unauthenticated vulnerability scan on all servers in the environment.
- B. Perform a scan for the specific vulnerability on all web servers.
- C. Perform a web vulnerability scan on all servers in the environment.
- D. Perform an authenticated scan on all web servers in the environment.
Answer: B
NEW QUESTION 10
Scan results identify critical Apache vulnerabilities on a company’s web servers. A security analyst believes many of these results are false positives because the web environment mostly consists of Windows servers.
Which of the following is the BEST method of verifying the scan results?
- A. Run a service discovery scan on the identified servers.
- B. Refer to the identified servers in the asset inventory.
- C. Perform a top-ports scan against the identified servers.
- D. Review logs of each host in the SIEM.
Answer: A
NEW QUESTION 11
Which of the following remediation strategies are MOST effective in reducing the risk of a network-based compromise of embedded ICS? (Select two.)
- A. Patching
- B. NIDS
- C. Segmentation
- D. Disabling unused services
- E. Firewalling
Answer: CD
NEW QUESTION 12
Using a heuristic system to detect an anomaly in a computer’s baseline, a system administrator was able to detect an attack even though the company signature based IDS and antivirus did not detect it. Further analysis revealed that the attacker had downloaded an executable file onto the company PC from the USB port, and executed it to trigger a privilege escalation flaw. Which of the following attacks has MOST likely occurred?
- A. Cookie stealing
- B. Zero-day
- C. Directory traversal
- D. XML injection
Answer: B
NEW QUESTION 13
The director of software development is concerned with recent web application security incidents, including the successful breach of a back-end database server. The director would like to work with the security team to implement a standardized way to design, build, and test web applications and the services that support them. Which of the following meets the criteria?
- A. OWASP
- B. SANS
- C. PHP
- D. Ajax
Answer: A
Explanation: Reference https://www.synopsys.com/software-integrity/resources/knowledge-database/owasp-top-10.html
NEW QUESTION 14
A cybersecurity analyst has identified a new mission-essential function that utilizes a public cloud-based system. The analyst needs to classify the information processed by the system with respect to CIA. Which of the following should provide the CIA classification for the information?
- A. The cloud provider
- B. The data owner
- C. The cybersecurity analyst
- D. The system administrator
Answer: B
NEW QUESTION 15
A security analyst is creating ACLs on a perimeter firewall that will deny inbound packets that are from internal addresses, reserved external addresses, and multicast addresses. Which of the following is the analyst attempting to prevent/
- A. Broadcast storms
- B. Spoofing attacks
- C. UDoS attacks
- D. Man in-the-middle attacks
Answer: B
NEW QUESTION 16
When network administrators observe an increased amount of web traffic without an increased number of financial transactions, the company is MOST likely experiencing which of the following attacks?
- A. Bluejacking
- B. ARP cache poisoning
- C. Phishing
- D. DoS
Answer: D
NEW QUESTION 17
A vulnerability analyst needs to identity all systems with unauthorized web servers on the 10 1 1 0/24 network. The analyst uses the following default Nmap scan:
nmap –sV –p 1-65535 10.1.1.0/24
Which of the following would be the result of running the above command?
- A. This scan checks all TCP ports
- B. This scan probes all ports and returns open ones
- C. This scan checks all TCP ports and returns versions
- D. This scan identities unauthorized serves
Answer: C
NEW QUESTION 18
The Chief Security Office (CSO) has requested a vulnerability report of systems on the domain, identifying those running outdated OSs. The automated scan reports are not displaying OS version derails so the CSO cannot determine risk exposure levels from vulnerable systems. Which of the following should the cybersecurity analyst do to enumerate OS information as part of the vulnerability scanning process in the MOST efficient manner?
- A. Execute the ver command
- B. Execute the nmap -p command
- C. Use Wireshart to export a list
- D. Use credentialed configuration
Answer: A
P.S. Dumpscollection now are offering 100% pass ensure CS0-001 dumps! All CS0-001 exam questions have been updated with correct answers: http://www.dumpscollection.net/dumps/CS0-001/ (242 New Questions)