Cause all that matters here is passing exam with CS0-001 Free Practice Questions. Cause all that you need is a high score of CS0-001 Free Practice Questions. The only one thing you need to do is downloading CS0-001 Exam Questions free now. We will not let you down with our money-back guarantee.
Free demo questions for CompTIA CS0-001 Exam Dumps Below:
NEW QUESTION 1
A technician receives an alert indicating an endpoint is beaconing to a suspect dynamic DNS domain. Which of the following countermeasures should be used to BEST protect the network In response to this alert? (Select TWO)
- A. Set up a sinkhole for that dynamic DNS domain to prevent communication.
- B. Isolate the infected endpoint to prevent the potential spread of malicious activity.
- C. Implement an internal honeypot to catch the malicious traffic and trace it.
- D. Perform a risk assessment and implement compensating controls.
- E. Ensure the IDS is active on the network segment where the endpoint resides.
Answer: AB
NEW QUESTION 2
A company installed a wireless network more than a year ago, standardizing on the same model APs in a single subnet. Recently, several users have reported timeouts and connection issues with Internet browsing. The security administrator has gathered some information about the network to try to recreate the issues with the assistance of a user. The administrator is able to ping every device on the network and confirms that the network is very slow.
Output: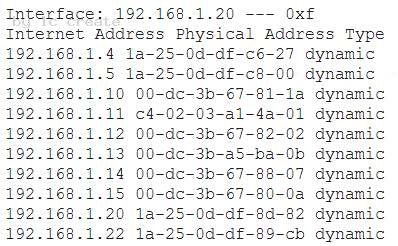
Given the above results, which of the following should the administrator investigate FIRST?
- A. The AP-Workshop device
- B. The AP-Reception device
- C. The device at 192.168.1.4
- D. The AP-IT device
- E. The user’s PC
Answer: A
NEW QUESTION 3
Which of the following best practices is used to identify areas in the network that may be vulnerable to penetration testing from known external sources?
- A. Blue team training exercises
- B. Technical control reviews
- C. White team training exercises
- D. Operational control reviews
Answer: A
NEW QUESTION 4
A security analyst has determined the security team should take action based on the following log: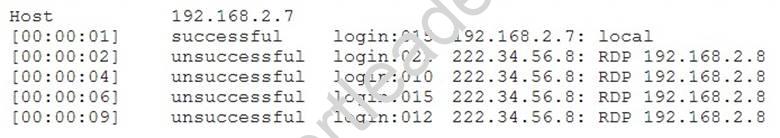
Which of the following should be used to improve the security posture of the system?
- A. Enable login account auditing.
- B. Limit the number of unsuccessful login attempts
- C. Upgrade the firewalls
- D. Increase password complexity requirements
Answer: B
NEW QUESTION 5
A zero-day crypto-worm is quickly spreading through the internal network on port 25 and exploiting a software vulnerability found within the email servers.
Which of the following countermeasures needs to be implemented as soon as possible to mitigate the worm from continuing to spread?
- A. Implement a traffic sinkhole.
- B. Block all known port/services.
- C. Isolate impacted servers.
- D. Patch affected systems.
Answer: C
NEW QUESTION 6
A company provides wireless connectivity to the internal network from all physical locations for companyowned devices. Users were able to connect the day before, but now all users have reported that when they connect to an access point in the conference room, they cannot access company resources. Which of the following BEST describes the cause of the problem?
- A. The access point is blocking access by MAC addres
- B. Disable MAC address filtering.
- C. The network is not availabl
- D. Escalate the issue to network support.
- E. Expired DNS entries on users’ device
- F. Request the affected users perform a DNS flush.
- G. The access point is a rogue devic
- H. Follow incident response procedures.
Answer: D
NEW QUESTION 7
During winch of the lo.low.ng NIST risk management framework steps would an information system security engineer identify inherited security controls and tailor those controls to the system?
- A. Categorize
- B. Select
- C. Implement
- D. Assess
Answer: B
NEW QUESTION 8
Which of the fallowing has the GREAT EST impact to the data retention policies of an organization?
- A. The CIA classification matrix assigned to each piece of data
- B. The level of sensitivity of the data established by the data owner
- C. The regulatory requirements concerning the data set
- D. The technical constraints of the technology used to store the data
Answer: D
NEW QUESTION 9
Alerts have been received from the SIEM, indicating infections on multiple computers. Based on threat characteristic, these files were quarantined by the host-based antivirus program. At the same time, additional alerts in the SIEM show multiple blocked URLs from the address of the infected computers; the URLs were clashed as uncategorized. The domain location of the IP address of the URLs that were blocked is checked, and it is registered to an ISP in Russia. Which of the following steps should be taken NEXT?
- A. Remove those computers from the network and replace the hard drives Send the Infected hard drives out lot investigation.
- B. Run a full antivirus scan on all computers and use Splunk to search for any suspicious activity that happened just before the alerts were received in the SIEM.
- C. Run a vulnerability scan and patch discovered vulnerabilities on the next patching cycle Have the users restart their computer Create a use case in the SIEM to monitor farted logins oninfected computers.
- D. Install a computer with the same settings as the infected computers in the DM^ to use as a honeypot Permit the URLs classified as uncategorized to and from that host.
Answer: B
NEW QUESTION 10
A security analyst suspects that a workstation may be beaconing to a command and control server. You must inspect the logs from the company’s web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.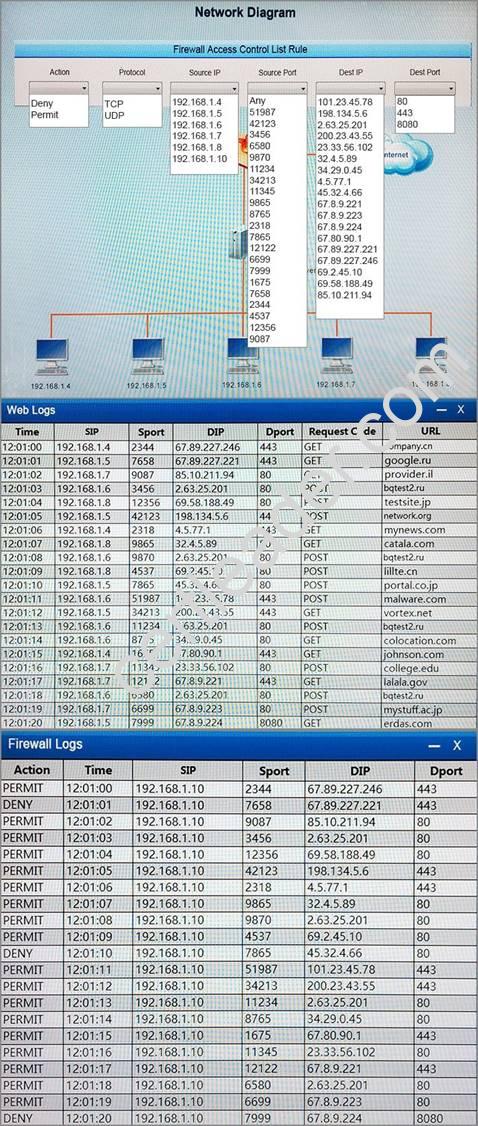
Answer:
Explanation: DENYTCP 192.168.1.5 7999 67.8.9.2248080
NEW QUESTION 11
A recent audit included a vulnerability scan that found critical patches released GO days prior were not applied to servers in the environment The infrastructure team was able to isolate the issue and determined it was due to a service disabled on the server running the automated patch management application Which of the following
would Be the MOST efficient way to avoid similar audit findings in the future?
- A. Implement a manual patch management application package to regain greater control over the process
- B. Create a patch management policy that requires all servers to be patched within 30 days of patch release.
- C. Implement service monitoring to validate that tools are functioning properly.
- D. Set service on the patch management server to automatically run on start-up.
Answer: D
NEW QUESTION 12
A technician receives a report that a user’s workstation is experiencing no network connectivity. The technician investigates and notices the patch cable running the back of the user’s VoIP phone is routed directly under the rolling chair and has been smashed flat over time.
Which of the following is the most likely cause of this issue?
- A. Cross-talk
- B. Electromagnetic interference
- C. Excessive collisions
- D. Split pairs
Answer: C
NEW QUESTION 13
A company has established an ongoing vulnerability management program and procured the latest technology to support it. However, the program is failing because several vulnerabilities have not been detected. Which of the following will reduce the number of false negatives?
- A. Increase scan frequency.
- B. Perform credentialed scans.
- C. Update the security incident response plan.
- D. Reconfigure scanner to brute force mechanisms.
Answer: B
NEW QUESTION 14
An analyst received a forensically sound copy of an employee’s hard drive. The employee’s manager suspects inappropriate images may have been deleted from the hard drive. Which of the following could help the analyst recover the deleted evidence?
- A. File hashing utility
- B. File timestamps
- C. File carving tool
- D. File analysis tool
Answer: C
NEW QUESTION 15
A threat intelligence analyst who works for a technology firm received this report from a vendor.
“There has been an intellectual property theft campaign executed against organizations in the technology industry. Indicators for this activity are unique to each intrusion. The information that appears to be targeted is R&D data. The data exfiltration appears to occur over months via uniform TTPs. Please execute a defensive operation regarding this attack vector.”
Which of the following combinations suggests how the threat should MOST likely be classified and the type of analysis that would be MOST helpful in protecting against this activity?
- A. Polymorphic malware and secure code analysis
- B. Insider threat and indicator analysis
- C. APT and behavioral analysis
- D. Ransomware and encryption
Answer: B
NEW QUESTION 16
A company wants to update its acceptable use policy (AUP) to ensure it relates to the newly implemented password standard, which requires sponsored authentication of guest wireless devices. Which of the following is MOST likely to be incorporated in the AUP?
- A. Sponsored guest passwords must be at least ten characters in length and contain a symbol.
- B. The corporate network should have a wireless infrastructure that uses open authentication standards.
- C. Guests using the wireless network should provide valid identification when registering their wireless devices.
- D. The network should authenticate all guest users using 802.1x backed by a RADIUS or LDAP server.
Answer: C
NEW QUESTION 17
A newly discovered malware has a known behavior of connecting outbound to an external destination on port 27500 for the purpose of exfiltrating data. The following are four snippets taken from running netstat –an on separate Windows workstations: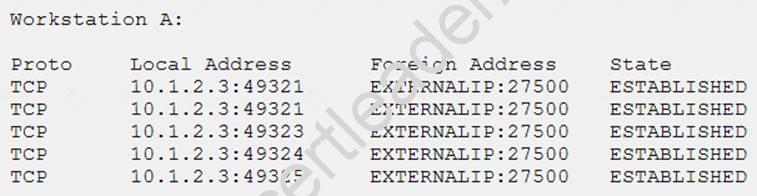
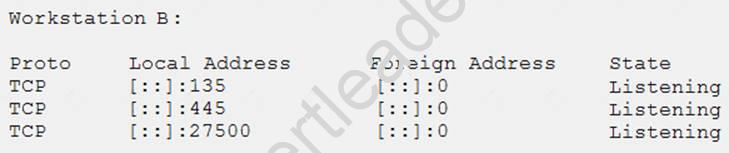
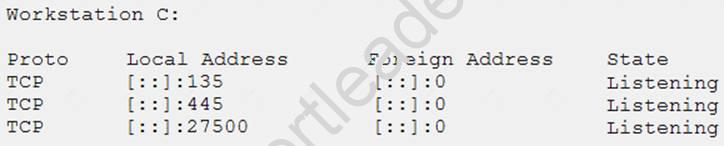
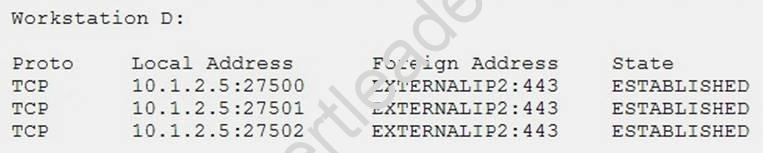
Based on the above information, which of the following is MOST likely to be exposed to this malware?
- A. Workstation A
- B. Workstation B
- C. Workstation C
- D. Workstation D
Answer: A
NEW QUESTION 18
A Linux-based file encryption malware was recently discovered in the wild. Prior to running the malware on a preconfigured sandbox to analyze its behavior, a security professional executes the following command:
umount –a –t cifs,nfs
Which of the following is the main reason for executing the above command?
- A. To ensure the malware is memory bound.
- B. To limit the malware’s reach to the local host.
- C. To back up critical files across the network
- D. To test if the malware affects remote systems
Answer: B
P.S. Easily pass CS0-001 Exam with 242 Q&As prep-labs.com Dumps & pdf Version, Welcome to Download the Newest prep-labs.com CS0-001 Dumps: https://www.prep-labs.com/dumps/CS0-001/ (242 New Questions)