Cause all that matters here is passing exam with . Cause all that you need is a high score of . The only one thing you need to do is downloading free now. We will not let you down with our money-back guarantee.
Check 70-640 free dumps before getting the full version:
NEW QUESTION 1
Your company has an Active Directory domain. A user attempts to log on to the domain from a client computer and receives the following message: "This user account has expired. Ask your administrator to reactivate the account."
You need to ensure that the user is able to log on to the domain.
What should you do?
- A. Modify the properties of the user account to set the account to never expir
- B. Modify the properties of the user account to extend the Logon Hours settin
- C. Modify the default domain policy to decrease the account lockout duratio
- D. Modify the properties of the user account to set the password to never expir
Answer: A
Explanation: 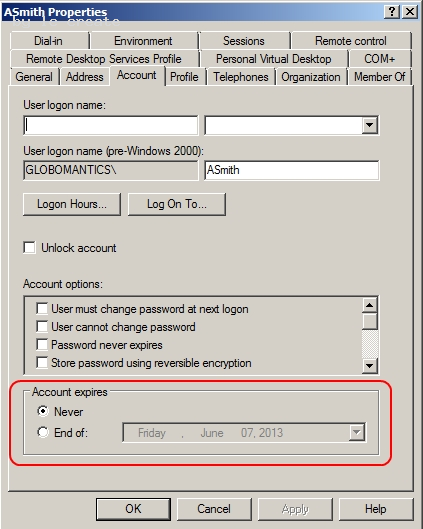
C:Documents and Settingsusernwz1Desktop1.PNG
Further information: http://technet.microsoft.com/en-us/library/dd145547.aspx User Properties - Account Tab Account expires Sets the account expiration policy for this user. You can select between the following options: Use Never to specify that the selected account will never expire. This option is the default for new users. Select End of and then select a date if you want to have the user's account expire on a specified date.
NEW QUESTION 2
Your network contains a domain controller that runs Windows Server 2008 R2.
You need to change the location of the Active Directory log files.
Which tool should you use?
- A. Dsamain
- B. Dsmgmt
- C. Dsmove
- D. Ntdsutil
Answer: AD
Explanation: http://support.microsoft.com/kb/257420 How To Move the Ntds.dit File or Log Files Moving a Database or Log File
1. Restart the domain controller.
2. Press F8 at the Startup menu, and then click Directory Services Restore Mode.
3. Select the appropriate installation if more than one exists, and then log on as an
administrator at the logon prompt.
4. Start a command prompt, and then type ntdsutil.exe.NOTE: To get a list of commands
that you can use at the Ntdsutil prompt, type ?
5. At a Ntdsutil prompt, type files.
6. At the File Maintenance prompt, use one or both of the following procedures:
* To move a database, type move db to %s, where %s is the drive and folder where you
want the database moved.
* To move log files, type move logs to %s, where %s is the drive and folder where you want
the log files moved.
7. To view the log files or database, type info. To verify the integrity of the database at its
new location, type integrity.
8. Type quit, and then type quit to return to a command prompt.
9. Restart the computer in Normal mode.
NOTE: When you move the database and log files, you must back up the domain
controller.
NEW QUESTION 3
Your company has a main office and four branch offices. An Active Directory site exists for each office. Each site contains one domain controller. Each branch office site has a site link to the main office site.
You discover that the domain controllers in the branch offices sometimes replicate directly to each other.
You need to ensure that the domain controllers in the branch offices only replicate to the domain controller in the main office.
What should you do?
- A. Modify the firewall settings for the main office sit
- B. Disable the Knowledge Consistency Checker (KCC) for each branch office sit
- C. Disable site link bridgin
- D. Modify the security settings for the main office sit
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/cc757117.aspx
Configuring site link bridges
By default, all site links are bridged, or transitive. This allows any two sites that are not connected by an explicit site link to communicate directly, through a chain of intermediary site links and sites. One advantage to bridging all site links is that your network is easier to maintain because you do not need to create a site link to describe every possible path between pairs of sites.
Generally, you can leave automatic site link bridging enabled. However, you might want to disable automatic site link bridging and create site link bridges manually just for specific site links, in the following cases:
You have a network routing or security policy in place that prevents every domain controller from being able to directly communicate with every other domain controller.
NEW QUESTION 4
You have an enterprise subordinate certification authority (CA). The CA is configured to use a hardware security module.
You need to back up Active Directory Certificate Services on the CA.
Which command should you run?
- A. certutil.exe backup
- B. certutil.exe backupdb
- C. certutil.exe backupkey
- D. certutil.exe store
Answer: B
Explanation:
Because a hardware security module (HSM) is used that stores the private keys, the command certutil. exe -backup would fail, since we cannot extract the private keys from the module. The HSM should have a proprietary procedure for that. The given commands are: certutil -backup Backup set includes certificate database, CA certificate an the CA key pair certutil -backupdb Backup set only includes certificate database certutil -backupkey Backup set only includes CA certificate and the CA key pair certutil –store Provides a dump of the certificate store onscreen.
Since we cannot extract the keys from the HSM we have to use backupdb. Explanation 1: Microsoft Windows Server(TM) 2003 PKI and Certificate Security (Microsoft Press, 2004) page 215 For the commands listed above. Explanation 2: http://technet.microsoft.com/en-us/library/cc732443.aspx Certutil.exe is a command-line program that is installed as part of Certificate Services. You can use Certutil.exe to dump and display certification authority (CA) configuration information, configure Certificate Services, back up and restore CA components, and verify certificates, key pairs, and certificate chains. Syntax Certutil <-parameter> [-parameter] Parameter -backupdb Backup the Active Directory Certificate Services database Explanation 3: http://poweradmin.se/blog/2010/01/11/backup-and-restore-for-active-directory-certificate-services/
NEW QUESTION 5
Your company has a single Active Directory domain. All domain controllers run Windows Server 2003.
You install Windows Server 2008 R2 on a server.
You need to add the new server as a domain controller in your domain.
What should you do first?
- A. On a domain controller run adprep /rodcpre
- B. On the new server, run dcpromo /ad
- C. On the new server, run dcpromo /createdcaccoun
- D. On a domain controller, run adprep /forestpre
Answer: D
Explanation:
http://social.technet.microsoft.com/Forums/en-US/winserverDS/thread/9931e32f-6302-40f0-a7a1-2598a96cd0c1/ DC promotion and adprep/forestprep
Q: I've tried to dcpromo a new Windows 2008 server installation to be a Domain Controller, running in an existing domain. I am informed that, first, I must run adprep/forestprep ("To install a domain controller into this Active Directory forest, you must first perpare the forest using "adprep/forestprep". The Adprep utility is available on the Windows Server 2008 installation media in the Windowssourcesadprep folder"
A1:
You can run adprep from an existing Windows Server 2003 domain controller. Copy the
contents of the sourcesadprep folder from the Windows Server 2008 installation DVD to
the schema master role holder and run Adprep from there.
A2: to introduce the first W2K8 DC within an AD forest....
(1) no AD forest exists yet:
--> on the stand alone server execute: DCPROMO
--> and provide the information needed
(2) an W2K or W2K3 AD forest already exists:
--> ADPREP /Forestprep on the w2k/w2k3 schema master (both w2k/w2k3 forests)
--> ADPREP /rodcprep on the w2k3 domain master (only w2k3 forests)
--> ADPREP /domainprep on the w2k3 infrastructure master (only w2k3 domains)
--> ADPREP /domainprep /gpprep on the w2k infrastructure master (only w2k domains)
--> on the stand alone server execute: DCPROMO
--> and provide the information needed
NEW QUESTION 6
You have two servers named Server1 and Server2. Both servers run Windows Server 2008 R2. Server1 is configured as an enterprise root certification authority (CA).
You install the Online Responder role service on Server2.
You need to configure Server1 to support the Online Responder.
What should you do?
- A. Import the enterprise root CA certificat
- B. Configure the Certificate Revocation List Distribution Point extensio
- C. Configure the Authority Information Access (AIA) extensio
- D. Add the Server2 computer account to the CertPublishers grou
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/cc732526.aspx
Configure a CA to Support OCSP Responders
To function properly, an Online Responder must have a valid Online Certificate Status Protocol (OCSP)Response Signing certificate. This OCSP Response Signing certificate is also needed if you are using a non-Microsoft OCSP responder.
Configuring a certification authority (CA) to support OCSP responder services includes the following steps:
1. Configure certificate templates and issuance properties for OCSP Response Signing certificates.
2. Configure enrollment permissions for any computers that will be hosting Online Responders.
3. If this is a Windows Server 2003–based CA, enable the OCSP extension in issued certificates.
NEW QUESTION 7
A corporate network contains a Windows Server 2008 R2 Active Directory forest.
You need to add a user principal name (UPN) suffix to the forest.
Which tool should you use?
- A. Active Directory module for Windows PowerShell
- B. Active Directory Administrative Center console
- C. Active Directory Sites and Services console
- D. Active Directory Users and Computers console
Answer: B
NEW QUESTION 8
Your network contains an Active Directory domain named contoso.com.
You have an organizational unit (OU) named Sales and an OU named Engineering.
You need to ensure that when users log on to client computers, they are added automatically to the local Administrators group. The users must be removed from the group when they log off of the client computers.
What should you do?
- A. Modify the Group Policy permission
- B. Enable block inheritanc
- C. Configure the link orde
- D. Enable loopback processing in merge mod
- E. Enable loopback processing in replace mod
- F. Configure WMI filterin
- G. Configure Restricted Group
- H. Configure Group Policy PExplanation
- I. Link the Group Policy object (GPO) to the Sales O
- J. Link the Group Policy object (GPO) to the Engineering O
Answer: H
Explanation:
http://daniel.streefkerkonline.com/managing-local-admins-using-gpp/
http://www.grouppolicy.biz/2010/01/how-to-use-group-policy-pExplanations-to-secure-local-administrator-groups/
NEW QUESTION 9
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 has the Active Directory Federation Services (AD FS) role installed.
You have an application named App1 that is configured to use Server1 for AD FS authentication.
You deploy a new server named Server2. Server2 is configured as an AD FS 2.0 server.
You need to ensure that App1 can use Server2 for authentication.
What should you do on Server2?
- A. Add an attribute stor
- B. Create a relying party trus
- C. Create a claims provider trus
- D. Create a relaying provider trus
Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/dd807132%28v=ws.10%29.aspx Create a Relying Party Trust Using Federation Metadata http://pipe2text.com/?page_id=815 Setting up a Relying Party Trust in ADFS 2.0 http://blogs.msdn.com/b/card/archive/2010/06/25/using-federation-metadata-to-establish-a-relying-party-trustin-ad-fs-2-0.aspx Using Federation Metadata to establish a Relying Party Trust in AD FS 2.0
NEW QUESTION 10
Your company has an Active Directory forest. Each regional office has an organizational unit (OU) named Marketing. The Marketing OU contains all users and computers in the region's Marketing department.
You need to install a Microsoft Office 2007 application only on the computers in the Marketing OUs.
You create a GPO named MarketingApps.
What should you do next?
- A. Configure the GPO to assign the application to the computer accoun
- B. Link the GPO to the domai
- C. Configure the GPO to assign the application to the user accoun
- D. Link the GPO to each Marketing O
- E. Configure the GPO to assign the application to the computer accoun
- F. Link the GPO to each Marketing O
- G. Configure the GPO to publish the application to the user accoun
- H. Link the GPO to each Marketing O
Answer: C
Explanation:
http://support.microsoft.com/kb/816102
You can use Group Policy to distribute computer programs by using the following methods:
Assigning Software You can assign a program distribution to users or computers. If you assign the program to a user, it is installed when the user logs on to the computer. When the user first runs the program, the installation is completed. If you assign the program to a computer, it is installed when the computer starts, and it is available to all users who log on to the computer. When a user first runs the program, the installation is completed.
Publishing Software
You can publish a program distribution to users. When the user logs on to the computer, the published program is displayed in the Add or Remove Programs dialog box, and it can be installed from there.
NEW QUESTION 11
Your company has an Active Directory forest that contains client computers that run Windows Vista andMicrosoft Windows XP.
You need to ensure that users are able to install approved application updates on their computers.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
- A. Set up Automatic Updates through Control Panel on the client computer
- B. Create a GPO and link it to the Domain Controllers organizational uni
- C. Configure the GPO to automatically search for updates on the Microsoft Update sit
- D. Create a GPO and link it to the domai
- E. Configure the GPO to direct the client computers to the Windows Server Update Services (WSUS) server for approved update
- F. Install the Windows Server Update Services (WSUS). Configure the server to search for new updates on the Interne
- G. Approve all required update
Answer: CD
Explanation:
http://technet.microsoft.com/en-us/library/cc720539%28v=ws.10%29.aspx
Configure Automatic Updates by Using Group Policy
When you configure the Group Policy settings for WSUS, use a Group Policy object (GPO)
linked to an Active Directory container appropriate for your environment.
NEW QUESTION 12
Your network contains an Active Directory forest. The forest contains two domains named contoso.com and eu.contoso.com. All domain controllers are DNS servers.
The domain controllers in contoso.com host the zone for contoso.com. The domain controllers in eu.contoso.com host the zone for eu.contoso.com. The DNS zone for contoso.com is configured as shown in the exhibit. (Click the Exhibit button.) 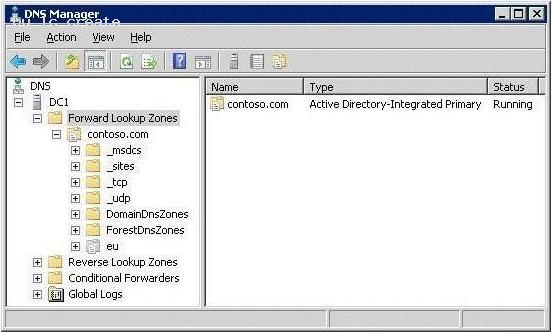
You need to ensure that all domain controllers in the forest host a writable copy of _msdsc.contoso.com.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
- A. Create a zone delegation record in the contoso.com zon
- B. Create a zone delegation record in the eu.contoso.com zon
- C. Create an Active Directory-integrated zone for _msdsc.contoso.co
- D. Create a secondary zone named _msdsc.contoso.com in eu.contoso.co
Answer: AC
Explanation:
Note that the question speaks of _msdSC, instead of _msdCS. Not sure if it means something, probably a typo.
NEW QUESTION 13
Your company has a main office and a branch office. You deploy a read-only domain controller (RODC) that runs Microsoft Windows Server 2008 to the branch office.
You need to ensure that users at the branch office are able to log on to the domain by using the RODC.
What should you do?
- A. Add another RODC to the branch offic
- B. Configure a new bridgehead server in the main offic
- C. Decrease the replication interval for all connection objects by using the Active Directory Sites and Services consol
- D. Configure the Password Replication Policy on the ROD
Answer: D
Explanation:
Answer: Configure the Password Replication Policy on the RODC.
http://technet.microsoft.com/en-us/library/cc754956%28v=ws.10%29.aspx RODC Frequently Asked Questions What new attributes support the RODC Password Replication Policy? Password Replication Policy is the mechanism for determining whether a user or computer's credentials are allowed to replicate from a writable domain controller to an RODC. The Password Replication Policy is always set on a writable domain controller running Windows Server 2008. What operations fail if the WAN is offline, but the RODC is online in the branch office? If the RODC cannot connect to a writable domain controller running Windows Server 2008 in the hub, the following branch office operations fail: Password changes Attempts to join a computer to a domain Computer rename Authentication attempts for accounts whose credentials are not cached on the RODC Group Policy updates that an administrator might attempt by running the gpupdate /force command What operations succeed if the WAN is offline, but the RODC is online in the branch office? If the RODC cannot connect to a writable domain controller running Windows Server 2008 in the hub, the following branch office operations succeed: Authentication and logon attempts, if the credentials for the resource and the requester are already cached, Local RODC server administration performed by a delegated RODC server administrator.
NEW QUESTION 14
Your network contains an Active Directory-integrated DNS zone named contoso.com.
You discover that the zone includes DNS records for computers that were removed from the network.
You need to ensure that the DNS records are deleted automatically from the zone.
What should you do?
- A. From DNS Manager, set the aging propertie
- B. Create a scheduled task that runs dnslint.exe /v /d contoso.co
- C. From DNS Manager, modify the refresh interval of the start of authority (SOA) recor
- D. Create a scheduled task that runs ipconfig.exe /flushdn
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/cc753217.aspx
Set Aging and Scavenging Properties for the DNS Server
The DNS Server service supports aging and scavenging features. These features are provided as a mechanism for performing cleanup and removal of stale resource records, which can accumulate in zone data over time. You can use this procedure to set the default aging and scavenging properties for the zones on a server.
To set aging and scavenging properties for the DNS server using the Windows interface
1. Open DNS Manager.
2. In the console tree, right-click the applicable DNS server, and then click Set Aging/Scavenging for all zones.
3. Select the Scavenge stale resource records check box.
4. Modify other aging and scavenging properties as needed.
NEW QUESTION 15
You have an Active Directory snapshot.
You need to view the contents of the organizational units (OUs) in the snapshot.
Which tools should you run?
- A. explorer.exe, netdom.exe, and dsa.msc
- B. ntdsutil.exe, dsamain.exe, and dsa.msc
- C. wbadmin.msc, dsamain.exe, and netdom.exe
- D. wbadmin.msc, ntdsutil.exe, and explorer.exe
Answer: B
NEW QUESTION 16
Your network contains an Active Directory forest. The forest schema contains a custom attribute for user objects.
You need to generate a file that contains the last logon time and the custom attribute values for each user in the forest.
What should you use?
- A. the Get-ADUser cmdlet
- B. the Export-CSV cmdlet
- C. the Net User command
- D. the Dsquery User tool
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/cc771865.aspx
Adds or modifies user accounts, or displays user account information.
DSQUERY
Explanation 1:
http://technet.microsoft.com/en-us/library/cc754232.aspx
Parameters {<StartNode> | forestroot | domainroot}
Specifies the node in the console tree where the search starts. You can specify the forest root (forestroot), domain root (domainroot), or distinguished name of a node as the start node <StartNode>. If you specify forestroot, AD DS searches by using the global catalog.
-attr {<AttributeList> | *} Specifies that the semicolon separated LDAP display names included in <AttributeList> for each entry in the result set. If you specify the value of this parameter as a wildcard character (*), this parameter displays all attributes that are present on the object in the result set. In addition, if you specify a *, this parameter uses the default output format (a list), regardless of whether you specify the -l parameter. The default <AttributeList> is a distinguished name.
Explanation 2:
http://social.technet.microsoft.com/Forums/eu/winserverDS/thread/dda5fcd6-1a10-4d47-9379-02ca38aaa5b
Give an example of how to find a user with certain attributes using Dsquery. Note that it uses domainroot as the startnode, instead of forestroot what we need.
Explanation 3:
http://social.technet.microsoft.com/Forums/en-US/winservergen/thread/c6fc3826-78e1-48fd-ab6f-690378e0f787/
List all last login times for all users, regardless of whether they are disabled.
dsquery * -filter "(&(objectCategory=user)(objectClass=user))" -limit 0 -attr givenName sn sAMAccountName
lastLogon>>c:last_logon_for_all.txt
NEW QUESTION 17
Your network contains an Active Directory domain named contoso.com. The network contains 10 subnets.
You install a Web server on three different subnets. Each Web server hosts a web application accessed by using an FQDN of webl.contoso.com.
For webl.contoso.com, you create three host (A) records that each points to one of the Web servers.
You need to configure the DNS settings to meet the following requirements:
. Users who access webl.contoso.com from a subnet that contains one of the Web servers must connect to the server on their local subnet.
. When users connect from a subnet that does not contain a Web server hosting the web application, the connections must be balanced between the three Web servers.
Which two settings should you modify? (To answer, select the two appropriate settings in the answer area.) 
Answer:
Explanation: 
NEW QUESTION 18
Your company has a main office and a branch office. The main office contains two domain controllers.
You create an Active Directory site named BranchOfficeSite.
You deploy a domain controller in the branch office, and then add the domain controller to the BranchOfficeSite site.
You discover that users in the branch office are randomly authenticated by either the domain controller in the branch office or the domain controllers in the main office.
You need to ensure that the users in the branch office always attempt to authenticate to the domain controller in the branch office first.
What should you do?
- A. Create organizational units (OUs).
- B. Create Active Directory subnet object
- C. Modify the slow link detection threshol
- D. Modify the Location attribute of the computer object
Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/cc754697.aspx Understanding Sites, Subnets, and Site Links Sites overview Sites in AD DS represent the physical structure, or topology, of your network. AD DS uses network topology information, which is stored in the directory as site, subnet, and site link objects, to build the most efficient replication topology. The replication topology itself consists of the set of connection objects that enable inbound replication from a source domain controller to the destination domain controller that stores the connection object. The Knowledge Consistency Checker (KCC) creates these connection objects automatically on each domain controller.
Associating sites and subnets A subnet object in AD DS groups neighboring computers in much the same way that postal codes group neighboring postal addresses. By associating a site with one or more subnets, you assign a set of IP addresses to the site. Note The term "subnet" in AD DS does not have the strict networking definition of the set of all addresses behind a single router. The only requirement for an AD DS subnet is that the address prefix conforms to the IP version 4 (IPv4) or IP version 6 (IPv6) format. When you add the Active Directory Domain Services server role to create the first domain controller in a forest, a default site (Default-First-Site-Name) is created in AD DS. As long as this site is the only site in the directory, all domain controllers that you add to the forest are assigned to this site. However, if your forest will have multiple sites, you must create subnets that assign IP addresses to Default-First-Site-Name as well as to all additional sites.
Locating domain controllers by site Domain controllers register service (SRV) resource records in Domain Name System (DNS) that identify their site names. Domain controllers also register host (A) resource records in DNS that identify their IP addresses. When a client requests a domain controller, it provides its site name to DNS. DNS uses the site name to locate a domain controller in that site (or in the next closest site to the client). DNS then provides the IP address of the domain controller to the client for the purpose of connecting to the domain controller. For this reason, it is important to ensure that the IP address that you assign to a domain controller maps to a subnet that is associated with the site of the respective server object. Otherwise, when a client requests a domain controller, the IP address that is returned might be the IP address of a domain controller in a distant site. When a client connects to a distant site, the result can be slow performance and unnecessary traffic on expensive WAN links.
Recommend!! Get the Full 70-640 dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/70-640-exam-dumps.html (New 631 Q&As Version)