Master the CS0-001 Dumps content and be ready for exam day success quickly with this CS0-001 Braindumps. We guarantee it!We make it a reality and give you real CS0-001 Dumps Questions in our CompTIA CS0-001 braindumps. Latest 100% VALID CS0-001 Dumps Questions at below page. You can use our CompTIA CS0-001 braindumps and pass your exam.
Check CS0-001 free dumps before getting the full version:
NEW QUESTION 1
Weeks before a proposed merger is scheduled for completion, a security analyst has noticed unusual traffic patterns on a file server that contains financial information. Routine scans are not detecting the signature of any known exploits or malware. The following entry is seen in the ftp server logs:
tftp –I 10.1.1.1 GET fourthquarterreport.xls
Which of the following is the BEST course of action?
- A. Continue to monitor the situation using tools to scan for known exploits.
- B. Implement an ACL on the perimeter firewall to prevent data exfiltration.
- C. Follow the incident response procedure associate with the loss of business critical data.
- D. Determine if any credit card information is contained on the server containing the financials.
Answer: C
NEW QUESTION 2
During a network reconnaissance engagement, a penetration tester was given perimeter firewall ACLs to accelerate the scanning process. The penetration tester has decided to concentrate on trying to brute force log in to destination IP address 192.168.192.132 via secure shell.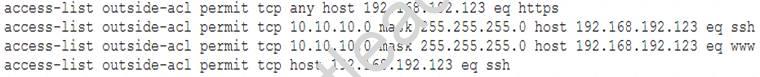
Given a source IP address of 10.10.10.30, which of the following ACLs will permit this access?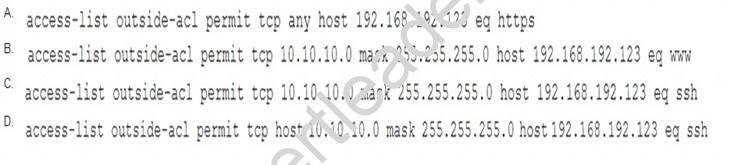
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: C
NEW QUESTION 3
A threat intelligence feed has posted an alert stating there is a critical vulnerability in the kernel. Unfortunately, the company’s asset inventory is not current. Which of the following techniques would a cybersecurity analyst perform to find all affected servers within an organization?
- A. A manual log review from data sent to syslog
- B. An OS fingerprinting scan across all hosts
- C. A packet capture of data traversing the server network
- D. A service discovery scan on the network
Answer: B
NEW QUESTION 4
A nuclear facility manager (determined the need to monitor utilization of water within the facility. A startup company just announced a state-of-the-art solution to address the need for integrality 'be business and ICS networks The solution leqmies a very small agent lo be installed on the 1CS equipment Which of the following is the MOST important security control for the manager to invest in to protect the facility?
- A. Run a penetration lest on the installed agent.
- B. Require that the solution provider make the agent source code available for analysis.
- C. Require thorough guides for administrator and users
- D. Install the agent tor a week on a test system and monitor the activities
Answer: D
NEW QUESTION 5
On winch of the following organizational resources is the lack of an enabled password or PIN a common vulnerability?
- A. VDI systems
- B. Mobile devices
- C. Enterprise server OSs
- D. VPNs
- E. VoIP phones
Answer: B
NEW QUESTION 6
An insurance company employs quick-response team drivers that can corporate issued mobile devices with the insurance company's app installed on them Devices are configuration hardened by an MOM and kept up to date. The employees use the app to collect insurance claim into formation and process payments Recently, a number of customers have filed complaints of credit card fraud against the insurance company, Which occurred shortly after their payments were processed via the mobile app. The cyber-incidence response team has been asked investigate. Which of the following is MOST likely the cause? ^
- A. The MDM server Is misconfigured.
- B. The app does not employ TLS.
- C. USB tethering is enabled.
- D. 3G and less secure cellular technologies ate not restricted.
Answer: B
NEW QUESTION 7
A company that is hiring a penetration tester wants to exclude social engineering from the list of authorized activities. Which of the following documents should include these details?
- A. Acceptable use policy
- B. Service level agreement
- C. Rules of engagement
- D. Memorandum of understanding
- E. Master service agreement
Answer: C
NEW QUESTION 8
Which of the following utilities could be used to resolve an IP address to a daman name, assuming the address has a PTR record?
- A. ifconfig
- B. ping
- C. arp
- D. nbtotot
Answer: B
NEW QUESTION 9
An investigation showed a worm was introduced from an engineer’s laptop. It was determined the company does not provide engineers with company-owned laptops, which would be subject to company policy and technical controls.
Which of the following would be the MOST secure control implement?
- A. Deploy HIDS on all engineer-provided laptops, and put a new router in the management network.
- B. Implement role-based group policies on the management network for client access.
- C. Utilize a jump box that is only allowed to connect to clients from the management network.
- D. Deploy a company-wide approved engineering workstation for management access.
Answer: D
NEW QUESTION 10
A system administrator who was using an account with elevated privileges deleted a large amount of log files generated by a virtual hypervisor in order to free up disk space. These log files are needed by the security team to analyze the health of the virtual machines. Which of the following compensating controls would help prevent this from reoccurring? (Select two.)
- A. Succession planning
- B. Separation of duties
- C. Mandatory vacation
- D. Personnel training
- E. Job rotation
Answer: BD
NEW QUESTION 11
The following IDS log was discovered by a company’s cybersecurity analyst:
Which of the following was launched against the company based on the IDS log?
- A. SQL injection attack
- B. Cross-site scripting attack
- C. Buffer overflow attack
- D. Online password crack attack
Answer: C
NEW QUESTION 12
Which of the following items represents a document that includes detailed information on when an incident was detected, how impactful the incident was, and how it was remediated, in addition to incident response effectiveness and any identified gaps needing improvement?
- A. Forensic analysis report
- B. Chain of custody report
- C. Trends analysis report
- D. Lessons learned report
Answer: D
NEW QUESTION 13
A medical organization recently started accepting payments over the phone. The manager is concerned about the impact of the storage of different types of data. Which of the following types of data incurs the highest regulatory constraints?
- A. PHI
- B. PCI
- C. Pll
- D. IP
Answer: B
NEW QUESTION 14
A security analyst is reviewing a report from the networking department that describes an increase in network utilization, which is causing network performance issues on some systems. A top talkers report over a
five-minute sample is included.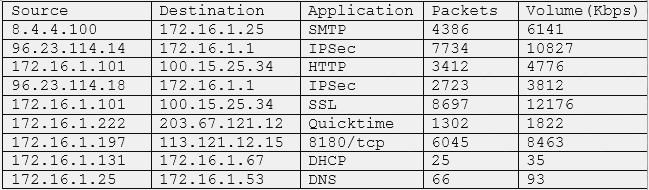
Given the above output of the sample, which of the following should the security analyst accomplish FIRST to help track down the performance issues?
- A. Perform reverse lookups on each of the IP addresses listed to help determine if the traffic necessary.
- B. Recommend that networking block the unneeded protocols such as Quicklime lo clear up some of the congestion
- C. Put ACLs in place to restrict traffic destined for random or non-default application ports
- D. Quarantine the top talker on the network and begin to investigate any potential threats caused by the excessive traffic
Answer: A
NEW QUESTION 15
During a web application vulnerability scan, it was discovered that the application would display inappropriate data after certain key phrases were entered into a webform connected to a SQL database server. Which of the following should be used to reduce the likelihood of this type of attack returning sensitive data?
- A. Static code analysis
- B. Peer review code
- C. Input validation
- D. Application fuzzing
Answer: C
NEW QUESTION 16
After a recent security breach, it was discovered that a developer had promoted code that had been written to the production environment as a hotfix to reserve a user navigation issue that was causing issues for several customers. The code had inadvertently granted administrative privileges to all users, allowing inappropriate access to sensitive data and reports. Which of the following could have prevented the code from being released into the production environment?
- A. Cross training
- B. Succession planning
- C. Automated reporting
- D. Separation of duties
Answer: D
NEW QUESTION 17
A security analyst is conducting a vulnerability assessment of older SCADA devices on the corporate network. Which of the following compensating controls is likely to prevent the scans from providing value?
- A. Access control list network segmentation that prevents access to the SCADA devices inside the network.
- B. Detailed and tested firewall rules that effectively prevent outside access of the SCADA devices.
- C. Implementation of a VLAN that allows all devices on the network to see all SCADA devices on the network.
- D. SCADA systems configured with ‘SCADA SUPPORT’=ENABLE
Answer: B
NEW QUESTION 18
A security analyst is reviewing packet captures for a specific server that is suspected of containing malware and discovers the following packets:
Which of the following traffic patterns or data would be MOST concerning to the security analyst?
- A. Ports used for SMTP traffic from 73.252.34.101
- B. Unencrypted password sent from 103.34.243.12
- C. Anonymous access granted by 103.34.243.12
- D. Ports used HTTP traffic from 202.53.245.78
Answer: C
100% Valid and Newest Version CS0-001 Questions & Answers shared by Simply pass, Get Full Dumps HERE: https://www.simply-pass.com/CompTIA-exam/CS0-001-dumps.html (New 242 Q&As)