It is impossible to pass CompTIA SY0-701 exam without any help in the short term. Come to Examcollection soon and find the most advanced, correct and guaranteed CompTIA SY0-701 practice questions. You will get a surprising result by our Updated CompTIA Security+ Exam practice guides.
Free demo questions for CompTIA SY0-701 Exam Dumps Below:
NEW QUESTION 1
The application development teams have been asked to answer the following questions:  Does this application receive patches from an external source?
Does this application receive patches from an external source? Does this application contain open-source code?
Does this application contain open-source code?  Is this application accessible by external users?
Is this application accessible by external users? Does this application meet the corporate password standard? Which of the following are these questions part of?
Does this application meet the corporate password standard? Which of the following are these questions part of?
- A. Risk control self-assessment
- B. Risk management strategy
- C. Risk acceptance
- D. Risk matrix
Answer: A
Explanation:
A risk control self-assessment (RCSA) is a process that allows an organization to identify, evaluate, and mitigate the risks associated with its activities, processes, systems, and products. A RCSA involves asking relevant questions to assess the effectiveness of existing controls and identify any gaps or weaknesses that need improvement. A RCSA also helps to align the risk appetite and tolerance of the organization with its strategic objectives and performance.
The application development teams have been asked to answer questions related to their applications’ security posture, such as whether they receive patches from an external source, contain open-source code, are accessible by external users, or meet the corporate password standard. These questions are part of a RCSA process that aims to evaluate the potential risks and vulnerabilities associated with each application and determine how well they are managed and mitigated.
NEW QUESTION 2
A security analyst is taking part in an evaluation process that analyzes and categorizes threat actors Of real-world events in order to improve the incident response team's process. Which Of the following is the analyst most likely participating in?
- A. MITRE ATT&CK
- B. Walk-through
- C. Red team
- D. Purple team-I
- E. TAXI
Answer: A
Explanation:
MITRE ATT&CK is a knowledge base and framework that analyzes and categorizes threat actors and
real-world events based on their tactics, techniques and procedures. It can help improve the incident response team’s process by providing a common language and reference for identifying, understanding and mitigating threats
NEW QUESTION 3
A security administrator needs to inspect in-transit files on the enterprise network to search for PI I credit card data, and classification words Which of the following would be the best to use?
- A. IDS solution
- B. EDR solution
- C. HIPS software solution
- D. Network DLP solution
Answer: D
Explanation:
A network DLP (Data Loss Prevention) solution is a tool that monitors and controls the data that is transmitted over a network. It can inspect in-transit files on the enterprise network to search for PII (Personally Identifiable Information), credit card data, and classification words by using predefined rules and policies, and then block, encrypt, quarantine, or alert on any sensitive data that is detected or leaked.
NEW QUESTION 4
A security analyst needs to implement security features across smartphones. laptops, and tablets. Which of the following would be the most effective across heterogeneous platforms?
- A. Enforcing encryption
- B. Deploying GPOs
- C. Removing administrative permissions
- D. Applying MDM software
Answer: D
Explanation:
MDM stands for Mobile Device Management, which is a software solution that can manage and secure smartphones, laptops, tablets and other mobile devices across heterogeneous platforms. MDM can enforce security features such as encryption, password policies, remote wipe, device tracking, app control and more. MDM can also monitor and update the devices remotely and provide reports and alerts on their status. MDM is the most effective solution to implement security features across heterogeneous platforms, as it can provide centralized and consistent management of various types of devices. Verified References: Security+ (Plus) Certification | CompTIA IT Certifications
Security+ (Plus) Certification | CompTIA IT Certifications
https://www.comptia.org/certifications/security (See Domain 3: Architecture and Design, Objective 3.4: Given a scenario, implement secure systems design.) CompTIA Security+ 601 - Infosec
CompTIA Security+ 601 - Infosec
https://www.infosecinstitute.com/wp-content/uploads/2021/03/CompTIA-Security-eBook.pdf (See Security+: 5 in-demand cybersecurity skills, Implementation) Certification Security+ | CompTIA https://www.comptia.org/landing/securityplus/index.html (See Exam Objectives)
Certification Security+ | CompTIA https://www.comptia.org/landing/securityplus/index.html (See Exam Objectives)
NEW QUESTION 5
Leveraging the information supplied below, complete the CSR for the server to set up TLS (HTTPS)
• Hostname: ws01
• Domain: comptia.org
• IPv4: 10.1.9.50
• IPV4: 10.2.10.50
• Root: home.aspx
• DNS CNAME:homesite. Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.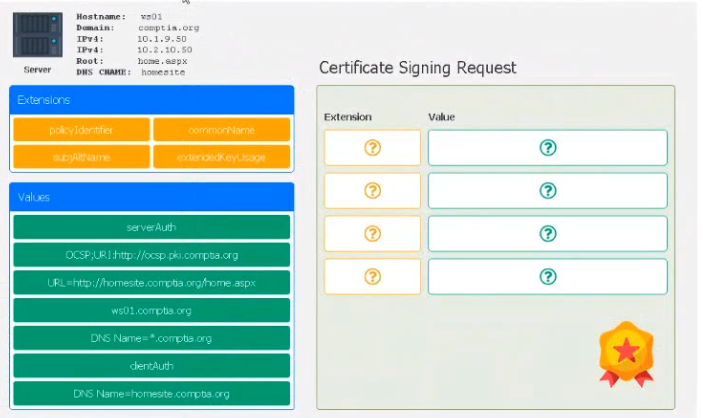
Solution:
Graphical user interface, application Description automatically generated
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 6
Which of the following Is the BEST reason to maintain a functional and effective asset management policy that aids in ensuring the security of an organization?
- A. To provide data to quantify risk based on the organization's systems
- B. To keep all software and hardware fully patched for known vulnerabilities
- C. To only allow approved, organization-owned devices onto the business network
- D. To standardize by selecting one laptop model for all users in the organization
Answer: A
Explanation:
An effective asset management policy helps an organization understand and manage the systems, hardware, and software it uses, and how they are used, including their vulnerabilities and risks. This information is crucial for accurately identifying and assessing risks to the organization, and making informed decisions about how to mitigate those risks. This is the best reason to maintain an effective asset management policy.
Reference: CompTIA Security+ Study Guide (SY0-601) 7th Edition by Emmett Dulaney, Chuck Easttom
NEW QUESTION 7
Which of the following incident response phases should the proper collection of the detected 'ocs and establishment of a chain of custody be performed before?
- A. Containment
- B. Identification
- C. Preparation
- D. Recovery
Answer: A
Explanation:
Containment is the phase where the incident response team tries to isolate and stop the spread of the incident12. Before containing the incident, the team should collect and preserve any evidence that may be useful for analysis and investigation12. This includes documenting the incident details, such as date, time, location, source, and impact12. It also includes establishing a chain of custody, which is a record of who handled the evidence, when, where, how, and why3. A chain of custody ensures the integrity and admissibility of the evidence in court or other legal proceedings3.
NEW QUESTION 8
A third party asked a user to share a public key for secure communication. Which of the following file formats should the user choose to share the key?
- A. .pfx
- B. .csr
- C. .pvk
- D. .cer
Answer: D
Explanation:
A user should choose the .cer file format to share a public key for secure communication. A .cer file is a public key certificate that can be shared with third parties to enable secure communication.
References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 6: Cryptography, pp. 301-302.
A public key is a cryptographic key that can be used to encrypt or verify data. A public key file is a file that contains one or more public keys in a specific format.
There are different formats for public key files, depending on the application and the algorithm used. Some of the common formats are: .pfx: This is a file format that stores a certificate and its private and public keys. It is also known as PKCS#12 or Personal Information Exchange. It is used by some applications such as Microsoft Internet Explorer and Outlook to import and export certificates and keys.1
.pfx: This is a file format that stores a certificate and its private and public keys. It is also known as PKCS#12 or Personal Information Exchange. It is used by some applications such as Microsoft Internet Explorer and Outlook to import and export certificates and keys.1 .csr: This is a file format that stores a Certificate Signing Request, which is a message sent to a Certificate Authority (CA) to request a digital certificate. It contains the public key and some information about the identity of the requester. It is also known as PKCS#10 or Certification Request Syntax.2
.csr: This is a file format that stores a Certificate Signing Request, which is a message sent to a Certificate Authority (CA) to request a digital certificate. It contains the public key and some information about the identity of the requester. It is also known as PKCS#10 or Certification Request Syntax.2 .pvk: This is a file format that stores a private key for Microsoft Authenticode code signing. It is used with a .spc file that contains the certificate and public key.3
.pvk: This is a file format that stores a private key for Microsoft Authenticode code signing. It is used with a .spc file that contains the certificate and public key.3 .cer: This is a file format that stores a certificate, which is a document that binds a public key to an identity. It is also known as DER or Distinguished Encoding Rules. It is used by some applications such as OpenSSL and Java to read and write certificates.4
.cer: This is a file format that stores a certificate, which is a document that binds a public key to an identity. It is also known as DER or Distinguished Encoding Rules. It is used by some applications such as OpenSSL and Java to read and write certificates.4
NEW QUESTION 9
A security administrator needs to add fault tolerance and load balancing to the connection from the file server to the backup storage. Which of the following is the best choice to achieve this objective?
- A. Multipathing
- B. RAID
- C. Segmentation
- D. 8021.1
Answer: A
Explanation:
to achieve the objective of adding fault tolerance and load balancing to the connection from the file server to the backup storage is multipathin1g. Multipathing is a technique that allows a system to use more than one path to access a storage device1. This can improve performance by distributing the workload across multiple paths, and also provide fault tolerance by switching to an alternative path if one path fails1. Multipathing can be implemented using software or hardware solutions1.
NEW QUESTION 10
A systems analyst determines the source of a high number of connections to a web server that were initiated by ten different IP addresses that belong to a network block in a specific country. Which of the following techniques will the systems analyst MOST likely implement to address this issue?
- A. Content filter
- B. SIEM
- C. Firewall rules
- D. DLP
Answer: C
Explanation:
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. The systems analyst can use firewall rules to block connections from the ten IP addresses in question, or from the entire network block in the specific country. This would be a quick and effective way to address the issue of high connections to the web server initiated by these IP addresses.
Reference: CompTIA Security+ SY0-601 Official Text Book, Chapter 5: "Network Security".
NEW QUESTION 11
Which of the following automation use cases would best enhance the security posture Of an organi-zation by rapidly updating permissions when employees leave a company Or change job roles inter-nally?
- A. Provisioning resources
- B. Disabling access
- C. APIs
- D. Escalating permission requests
Answer: B
Explanation:
Disabling access is an automation use case that can enhance the security posture of an organization by rapidly updating permissions when employees leave a company or change job roles internally. It can prevent unauthorized access and data leakage by revoking or modifying the access rights of employees based on their current status and role.
NEW QUESTION 12
A security analyst reviews web server logs and notices the following line: 104.35. 45.53 [22/May/2020:07 : 00:58 +0100] "GET . UNION ALL SELECT
user login, user _ pass, user email from wp users—— HTTP/I.I" 200 1072
http://www.example.com/wordpress/wp—admin/
Which of the following vulnerabilities is the attacker trying to exploit?
- A. SSRF
- B. CSRF
- C. xss
- D. SQLi
Answer: D
Explanation:
SQLi stands for SQL injection, which is a type of web security vulnerability that allows an attacker to execute malicious SQL statements on a database server. SQLi can result in data theft, data corruption, denial of service, or remote code execution.
The attacker in the web server log is trying to exploit a SQLi vulnerability by sending a malicious GET request that contains a UNION ALL SELECT statement. This statement is used to combine the results of two or more SELECT queries into a single result set. The attacker is attempting to retrieve user login, user pass, and user email from the wp users table, which is a WordPress database table that stores user information. The attacker may use this information to compromise the WordPress site or the users’ accounts.
NEW QUESTION 13
A security analyst was asked to evaluate a potential attack that occurred on a publicly accessible section of the company's website. The malicious actor posted an entry in an attempt to trick users into clicking the following:
Which of the following was most likely observed?
- A. DLL injection
- B. Session replay
- C. SQLi
- D. xss
Answer: D
Explanation:
Cross-site scripting is a type of web application attack that involves injecting malicious code or scripts into a trusted website or application. The malicious code or script can execute in the browser of the victim who visits the website or application, and can perform actions such as stealing cookies, redirecting to malicious sites, displaying fake content, or compromising the system. References:
https://www.comptia.org/blog/what-is-cross-site-scripting
https://www.certblaster.com/wp-content/uploads/2020/11/CompTIA-Security-SY0-601-Exam-Objectives-1.0.pd
NEW QUESTION 14
An attacker replaces a digitally signed document with another version that goes unnoticed Upon reviewing the document's contents the author notices some additional verbiage that was not originally in the document but cannot validate an integrity issue. Which of the following attacks was used?
- A. Cryptomalware
- B. Hash substitution
- C. Collision
- D. Phishing
Answer: B
Explanation:
This type of attack occurs when an attacker replaces a digitally signed document with another version that has a different hash value. The author would be able to notice the additional verbiage, however, since the hash value would have changed, they would not be able to validate an integrity issue.
NEW QUESTION 15
Which of the following best reduces the security risks introduced when running systems that have expired vendor support and lack an immediate replacement?
- A. Implement proper network access restrictions.
- B. Initiate a bug bounty program.
- C. Classify the system as shadow IT.
- D. Increase the frequency of vulnerability scans.
Answer: A
Explanation:
Network access restrictions can limit the exposure of systems that have expired vendor support and lack an immediate replacement, as they can prevent unauthorized or unnecessary access to those systems from other devices or networks. Network access restrictions can include firewalls, network segmentation, VPNs, access control lists, and other methods that can filter or block traffic based on predefined rules or policies. Network access restrictions can reduce the security risks introduced by running systems that have expired vendor support, as they can mitigate the impact of potential vulnerabilities or exploits that may affect those systems. Verified References: CompTIA Security+ Certification Exam Objectives Version 3.0 https://www.comptia.jp/pdf/Security%2B%20SY0-601%20Exam%20Objectives.pdf (See Domain 2.1: Given a scenario, implement secure protocols.)
CompTIA Security+ Certification Exam Objectives Version 3.0 https://www.comptia.jp/pdf/Security%2B%20SY0-601%20Exam%20Objectives.pdf (See Domain 2.1: Given a scenario, implement secure protocols.) CompTIA Security+ SY0-501 Study Guide
CompTIA Security+ SY0-501 Study Guide
https://www.certblaster.com/wp-content/uploads/2017/10/CompTIA-Security-SY0-501-Study-Guide.pdf (See Chapter 2: Technologies and Tools, Section 2.5: Firewall and Network Security Appliances.)
NEW QUESTION 16
After a phishing scam fora user's credentials, the red team was able to craft payload to deploy on a server. The attack allowed the installation of malicious software that initiates a new remote session
Which of the following types of attacks has occurred?
- A. Privilege escalation
- B. Session replay
- C. Application programming interface
- D. Directory traversal
Answer: A
Explanation:
"Privilege escalation is the act of exploiting a bug, design flaw, or configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user." In this scenario, the red team was able to install malicious software, which would require elevated privileges to access and install. Therefore, the type of attack that occurred is privilege escalation. References: CompTIA Security+ Study Guide, pages 111-112
NEW QUESTION 17
A security administrator Installed a new web server. The administrator did this to Increase the capacity (or an application due to resource exhaustion on another server. Which o( the following algorithms should the administrator use to split the number of the connections on each server In half?
- A. Weighted response
- B. Round-robin
- C. Least connection
- D. Weighted least connection
Answer: B
Explanation:
The administrator should use a round-robin algorithm to split the number of connections on each server in half. Round-robin is a load-balancing algorithm that distributes incoming requests to the available servers one by one in a cyclical order. This helps to evenly distribute the load across all of the servers, ensuring that no single server is overloaded.
NEW QUESTION 18
......
P.S. Easily pass SY0-701 Exam with 0 Q&As Dumpscollection.com Dumps & pdf Version, Welcome to Download the Newest Dumpscollection.com SY0-701 Dumps: https://www.dumpscollection.net/dumps/SY0-701/ (0 New Questions)