Cause all that matters here is passing exam with CS0-001 Exam Questions. Cause all that you need is a high score of CS0-001 Study Guides. The only one thing you need to do is downloading CS0-001 Free Practice Questions free now. We will not let you down with our money-back guarantee.
Online CompTIA CS0-001 free dumps demo Below:
NEW QUESTION 1
Which of the following is a feature of virtualization that can potentially create a single point of failure?
- A. Server consolidation
- B. Load balancing hypervisors
- C. Faster server provisioning
- D. Running multiple OS instances
Answer: A
NEW QUESTION 2
The new Chief Technology Officer (CTO) is seeking recommendations for network monitoring services for the local intranet. The CTO would like the capability to monitor all traffic to and from the gateway, as well as the capability to block certain content. Which of the following recommendations would meet the needs of the organization?
- A. Recommend setup of IP filtering on both the internal and external interfaces of the gateway router.
- B. Recommend installation of an IDS on the internal interface and a firewall on the external interface of the gateway router.
- C. Recommend installation of a firewall on the internal interface and a NIDS on the external interface of the gateway router.
- D. Recommend installation of an IPS on both the internal and external interfaces of the gateway router.
Answer: C
NEW QUESTION 3
In an effort to be proactive, an analyst has run an assessment against a sample workstation before auditors visit next month. The scan results are as follows: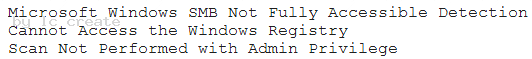
Based on the output of the scan, which of the following is the BEST answer?
- A. Failed credentialed scan
- B. Failed compliance check
- C. Successful sensitivity level check
- D. Failed asset inventory
Answer: A
NEW QUESTION 4
During a routine network scan, a security administrator discovered an unidentified service running on a new embedded and unmanaged HVAC controller, which is used to monitor the company’s datacenter:
The enterprise monitoring service requires SNMP and SNMPTRAP connectivity to operate. Which of the following should the security administrator implement to harden the system?
- A. Patch and restart the unknown service.
- B. Segment and firewall the controller’s network.
- C. Disable the unidentified service on the controller.
- D. Implement SNMPv3 to secure communication.
- E. Disable TCP/UDP ports 161 through 163.
Answer: A
NEW QUESTION 5
As part of the SDLC, software developers are testing the security of a new web application by inputting large amounts of random data. Which of the following types of testing is being performed?
- A. Fuzzing
- B. Regression testing
- C. Stress testing
- D. Input validation
Answer: A
NEW QUESTION 6
A security analyst is attempting to configure a vulnerability scan for a new segment on the network. Given the requirement to prevent credentials from traversing the network while still conducting a credentialed scan, which of the following is the BEST choice?
- A. Install agents on the endpoints to perform the scan
- B. Provide each endpoint with vulnerability scanner credentials
- C. Encrypt all of the traffic between the scanner and the endpoint
- D. Deploy scanners with administrator privileges on each endpoint
Answer: A
NEW QUESTION 7
Which of the following represent the reasoning behind careful selection of the timelines and time-of-day boundaries for an authorized penetration test? (Select TWO).
- A. To schedule personnel resources required for test activities
- B. To determine frequency of team communication and reporting
- C. To mitigate unintended impacts to operations
- D. To avoid conflicts with real intrusions that may occur
- E. To ensure tests have measurable impact to operations
Answer: AC
NEW QUESTION 8
A technician is running an intensive vulnerability scan to detect which ports are open to exploit. During the scan, several network services are disabled and production is affected. Which of the following sources would be used to evaluate which network service was interrupted?
- A. Syslog
- B. Network mapping
- C. Firewall logs
- D. NIDS
Answer: A
NEW QUESTION 9
A cybersecurity analyst is reviewing the following outputs: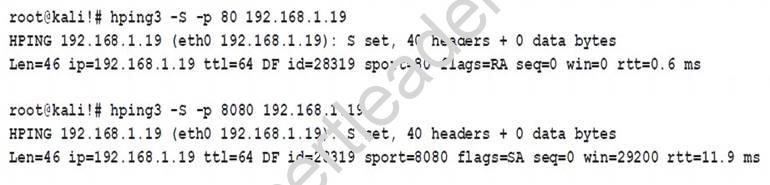
Which of the following can the analyst infer from the above output?
- A. The remote host is redirecting port 80 to port 8080.
- B. The remote host is running a service on port 8080.
- C. The remote host’s firewall is dropping packets for port 80.
- D. The remote host is running a web server on port 80.
Answer: B
NEW QUESTION 10
A security analyst has been asked to remediate a server vulnerability. Once the analyst has located a patch for the vulnerability, which of the following should happen NEXT?
- A. Start the change control process.
- B. Rescan to ensure the vulnerability still exists.
- C. Implement continuous monitoring.
- D. Begin the incident response process.
Answer: A
NEW QUESTION 11
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week: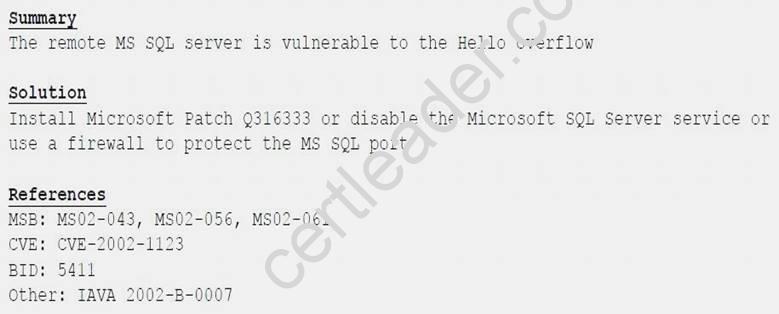
Based on the above information, which of the following should the system administrator do? (Select TWO).
- A. Verify the vulnerability using penetration testing tools or proof-of-concept exploits.
- B. Review the references to determine if the vulnerability can be remotely exploited.
- C. Mark the result as a false positive so it will show in subsequent scans.
- D. Configure a network-based ACL at the perimeter firewall to protect the MS SQL port.
- E. Implement the proposed solution by installing Microsoft patch Q316333.
Answer: DE
NEW QUESTION 12
An organization wants to remediate vulnerabilities associated with its web servers. An initial vulnerability scan has been performed, and analysts are reviewing the results. Before starting any remediation, the analysts want to remove false positives to avoid spending time on issues that are not actual vulnerabilities. Which of the following would be an indicator of a likely false positive?
- A. Reports show the scanner compliance plug-in is out-of-date.
- B. Any items labeled ‘low’ are considered informational only.
- C. The scan result version is different from the automated asset inventory.
- D. ‘HTTPS’ entries indicate the web page is encrypted securely.
Answer: B
NEW QUESTION 13
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has already identified active hosts in the network and is now scanning individual hosts to determine if any are running a web server. The output from the latest scan is shown below: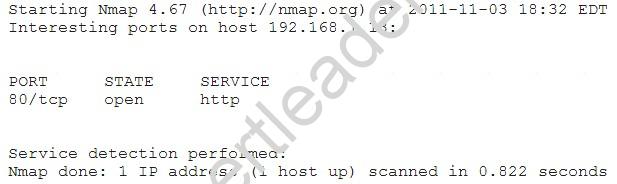
Which of the following commands would have generated the output above?
- A. –nmap –sV 192.168.1.13 –p 80
- B. –nmap –sP 192.168.1.0/24 –p ALL
- C. –nmap –sV 192.168.1.1 –p 80
- D. –nmap –sP 192.168.1.13 –p ALL
Answer: A
NEW QUESTION 14
A cybersecurity analyst is reviewing the current BYOD security posture. The users must be able to synchronize their calendars, email, and contacts to a smartphone or other personal device. The
recommendation must provide the most flexibility to users. Which of the following recommendations would meet both the mobile data protection efforts and the business requirements described in this scenario?
- A. Develop a minimum security baseline while restricting the type of data that can be accessed.
- B. Implement a single computer configured with USB access and monitored by sensors.
- C. Deploy a kiosk for synchronizing while using an access list of approved users.
- D. Implement a wireless network configured for mobile device access and monitored by sensors.
Answer: D
NEW QUESTION 15
A security operations team was alerted to abnormal DNS activity coming from a user’s machine. The team performed a forensic investigation and discovered a host had been compromised. Malicious code was using DNS as a tunnel to extract data from the client machine, which had been leaked and transferred to an unsecure public Internet site. Which of the following BEST describes the attack?
- A. Phishing
- B. Pharming
- C. Cache poisoning
- D. Data exfiltration
Answer: D
NEW QUESTION 16
Review the following results:
Which of the following has occurred?
- A. This is normal network traffic.
- B. 123.120.110.212 is infected with a Trojan.
- C. 172.29.0.109 is infected with a worm.
- D. 172.29.0.109 is infected with a Trojan.
Answer: A
NEW QUESTION 17
The board of directors made the decision to adopt a cloud-first strategy. The current security infrastructure was designed for on-premise implementation. A critical application that is subject to the Federal Information Security Management Act (FISMA) of 2002 compliance has been identified as a candidate for a hybrid cloud deployment model. Which of the following should be conducted FIRST?
- A. Develop a request for proposal.
- B. Perform a risk assessment.
- C. Review current security controls.
- D. Review the SLA for FISMA compliance.
Answer: C
NEW QUESTION 18
An incident response report indicates a virus was introduced through a remote host that was connected to corporate resources. A cybersecurity analyst has been asked for a recommendation to solve this issue. Which of the following should be applied?
- A. MAC
- B. TAP
- C. NAC
- D. ACL
Answer: C
100% Valid and Newest Version CS0-001 Questions & Answers shared by prep-labs.com, Get Full Dumps HERE: https://www.prep-labs.com/dumps/CS0-001/ (New 242 Q&As)